Expand capabilities of IdPs to ensure security of SaaS
Identity Threat Detection and Response (ITDR) solutions like Okta or Duo excel in capturing threats to on-premise infrastructure, IaaS, and PaaS. But what about SaaS? Do you have visibility into which SaaS applications have MFA disabled and may be bypassing SSO? Businesses continue to use more SaaS products and an important consideration to secure them emerges—the need for specialized tools to address the unique challenges of SaaS environments.
Traditional ITDR Solutions versus SaaS-aware ITDR
Traditional ITDR solutions are highly effective, and their capabilities can be further enhanced with the addition of SaaS-specific tools. For example, traditional ITDR solutions do not enumerate roles and privileges defined within the SaaS applications giving only a partial view of whether a user is provisioned to an application. Whereas ITDR for SaaS—or as we are calling it, SaaS-Aware ITDR—provides the insights and context needed for SaaS application events and posture settings. Identity-centric SaaS solutions uniquely correlate and detect SaaS threats by combining user behavior analysis with context from posture. They complement traditional ITDR solutions, providing a comprehensive, end-to-end threat detection and response specifically for SaaS applications. They facilitate policy-driven automated actions to counter account takeovers and privilege escalation attempts.
Why identity-centric analysis is essential for SaaS security
Human and non-human identities have SaaS security implications at every step of their SaaS usage journey—from creation, role assignment, and privilege updates, to interactions with the SaaS estate, potentially anomalous behavior, and off-boarding. There is a continuous stream of signals that must be processed and addressed. This creates a significant amount of noise for already strapped Security Operations Center (SOC) teams that might miss critical signals leading to data compromises.
On top of that, SaaS breaches continue to rise with dramatic impacts. The connected nature of SaaS apps makes taking advantage of misconfigured policies easy. Take the Snowflake breach for example, a single credential with MFA disabled resulted in the exfiltration of potentially hundreds of companies. This trend will likely continue as threat actors such as UNC3944/Scattered Spider further exploit the complexities of SaaS security, prompting even the NSA to develop new guidance for securing applications.
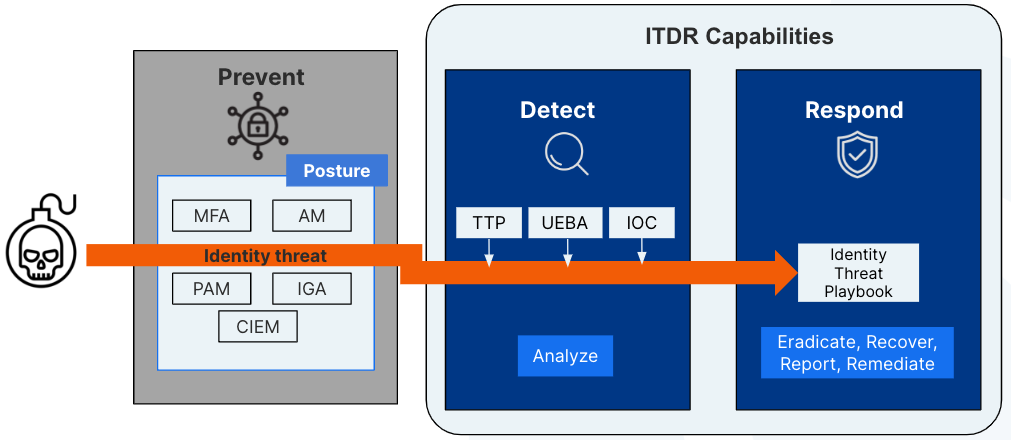
In a world where there are too many security tools, too much noise, and fatigued security teams, having a unified location for security posture, identities, and threat detection is critical to gain context of where, what, and with whom SaaS threats exist. After all, SaaS-aware ITDR delivers a clear security signal for faster response times. By focusing on identities, SaaS-specific tools effectively pinpoint suspicious activities that signal potential security breaches. This represents a more comprehensive approach to ITDR security methods used widely today.
Successfully building threat detections for SaaS applications requires a multifaceted approach—one that combines advanced detection capabilities with comprehensive insights across your SaaS estate and integrates both posture and identity information. This approach eliminates entire classes of SaaS issues, enhances threat detection accuracy, and reduces the number of alerts to enable busy SOC teams with end-to-end context. SaaS-Aware ITDR provides a comprehensive view of SaaS threats, reduces alert fatigue, and enables actionable responses to secure your SaaS applications.
