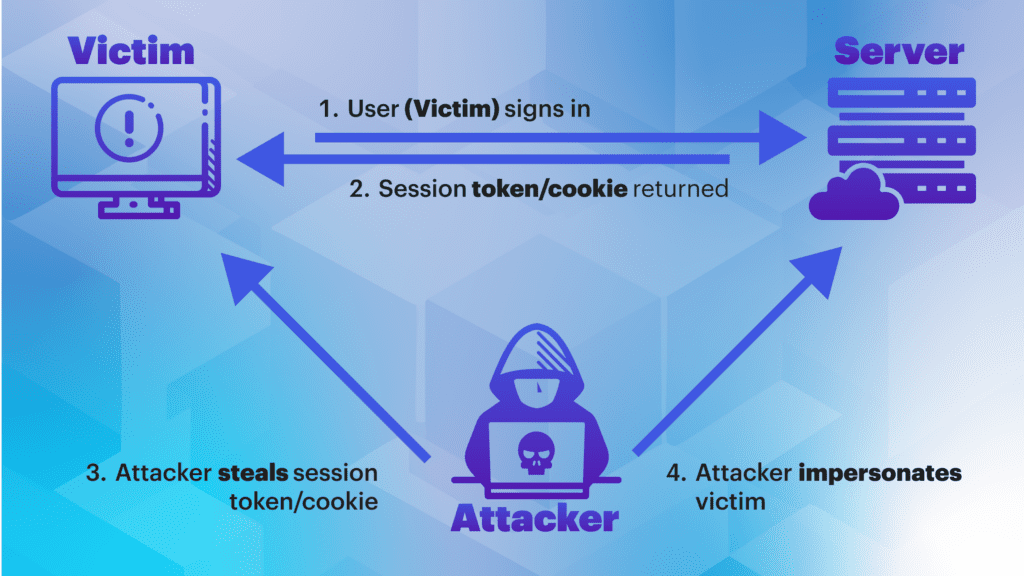
As businesses move more of their most sensitive data and operations into SaaS platforms, the risks have evolved. One of the most dangerous and underappreciated threats is session hijacking—where an attacker steals a valid session (like a cookie or token) and uses it to impersonate a legitimate user within the SaaS app. This bypasses traditional security controls and, in many cases, provides direct access to critical business systems.
In classic IT environments, session hijacking was already serious. In SaaS, it’s even more problematic because:
- SaaS apps are always internet-facing, accessible from anywhere
- Session tokens are often long-lived and sometimes shared across connected apps
- SaaS providers may offer limited visibility or inconsistent logging into session activity
The reality is that once a session is hijacked, perimeter defenses (like CASB or SSE) are no longer relevant. Attackers have an open door—and it’s your SaaS data at risk.
How session hijacking happens in SaaS
Understanding the attacker’s playbook is the first step in defense. In recent years, AppOmni Labs and leading security researchers have observed a steady rise in session hijacking attacks targeting SaaS apps, often using one of these methods:
- Phishing for session tokens: Modern phishing kits don’t just steal usernames and passwords—they grab session cookies or OAuth tokens, instantly giving the attacker access without triggering MFA challenges.
- Exploiting insecure integrations: Many SaaS platforms allow third-party or shadow applications to connect via OAuth or API keys. If those integrations are poorly secured or overprivileged, attackers can hijack sessions to gain persistent access.
- Man-in-the-middle attacks: With users accessing SaaS from everywhere, insecure WiFi or compromised networks can let attackers intercept session tokens.
- Session fixation: Forcing a user to authenticate using a session ID the attacker already knows, then using that session once authenticated.
These techniques are not hypothetical. High-profile incidents, such as the 2024 Midnight Blizzard attacks, have highlighted how threat actors can leverage token theft to maintain persistent, stealthy access to SaaS environments for months—sometimes evading detection altogether.
How you can prevent and prepare for session hijacking
Detecting session hijacking is challenging because, on the surface, the attacker is using valid credentials and a valid session. Traditional anomaly detection—looking for failed logins or brute force attempts—doesn’t always work. Instead, security teams need to take a holistic, context-rich approach.
Simulate session hijacking in your SaaS applications
Most organizations overestimate their ability to detect and respond to SaaS session hijacking until they actually test it. Simulating these attacks in a safe, controlled environment is now a recommended practice for any team responsible for SaaS security posture management.
