Imagine being a CISO, head of IT, or security admin and feeling certain your SaaS environments are locked down. You’ve invested in the right tools, checked all the boxes, and your team is confident (maybe even proud) of your SaaS security program. But then, you discover your organization is among the 75% that suffered a SaaS security incident or breach in the past year. That sense of control suddenly feels like a mirage. You’re left asking: “How did this happen, and why didn’t we see it coming?”
That’s not just a hypothetical scenario. According to AppOmni’s 2025 State of SaaS Security Report:
- 75% of organizations suffered a SaaS incident or breach in the past 12 months
- 91% say they’re confident in their SaaS security posture
- SaaS incidents increased 33% year-over-year
For many teams, this isn’t just confusing; it’s demoralizing. The disconnect between perception and reality creates frustration, self-doubt, and pressure from stakeholders who expect better.
Why is the confidence gap so wide, and what’s driving the surge in SaaS security incidents?
In this deep dive, we’ll break down the reasons for this confidence gap, why it persists even among mature enterprises, and what the data reveals about the real-world consequences of relying too heavily on surface-level security signals. If you’re searching for answers about why SaaS incidents are rising despite bigger budgets and better dashboards, you’re not alone. The answers are as instructive for CISOs as they are for business leaders and app owners, especially as SaaS becomes the operating backbone for nearly every modern company.

High confidence, higher SaaS security incident rates
According to AppOmni’s 2025 State of SaaS Security Report, 91% of organizations say they’re confident in their SaaS security posture. Yet two-thirds suffered a SaaS-related incident or breach in the past 12 months (a percentage that’s increasing dramatically year-over-year). There’s a big disconnect here between how people feel about their security and what’s actually happening.
So, what’s fueling this disconnect?
1. Visibility alone doesn’t equal complete SaaS security
Many organizations conflate visibility with real security. Nearly 89% of those breached believed they had “appropriate visibility” at the time—only to learn too late that visibility without continuous enforcement creates an illusion of control.
While dashboards and logs provide valuable insights, they can also add to this illusion of safety, especially if they aren’t paired with enforcement and continuous validation. The report found that nearly half of companies (43%) have implemented some form of continuous or near real-time SaaS oversight. That means most (52%) are still relying on point-in-time audits or static reviews, which leaves room for configuration drift, subtle access changes, and misconfigurations that can open the door to attackers.
2. Teams are overly trusting of SaaS vendors and legacy approaches
Confidence in SaaS security is often rooted in trust—primarily, trust in SaaS vendors themselves. In fact, 53% of confident respondents say their sense of security is based on the strength of their vendors’ controls. But this ignores the realities of the shared responsibility model. Once data is in the hands of a third-party provider, oversight becomes more complex and indirect. Without routine, independent verification, teams may be missing silent risks.
3. Decentralized ownership creates fragmented accountability
Another key finding: Only 16% of organizations assign SaaS security solely to their security teams, while 43% leave it to business units. This fragmented approach can lead to unclear accountability, inconsistent controls, and security gaps that aren’t anyone’s explicit responsibility.
4. Static SaaS security measures don’t work well in dynamic environments
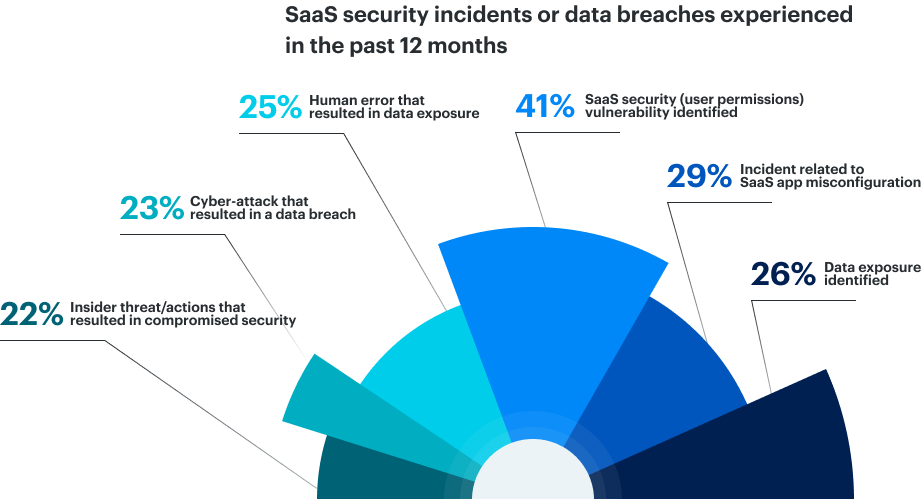
SaaS environments are anything but static. New apps are deployed, user roles change, integrations proliferate, and feature updates are rolled out—all at a pace traditional security reviews can’t keep up with. The data shows that 41% of SaaS incidents involved user permissions, and 29% were caused by misconfigurations. These are not sophisticated, zero-day exploits; they’re basic hygiene issues that slip through the cracks when monitoring isn’t continuous and enforcement isn’t proactive.
5. People settle for “good enough” (which isn’t actually good enough)
There’s also a psychological angle: As SaaS ecosystems expand and workloads shift to the cloud, teams are stretched thin. With competing security priorities, it’s tempting to assume things are “good enough,” especially when previous audits or vendor attestations seemed solid. But as the data shows, hope is not a strategy.
The real-world impact of SaaS security incidents
The fallout from SaaS incidents is real:
- 57% of respondents cited data breaches or loss of intellectual property as their top concern.
- 37% worried about customer data being compromised.
- More than a quarter (28%) pointed to accidental data exposure as a pressing risk.

On top of this, the average cost of a data breach is staggering: IBM’s findings peg it at $4.45 million, and even small-scale incidents can cost $165 per record—underscoring that risk scales, not shrinks, with impact
Every incident that flies under the radar or is discovered too late erodes customer trust, invites regulatory scrutiny, and can have a direct financial and reputational impact.
Practical next steps to close the SaaS security confidence gap
So, how can organizations break out of the confidence trap and move toward true SaaS resilience? The research points to several clear imperatives.
- Continuous monitoring is non-negotiable: Replace periodic audits with always-on monitoring that detects posture drift, permission changes, and risky behaviors as they happen, not months later.
- Clarify ownership: Define and document clear SaaS security responsibilities across business units and security teams. It can be everyone’s job, but make roles and expectations explicit.
- Verify, don’t assume: Routine, independent validation of SaaS configurations and integrations is essential. Don’t rely solely on vendor assurances, defaults, or legacy tools.
- Prioritize what matters: Not all apps are equal. Use the 80/20 rule to focus continuous oversight on the small set of applications that house most of your sensitive data and present the greatest risk.
- Leverage the right tools: Manual processes can’t keep up with the speed and scale of modern SaaS. Look for tools and platforms that deliver contextual, prioritized insights and automate routine checks without adding more work for already stretched teams.
Closing thoughts
The rise in SaaS incidents (despite high confidence) should be a wake-up call, not a cause for despair. With the right mindset, ownership, and technology, organizations can move from reactive to proactive, and from an illusion of control to true SaaS resilience.
Want to see how your SaaS security posture stacks up—and how to start closing the confidence gap? Download the full 2025 State of SaaS Security report for more insights, benchmarks, and actionable recommendations.
