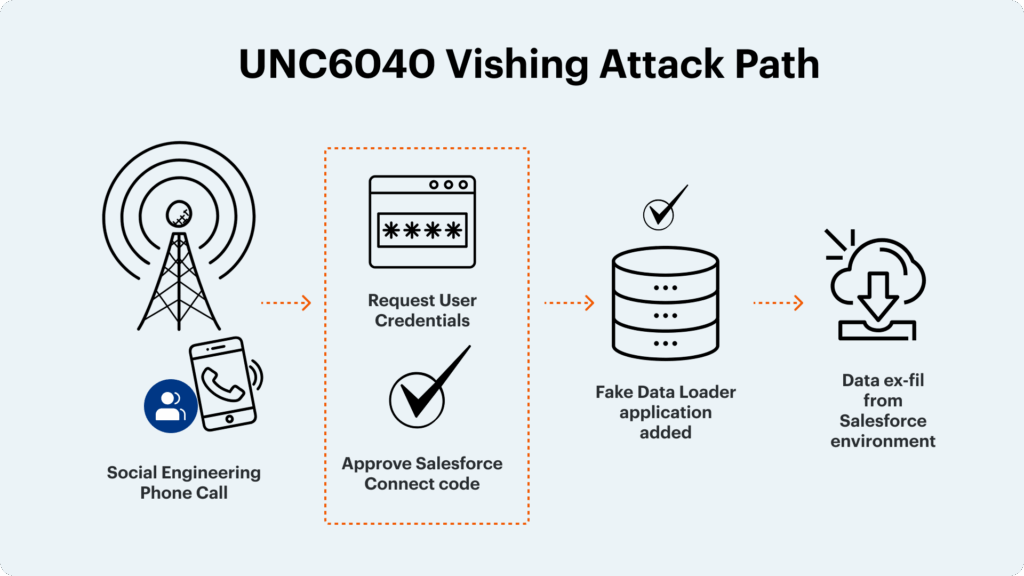
UNC6040’s (closely linked to ShinyHunters) phone-phishers lure employees into approving a fake dataloader[.]io app, hijacking Salesforce APIs to siphon customer data. Turning on Salesforce API Access Control blocks every integration you haven’t explicitly allow-listed—blocking UNC6040-style breaches before a single record leaves your CRM.
UNC6040 and Salesforce OAuth connected apps: How the attacks work
Google’s Threat Intelligence Group recently spotlighted UNC6040, a financially-motivated attacker group (closely linked with ShinyHunters) that cold-calls employees, impersonates internal IT, and persuades them to “install” a fake connected app—usually branded dataloader[.]io—inside Salesforce. Once the OAuth prompt is approved, the attackers siphon CRM records and demand ransom.
Which Salesforce setting instantly blocks rogue OAuth apps?
Salesforce ships a little-known feature called API Access Control. When enabled, it blocks every incoming API connection except apps that admins have allow-listed. If the feature is not already enabled in your environment, raise a case with Salesforce to enable it. API Access Control flips the environment from “users may self-authorise anything” to “only admin-approved apps and pre-authorised users connect.” Any unsigned app—malicious or merely unsanctioned—fails to authenticate, short-circuiting the UNC6040 playbook.
What we recommend today
Note: The review times in the table below are estimates. The amount of time taken will depend upon the connected apps and Salesforce tenants in each organization.
| Step | Owner | Time |
| 1. Review Connected Apps → OAuth Usage and mark each as Install (approved) or Block. | SFDC Admin | 30 mins |
| 2. For every Installed app, switch Permitted Users to “Admin-approved users are pre-authorized” and assign a permission set to legitimate users. | SFDC Admin | 30 mins |
| 3. Open a Salesforce support case to activate API Access Control, test in a sandbox, then enable in production. | SFDC Admin | 10 mins |
| 4. Brief support teams and users about vishing (or voice phishing) risks – be skeptical of IT requests made by phone, verify through official channels. | Security/IT | 15 mins |
Why Salesforce API access control is stronger than manual app reviews
Manual reviews catch yesterday’s risks; API Access Control stops tomorrow’s. By restricting OAuth at the gate, you eliminate whole classes of attacks—credential phish, rogue integrations, insider mistakes—without slowing legitimate workflows.
How does AppOmni keep you ahead after you enable the control?
- Baseline Best-Practice Policies – Our out-of-the-box policy set already flags orgs where users can self-authorize apps or where API Access Control is off, so you know instantly if you’re at risk.
- Continuous SaaS-to-SaaS Governance – We monitor every new OAuth app, compare it against your allow-list, and raise prioritized alerts when something unapproved appears—no manual log digging required.
- Guided Remediation & Automation – One-click policy fixes and optional workflow automation help you close gaps faster and keep them closed.
- Threat Detection and Response – We continuously assess your implementation for indicators of active events unfolding, from initial access to exfiltration.
AppOmni’s latest State of SaaS Security 2025 Report shows that 75% of organizations experienced a SaaS-related security incident in the last year, even though 91% felt confident in their posture. Rogue OAuth apps are one of the clearest reasons that perception and reality diverge.
Key takeaways for security & CRM teams
- Enable API Access Control today to neutralize UNC6040-style rogue-app attacks.
- Review and curate your Connected App list; limit approval to business-critical integrations.
- Augment native controls with continuous monitoring. AppOmni automates discovery, policy enforcement, and threat detection so nothing slips through the cracks.
Ready to take control?
Download your free checklist and get practical steps to secure OAuth tokens, protect SaaS data, and manage third-party risk today.
-

BodySnatcher (CVE-2025-12420): A Broken Authentication and Agentic Hijacking Vulnerability in ServiceNow
This blog deeply analyzes the interplay between Virtual Agent API and Now Assist enabled in this exploit.
-

When AI Turns on Its Team: Exploiting Agent-to-Agent Discovery via Prompt Injection
Aaron Costello uncovers how second-order prompt injection turns AI agents against their own systems. He explains how attackers exploit ServiceNow’s Now Assist and offers clear guidance on securing AI collaboration.
-

Salesforce Industry Clouds: 0-days and Exploitable Misconfigs
AppOmni’s latest research reveals 20+ OmniStudio security flaws, including 5 CVEs affecting Salesforce industry clouds. Learn how misconfigurations expose sensitive data and how to secure your org.