Compliance for SaaS
Make SaaS compliance easy. Simplify, secure, and sustain standards.
CHALLENGE
SaaS applications rely on external integrations, access policies, and configurations which if set up incorrectly, can violate security and privacy laws. From HIPAA, Sarbanes-Oxley to SOC II, AppOmni ensures your SaaS applications align and comply with regulatory SaaS compliance standards.
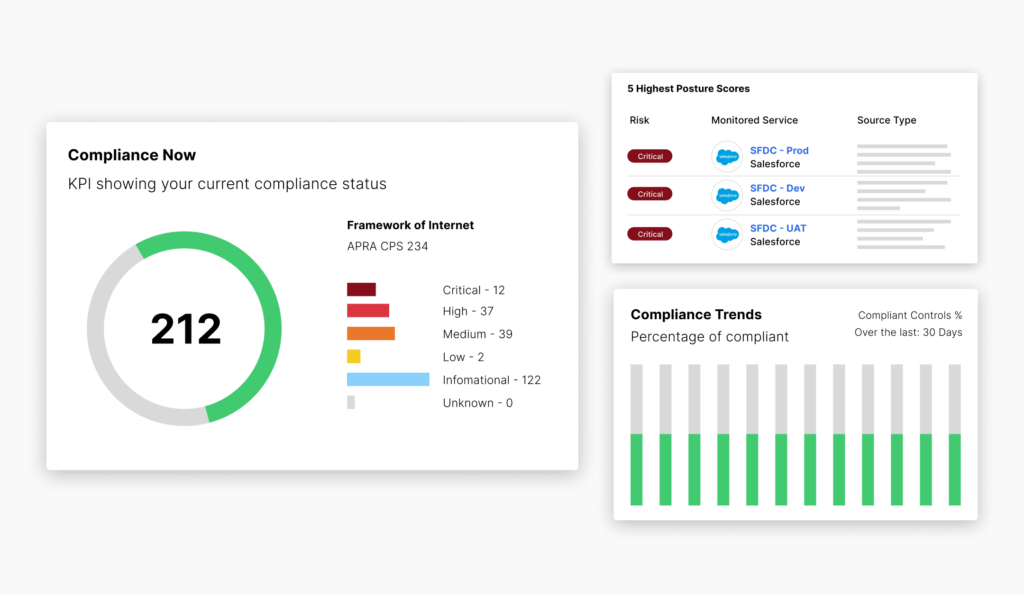
How AppOmni Compliance Secures SaaS
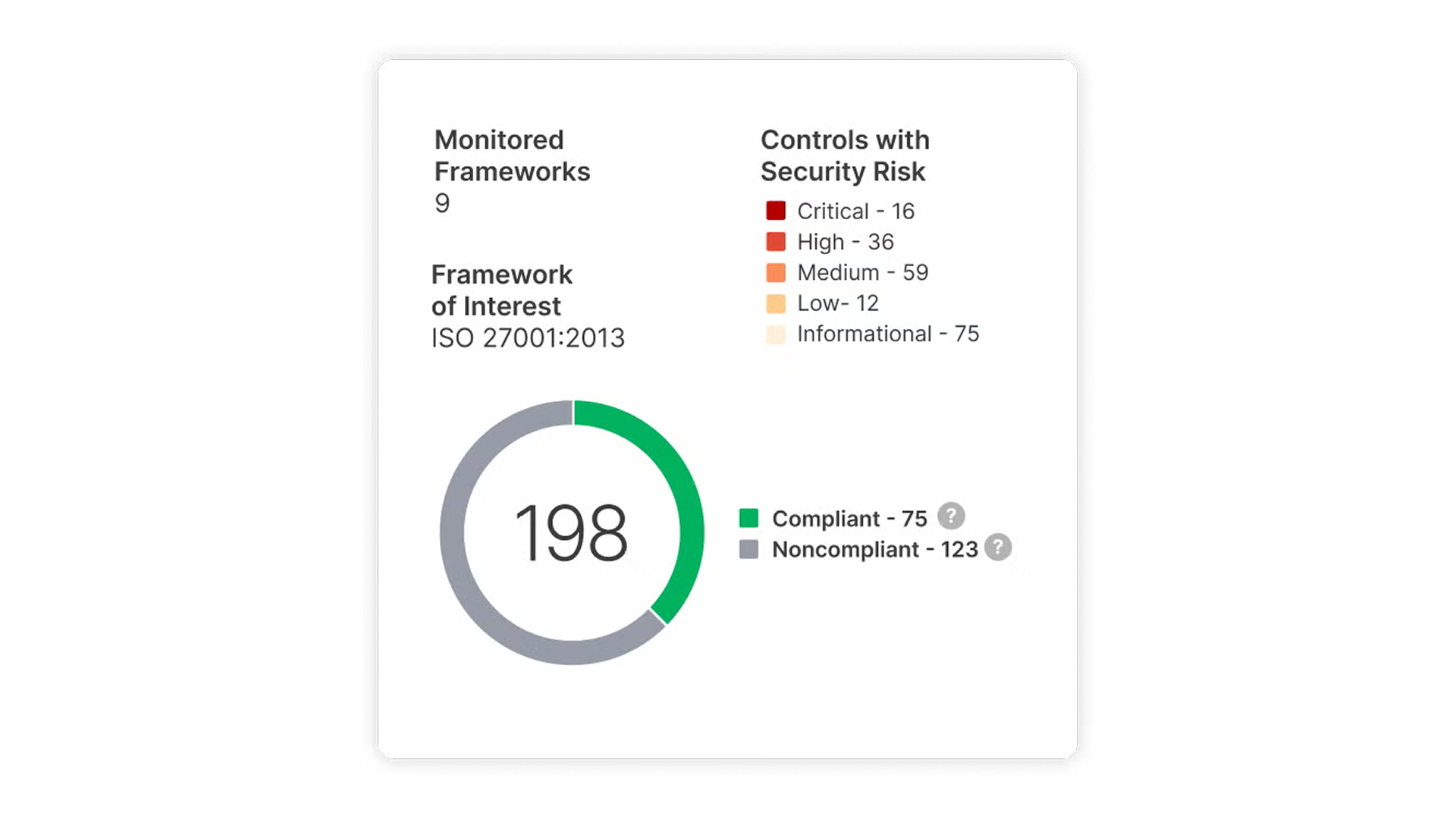
AppOmni enforces SaaS security controls, monitors for policy drift, and delivers audit-ready evidence to support compliance with standards like ISO, SOC 2, and HIPAA.