First, set up a non-production SaaS tenant and create a few user accounts with varying permission levels. Using penetration testing tools or browser plugins, you can generate a valid session (cookie or token), then transfer it to a separate browser or machine to mimic a real-world hijacking scenario. Does your security stack alert you? Are your SIEM and threat detection workflows triggered? If not, you’ve just uncovered a visibility gap—a common finding even among mature organizations.
AppOmni’s research shows that simulation often reveals:
- Gaps in SaaS log ingestion and normalization
- Delays or failures in detection of “impossible travel” or abnormal session activity
- Insufficient correlation between identity, session, and data access events
- Challenges in revoking active tokens across multiple SaaS and connected apps
The exercise isn’t just about breaking in—it’s about stress-testing your incident response and building muscle memory for the SOC team.
Unify your SaaS visibility
Modern SaaS environments are complex: Each app has its own log format, session controls, and integration points. Without unified visibility, threats slip through the cracks. Centralizing SaaS audit logs and normalizing them across platforms is the first step, as recommended by leading frameworks like Continuous Threat Exposure Management (CTEM).
Monitor behavioral analytics and create baselines
Rather than looking for one-off events, advanced detection leverages User and Entity Behavior Analytics (UEBA) to baseline what “normal” looks like for each user and service account. For example, if a user normally logs in from the US office, and suddenly their session cookie is used from an overseas IP with admin activity, that should trigger an alert—even if the login is technically valid.
Correlate identity and session data
Sophisticated detection correlates session activity with user roles, permissions, and recent changes. A session token tied to a privilege escalation event or rapid-fire API access can be a strong signal of compromise.
Build custom detections for specific SaaS apps and scenarios
Off-the-shelf rules won’t catch every threat. Leading teams are building custom detections for scenarios like:
- Simultaneous logins from geographically distant locations (impossible travel)
- Unusual OAuth token usage
- Multiple session tokens issued to a single user in a short period
- Sudden mass download or data exfiltration using an active session
AppOmni’s own research and threat detection content emphasize the importance of layering these capabilities and integrating with existing SIEM and SOAR tools, so your team can respond instantly to high-fidelity alerts, not drown in noise.
Real-world lessons and customer insights
Recent SaaS breaches have underscored the reality that session hijacking is not an edge case—it’s becoming the attacker’s method of choice, especially against organizations with strong MFA and password policies. As customer advocacy stories show, organizations that invest in deep SaaS visibility and continuous monitoring consistently detect threats sooner and respond faster.
One CISO summarized it this way:
“Previously, manual reviews took weeks, but with AppOmni’s help, we’ve shortened this process to a few hours, significantly enhancing our efficiency and response time.”
Another customer shared that with comprehensive session and identity monitoring, “SOC and incident response teams activated, receiving alerts directly from AppOmni—before any notification from the SaaS provider. That immediacy of alerting was absolutely critical.”
These are not isolated cases. As SaaS attack surfaces grow—driven by remote work, more integrations, and growing volumes of sensitive data—session hijacking will only increase in frequency and impact.
Takeaways for SaaS security teams
Session hijacking represents a convergence of technical and operational risk. Here’s how security leaders can move from reactive to proactive:
- Elevate SaaS session visibility to a first-class priority. Ensure your tools provide deep, normalized telemetry across all critical SaaS apps.
- Simulate attacks regularly to validate your controls and keep your team sharp.
- Invest in behavioral analytics that go beyond static detection, surfacing meaningful anomalies based on user and system context.
- Integrate detection and response, so that revoking tokens and remediating accounts is swift and seamless when incidents occur.
- Educate end users and admins on the importance of session hygiene, reporting suspicious activity, and recognizing phishing attempts for tokens—not just credentials.
The days of relying solely on perimeter security are over. Defending SaaS means seeing and stopping attacks where they actually happen: inside the session.
For more hands-on SaaS security guidance, best practices, and the latest threat research, visit AppOmni’s blog and AO Labs. Learn how leading organizations are closing the gaps on SaaS risk—one session at a time.
Analyzing the Attack Lifecycle of a Direct Deposit Scam

MFA can minimize impact on payroll diversion attacks, but adversaries leverage MFA bypass methods such as session hijacking.
Read more: Payroll Fraud: Analyzing the Attack Lifecycle of a Direct Deposit Scam