Shadow IT Definition
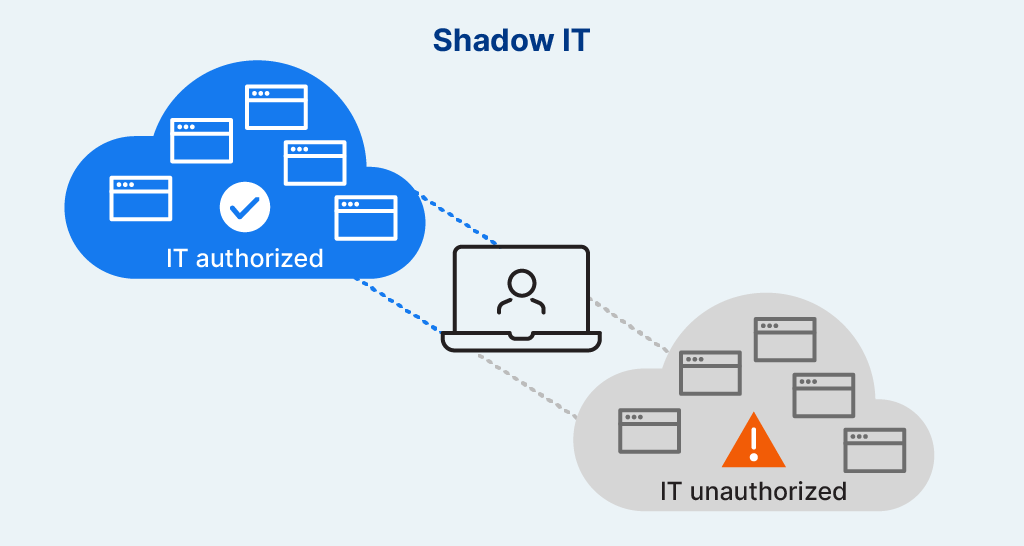
Shadow IT refers to hardware, software, or cloud services used within an organization without the knowledge, approval, or oversight of the IT or security department.
This can include things like:
• Employees using personal devices for work tasks
• Teams signing up for unsanctioned SaaS tools (e.g., using Google Drive or Trello without IT approval)
• Developers using unauthorized APIs or open-source code libraries
While shadow IT can improve productivity and agility, it poses security risks, such as data leaks, compliance violations, and vulnerabilities, because these tools are not subject to the organization’s security controls or monitoring.
Shadow IT FAQs
What is Shadow IT?
Shadow IT is when employees use apps, software, or devices for work without getting approval from their company’s IT team. This can be things like using personal email, cloud storage, or tools that haven’t been officially approved. While it can make work faster or easier, it can also create security risks because the IT team isn’t aware of it.
What is Shadow IT Discovery?
Shadow IT discovery is the process of identifying and monitoring unauthorized or unsanctioned technology, such as apps, cloud services, or devices, used within an organization without the knowledge of the IT or security team.
By uncovering shadow IT, organizations gain visibility into potential security risks, data exposure, and compliance gaps. Discovery tools often use network traffic analysis, CASBs, or endpoint monitoring to detect unapproved usage.
What is Shadow IT Policy?
A shadow IT policy is a set of rules and guidelines created by an organization to manage and control the use of unauthorized technology, such as apps, cloud services, or devices, that are not approved by the IT department.
This policy helps reduce security and compliance risks by clearly outlining what tools are allowed, how new tools can be requested, and what the consequences are for using unapproved technology. It also supports transparency between teams and encourages safer, more efficient technology use across the organization.
What are the Shadow IT Risks?
As with everything in the SaaS security world, there are risks of shadow IT that need to be considered.
Security Vulnerabilities. Unauthorized tools may lack proper security measures, leaving sensitive data exposed to breaches, malware, or hacking.
Data Loss & Leakage. Employees may store or share company data on unsanctioned platforms, increasing the risk of accidental or unauthorized exposure.
Compliance Violations. Using unapproved apps can lead to violations of regulations like GDPR, HIPAA, or SOC 2, resulting in legal or financial penalties.
Lack of Visibility. IT teams can’t protect what they can’t see. Shadow IT makes it harder to monitor, manage, or respond to threats.
Inconsistent User Access Controls. Unmanaged tools may not follow corporate identity and access protocols, increasing the chance of improper access to sensitive systems.
Duplication of Tools & Costs. Teams may purchase overlapping or redundant tools, leading to wasted budget and inefficiency.
Disruption to Incident Response. If a security incident occurs in an app IT isn’t aware of, it can slow down containment and recovery.
How to Detect Shadow IT
Shadow IT detection is the first step in reducing the risk it poses. Because unsanctioned tools often fly under the radar, detection requires visibility into how employees interact with cloud services and applications.
Common methods include:
- Network Traffic Analysis: Monitoring outbound traffic can reveal which apps are being accessed outside of approved systems.
- Cloud Access Security Brokers (CASBs): These tools sit between users and cloud services to uncover and control unauthorized usage.
- Endpoint Monitoring: Security software installed on devices can flag suspicious activity, like logins to unapproved tools or data uploads to external platforms.
- SSPM Tools: SaaS Security Posture Management (SSPM) tools help detect risky SaaS connections and misconfigurations, especially in large or fast-growing cloud environments.