Detect SaaS Shadow IT
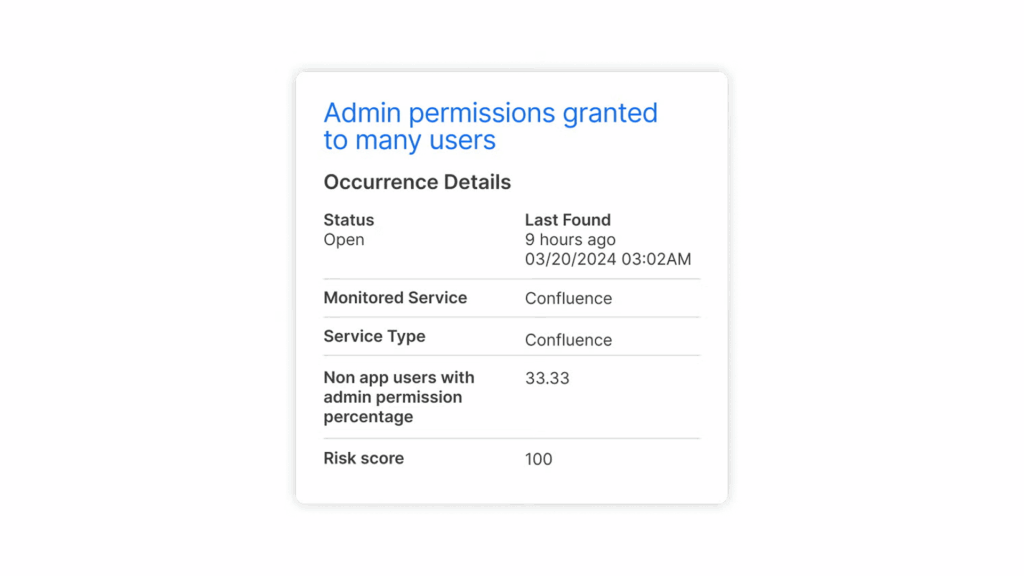
Detect unauthorized applications connected to your managed SaaS applications and gain insights into risks and incorrect user permissions.
Automation
Reduce tedious app by app validation of SaaS compliance checks. Use real-time insights and alerts to prevent potential violations and enhance overall SaaS security posture.
Identify, Prioritize & Remediate Misconfigurations
Utilize policy baselines or custom frameworks to alert on non-compliance. Ensure compliance using guided remediation steps.
Key Features
Supporting Federal SaaS Security and Resilience
AppOmni has been granted Federal Risk and Authorization Management Program (FedRAMP) Moderate Authority to Operate (ATO). Agencies can confidently adopt AppOmni’s SaaS Security Platform to secure their SaaS ecosystem, meet critical compliance requirements, and optimize data protection across multiple platforms.

Related Content
-
AdExchanger Data Privacy Roundup
Costello sees a broader pattern of SaaS vendors racing to bolt AI onto everything. In that rush, security is a lower priority.
-
New phishing campaign tricks employees into bypassing Microsoft 365 MFA
Cory Michal, CSO at AppOmni, said attacks often leverage OAuth tokens and service/integration identities because they’re a blind spot for many orgs.
-
Identity Crisis: Why SaaS Attacks Are Bypassing Your Best Defenses
To help build a solid foundation for AI adoption, IM firms should source high-quality data, use modern data cloud/hybrid infrastructure, and adopt robust data governance principles.
“I needed to get a better understanding of the overall attack surface, our portfolio of applications, and their configurations and data exposure risks.”
Wai Sheng Cheng
Information Security and Risk Manager, Spencer Fane

Cut compliance reporting time by 90%. What took days now takes minutes.
Centralize controls, map requirements, and prove compliance fast.