The mechanics of SaaS-aware identity-centric threat detection
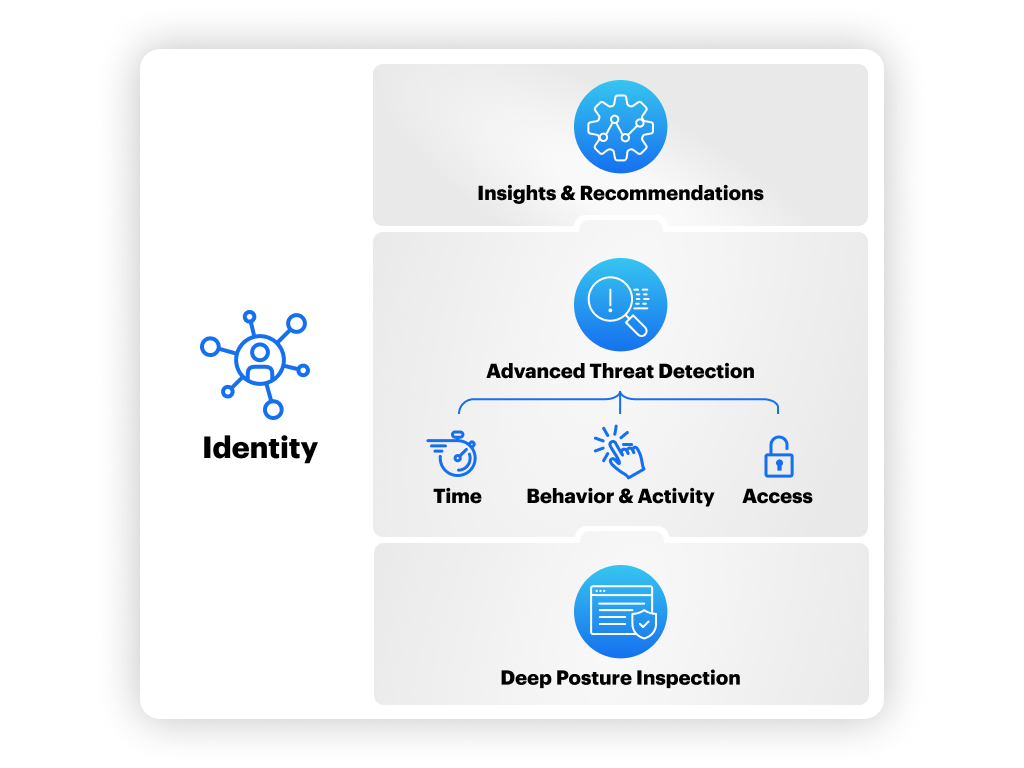
To be SaaS-aware for ITDR, SOC teams must align security posture with threat detection and overall SaaS expertise. Specifically, this foundation gives security teams the insight they need to have greater visibility into SaaS threats and take proactive steps to remediate them. To be SaaS aware, you need:
Posture Management: Security posture lies at the base of an effective SaaS security strategy. This involves continuous monitoring and assessment of identity configurations, permissions, and access controls. By maintaining a strong security posture, organizations can preemptively address vulnerabilities that attackers could exploit.
Anomaly Detection: Identity-centric analysis excels at detecting anomalies in user behavior. For instance, if a user suddenly accesses sensitive data they don’t normally interact with, it could indicate a compromised account. By continuously monitoring and analyzing identity-related activities, organizations can detect and respond to such anomalies in real-time and minimize potential damage.
Contextual Insights: Traditional security tools often generate massive amounts of alerts with little context, leading to alert fatigue and missed threats. An identity-centric approach, however, provides contextual insights by correlating events with specific user behaviors and identity attributes. This helps security teams quickly identify and prioritize genuine threats.
AppOmni provides enhanced SaaS-Aware Identity Threat Detection and Response (SITDR)
AppOmni’s SaaS-awareness complements ITDR capabilities by putting identity at the forefront of SaaS security. With full lifecycle visibility to identities in the context of SaaS, SaaS events and logs, and user behavior in SaaS, we detect SaaS-specific threats that originate from misconfigured permissions, anomalous user behavior, compromised credentials, and more. As part of responding to adverse events, we partner with IdPs to share signals based on observed behavior to force stepped-up authentication or dynamic re-authentication of users.
By leveraging the industry’s largest dataset, which monitors over 1.5 billion events daily, we provide unparalleled visibility and a comprehensive understanding of user actions and access patterns. Our SaaS-specific approach offers advanced threat detection and enhanced user and entity behavior analytics (UEBA), ensuring precise mapping and monitoring of roles, permissions, and configuration drift. This holistic perspective supplements traditional ITDR solutions, providing the awareness security teams need to combat SaaS threats. Here’s how we do it:
Identity and Threat Detection. By continuously monitoring identities, posture, and threats, AppOmni creates a comprehensive and actionable view of security, making security teams SaaS-aware. Starting with deep posture insights, AppOmni builds upon this foundation with advanced threat detection, providing prioritized recommendations and responses to secure SaaS environments. By focusing on both human and non-human identities throughout, AppOmni offers customers clear insights into who did what and where, effectively providing an audit trail that was previously lacking.