Regular audits and monitoring are essential to maintain visibility over time, especially as teams experiment with new SaaS tools or bring in vendors.
How to Manage Shadow IT
Managing shadow IT involves a mix of visibility, policy, and cultural alignment. Once you’ve identified unauthorized tools, the goal isn’t always to shut them down. Instead, it’s to understand why they were adopted and whether they can be safely integrated or replaced.
Key steps to manage shadow IT:
- Inventory and Risk Assess. Evaluate all discovered tools for security, compliance, and business value.
- Implement Access Controls. Use identity and access management (IAM) systems to centralize login processes and reduce unmonitored app usage.
- Create an App Approval Process. Offer a simple and transparent process for teams to request new tools, which can reduce the temptation to bypass IT.
- Educate Employees. Train staff on the risks of using unapproved software and share the benefits of going through official channels.
- Monitor Continuously. Shadow IT is ongoing. Maintain real-time monitoring to stay ahead of new risks.
How to Prevent Shadow IT
Prevention focuses on creating an environment where employees don’t feel the need to go outside IT systems to get their work done. This involves a combination of enablement, trust, and control.
- Offer Approved Alternatives. Ensure your teams have access to secure, user-friendly tools that meet their needs.
- Foster Collaboration with IT. Encourage departments to involve IT early when evaluating new technologies.
- Set Clear Policies. Define what tools are allowed, how new ones can be requested, and the risks associated with bypassing IT.
- Automate Governance. Use tools like CASBs and IAM to automatically flag or block access to risky or unapproved tools.
- Build a Security-First Culture. Empower employees to take ownership of security by including them in the conversation, not just enforcing rules.
By making it easier to do the right thing, organizations can minimize shadow IT without stifling innovation.
Shadow IT vs Insider Threat
| Aspect | Shadow IT | Insider Threat |
| Definition | Use of unauthorized technology (apps, devices, or services) without IT approval. | Risk posed by insiders (employees, contractors) who intentionally or accidentally cause harm. |
| Intent | Usually not malicious. Done to improve productivity or solve problems quickly. | Can be malicious (e.g., sabotage, theft) or accidental (e.g., mistakes, phishing). |
| Examples | Using unapproved cloud storage or communication apps. | An employee stealing data or accidentally clicking a phishing email. |
| Risk Type | Creates security blind spots and control gaps. | Leads to data breaches, intellectual property loss, or operational damage. |
| Detection Challenges | Difficult to detect because IT is unaware of the tool or service. | Hard to detect as insiders have legitimate access and may appear normal. |
| Mitigation Focus | Shadow IT discovery, policies, employee education, and approved alternatives. | User behavior monitoring, access controls, insider threat programs, and training. |
Benefits of Shadow IT
While shadow IT is often viewed as a security risk, it can also bring some positive outcomes to organizations when managed properly or understood in context:
Increased Agility and Innovation. Employees can quickly adopt new tools and technologies to solve problems or improve workflows without waiting for lengthy IT approval processes. This can accelerate innovation and responsiveness, especially in fast-paced environments.
Enhanced Productivity. Teams often turn to shadow IT solutions because they offer features or usability that official tools lack. By using software they prefer, employees may work more efficiently and collaboratively.
Real-World Testing of New Technologies. Shadow IT can act as a testing ground where emerging apps or platforms prove their value before IT departments formally evaluate and approve them for wider use.
User-Driven Technology Adoption Insights. Shadow IT reveals unmet needs within an organization’s existing technology stack. Understanding what tools employees are using unofficially can help IT tailor future investments to better support business goals.
Cost Savings (Short-Term). In some cases, shadow IT solutions may be less expensive or more accessible than enterprise alternatives, providing quick wins without large upfront costs.
Shadow IT Challenges
While shadow IT can bring benefits, it also introduces several significant challenges that organizations need to address:
Security Risks. Unapproved applications and devices often lack proper security controls, increasing the chances of data breaches, malware infections, and unauthorized access.
Compliance Issues. Shadow IT can lead to violations of industry regulations (such as GDPR, HIPAA, or PCI DSS) because data may be stored or processed in ways that don’t meet compliance standards.
Lack of Visibility and Control. IT teams are often unaware of shadow IT tools, making it difficult to monitor usage, enforce policies, or respond quickly to incidents involving these systems.
Data Loss and Leakage. Without oversight, sensitive company information may be shared or stored insecurely, increasing the risk of accidental exposure or intentional theft.
Integration Problems. Unauthorized tools may not integrate well with official systems, causing inefficiencies, data silos, and inconsistent workflows.
Increased Costs. Shadow IT can lead to redundant software subscriptions or unexpected expenses if multiple teams purchase similar tools independently.
Incident Response Challenges. When security incidents involve shadow IT, investigations and remediation are often slower because the IT and security teams lack full context or control.
How Does AppOmni Help Manage Shadow IT?
Shadow IT presents significant security risks by introducing unmonitored SaaS applications and cloud services into an organization’s environment. AppOmni helps organizations gain full visibility and control over their SaaS landscape, including unauthorized or unsanctioned apps that traditional security tools might miss.
By continuously monitoring SaaS configurations and user activity across all cloud services, AppOmni enables security teams to detect shadow IT early, assess potential risks, and enforce governance policies. This proactive approach reduces blind spots, helps maintain compliance, and minimizes the chance of data exposure caused by shadow IT.