By Paul McAndrew and David Tocco — Threat Detection Research Unit, AppOmni
UNC6040 (closely linked to ShinyHunters) threat actors are using social engineering tactics—often starting with vishing but not limited to it—to persuade Salesforce users to authorize rogue OAuth apps. First reported by the Google Threat Intelligence Group in June, these attacks enable collection and data exfiltration at scale, bypassing traditional security controls.
We recommend starting with our previous blog on the topic Shutting the Door on Vishing-Driven Data Theft in Salesforce for recommendations on policy and posture settings including reviewing connected apps in your organization and enabling API Access Control. Additionally, review the following recommendations from Salesforce: Protect Your Salesforce Environment from Social Engineering Threats. In this blog, we will focus on how to detect suspicious activities in Salesforce OAuth attacks like those used by UNC6040.
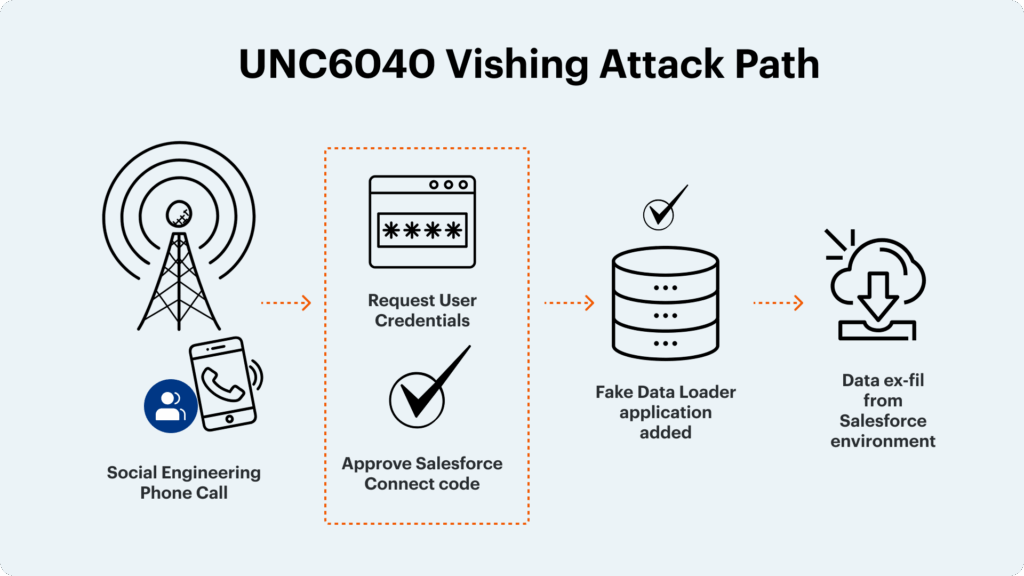
Salesforce vishing and OAuth exploits: How to stay ahead of UNC6040
While the tactics used in these campaigns are not necessarily novel, detecting them requires understanding the patterns generated by the malicious activity relative to normal user behavior. AppOmni empowers organizations to see what others miss—combining behavioral analytics, threat intelligence, and real-world attack patterns to stop vishing-driven OAuth abuse in Salesforce before it becomes a breach.
Here’s how AppOmni’s out-of-the-box detections work:
- AppOmni’s UEBA (User and Entity Behavior Analytics) detections can identify anomalous behaviors such as first-seen network locations or authentication methods that have not been previously associated with a specific user. While targeted intrusions may attempt to evade detection by using residential proxies, large-scale campaigns (such as those linked to UNC6040) often rely on generic infrastructure.
- AppOmni identifies suspicious VPN activity. This may also involve Tor or less common hosting providers, such as niche VPS services. By correlating data exfiltration attempts with the use of non-corporate VPNs, AppOmni can generate high-fidelity detections, leveraging patterns observed in prior confirmed attacks.
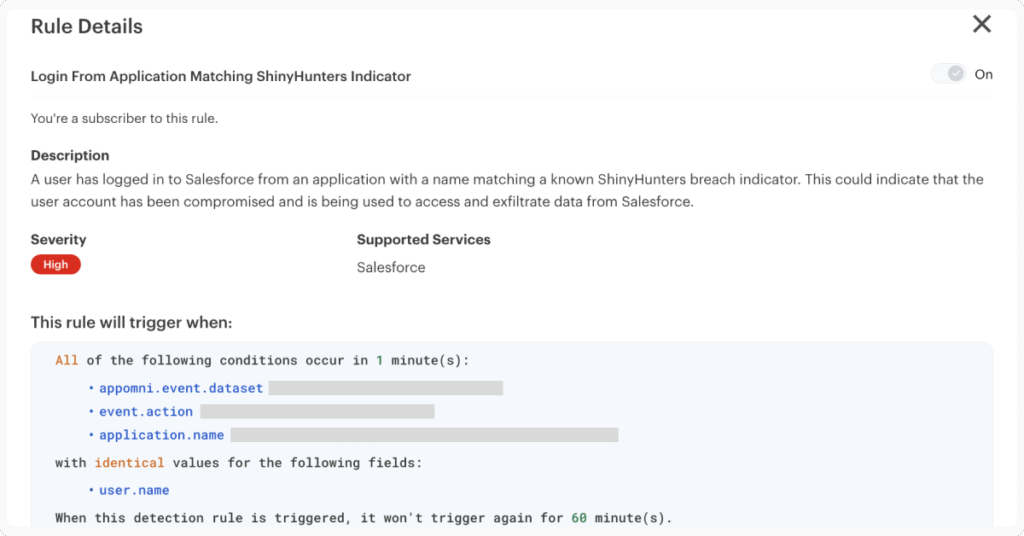
- AppOmni has identified several suspicious OAuth application names and deployed targeted detection logic to alert on their usage. Examples include names such as “My Ticket Portal” and similar variations designed to appear legitimate.
- AppOmni’s Threat Detection can alert on unusual OAuth authentication activity, including logins from previously unseen network locations or from OAuth applications not previously associated with the user. When this activity coincides with other suspicious signals, such as non-corporate VPNs, residential proxies, or atypical hosting providers, it may indicate an attempt to abuse OAuth tokens for unauthorized access or persistence.
- AppOmni can easily be onboarded to immediately provide detection capabilities in Salesforce environments. AppOmni’s Threat Detection Research Team and SaaS Security Research team will continue to monitor, test, and improve both posture insights as well as detection alerts to enable organizations to best protect themselves against this ongoing campaign.
Ready to strengthen your SaaS security? Here are 3 ways you can continue your journey to contain SaaS threats:
- Get a complimentary risk assessment to get insights and visibility to third-party apps connected to your SaaS estate.
- Download the SaaS Threat Detection Toolkit. Learn 6 essential strategies needed to detect threats and reduce alert fatigue.
- Schedule a demo. We’ll personalize the session to your organization’s immediate needs.
Related Resources
-

What is the Salesforce GraphQL Exploit and What You Should Do
Salesforce GraphQL exploit exposed misconfigured guest data in Experience Cloud. Learn how it happened and how to prevent exposure.
-
ShinyHunters Claims Woflow Breach: What It Means for SaaS Supply Chain Security
Learn the security risks in SaaS supply chains and about ShinyHunters’ evolving extortion tactics behind the alleged Woflow breach.
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.