Zero Trust Posture Management
Closing the loop on Zero Trust™
Eliminate implicit trust inside SaaS at the application level
Zero Trust (ZT) architectures operate on the principle that trust should never be assumed implicitly, regardless of the network location or asset ownership. Today, enterprise assets are not confined to a controlled network but rather spread across cloud services, remote offices, and mobile workers.
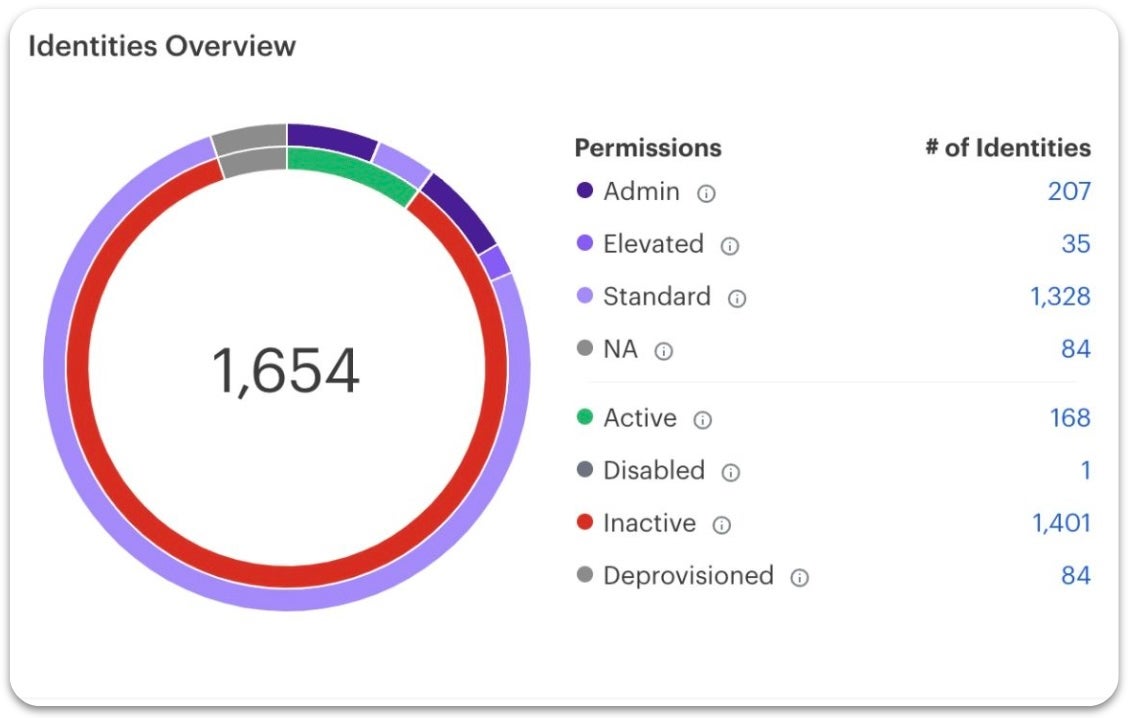
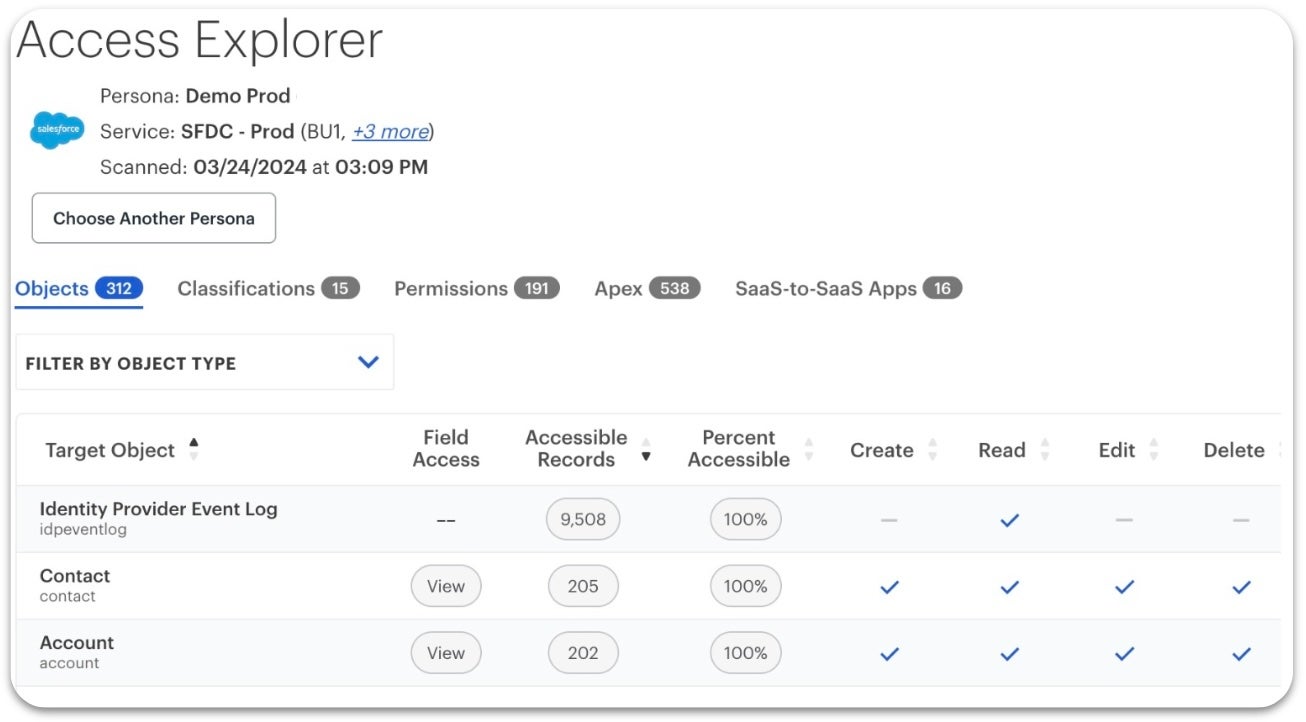
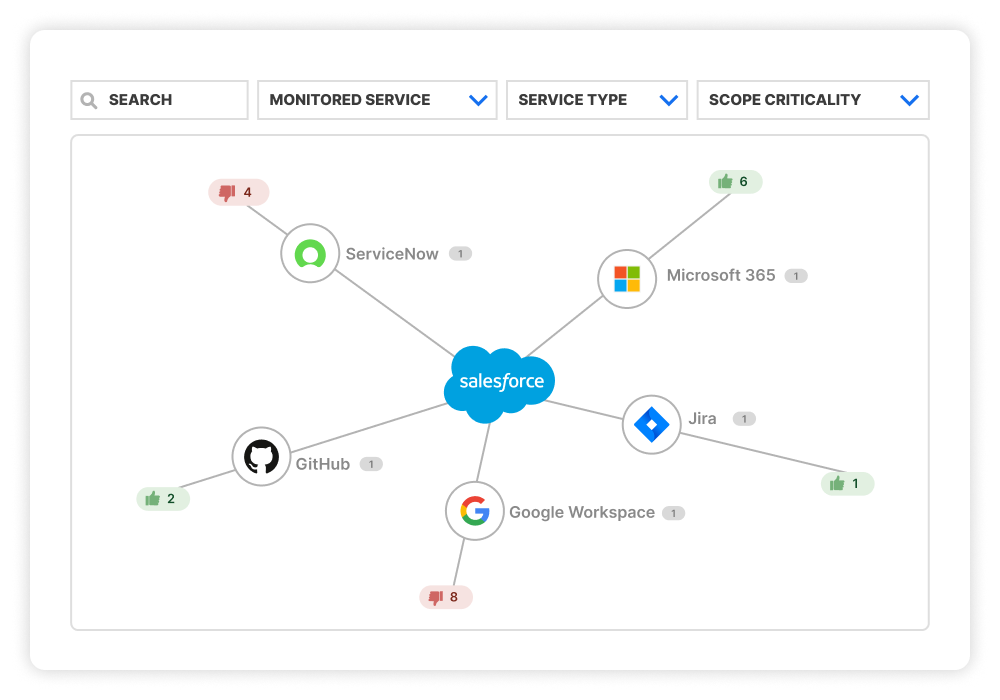
AppOmni extends Zero Trust beyond your network and infrastructure levels into SaaS applications with Zero Trust Posture Management (ZTPM™). It closes critical gaps at the application level, such as misconfigurations in access controls, unchecked privileges, data leaks, or overlooked third-party integrations.

End-to-end Zero Trust Security

Dynamic Policy Enforcement

Strong Identity and Access Protection
Extend your zero trust architecture to SaaS apps & data
Zero Trust (ZT) is an effective framework that secures today’s distributed organizations by leveraging continuous verification and the principle of “never trust, always verify” — regardless of network boundaries. Ensure Zero Trust doesn’t stop at the network edge.
How AppOmni bridges a critical gap in network-centric Zero Trust (ZT) architectures
See AppOmni in Action
AppOmni’s agentless architecture delivers continuous SaaS and AI security monitoring with timely insights and remediation guidelines to help you prevent data breaches. The platform provides a central control point for all managed SaaS applications in your organization.
Latest Resources
-
Identity Crisis: Why SaaS Attacks Are Bypassing Your Best Defenses
To help build a solid foundation for AI adoption, IM firms should source high-quality data, use modern data cloud/hybrid infrastructure, and adopt robust data governance principles.
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-
Artificial Intelligence security vulnerability uncovered
Aaron Costello with AppOmni tells Good Morning Cleveland anchor Mike Brookbank more about the flaw in the ServiceNow platform.