Response. AppOmni excels through seamless integrations and intelligent tagging. ‘We work, where you work’. By integrating with leading Identity Providers (IdPs) such as EntraID and Duo, AppOmni ensures that threat alerts trigger automated responses, streamlining the remediation process. Additionally, AppOmni integrates with Security Orchestration, Automation, and Response (SOAR) platforms, Security Information and Event Management (SIEM) systems, and IT Service Management (ITSM) tools, enabling security teams to manage incidents within their existing workflows. This comprehensive approach not only accelerates threat mitigation, but also ensures that responses are precise and effective, reducing the overall risk to the organization’s SaaS ecosystem.
The Future of SaaS Security
As business reliance on a wide array of SaaS applications continues to grow, adopting an identity-centric view for threat detection is imperative. Implementing advanced ITDR capabilities helps organizations protect their critical applications and sensitive data from increasingly sophisticated cyber threats. Identity is at the heart of an effective SaaS security, and focusing on it allows for a more accurate, efficient, and comprehensive threat detection strategy.
Want to start learning more about how SaaS threat detection is different? Check out our free Event Maturity Matrix highlighting the difference in log schemas.
Additional Resources
-

Zoom Breach at Federal Reserve Shows the Need for SaaS Security
A SaaS security misconfiguration led to a high-profile Zoom bombing, preventing the Federal Governor from delivering his remarks at a virtual event.
-
Zero Trust’s Weak Spot: SaaS Apps Aren’t Playing By The Same Rules
Organizations that rely solely on ZTNA or similar network-focused defenses often mistakenly believe their SaaS applications are protected.
-
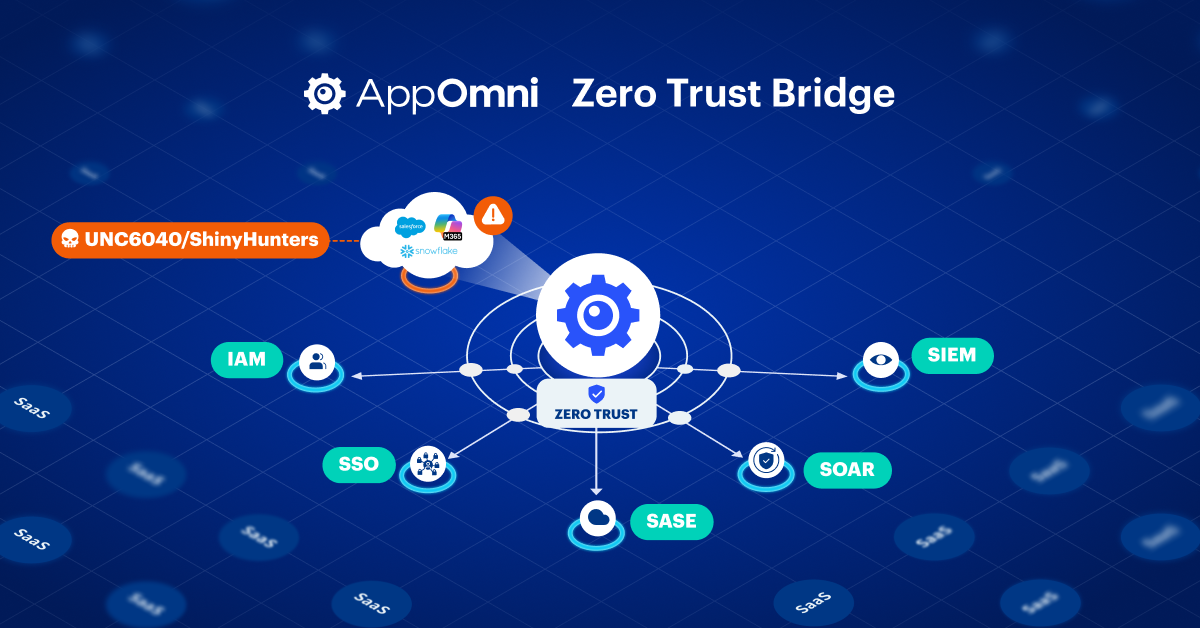
Zero Trust Needs a Bridge: How to Unlock Shared Signals for SaaS Now
Zero Trust Bridge activates shared signals in SaaS, boosting real-time risk detection with AppOmni.