On Sept 8, 2025, we added an FAQ section regarding the Salesloft Drift (UNC6395) supply chain attack.
On Sep 12, 2025, the FBI released IOC’s and tactics to help teams block potential attacks.
Is your Salesforce environment integrated with third-party apps like Salesloft Drift? If so, your organization could be at risk of the Salesloft Drift – Salesforce breach or other SaaS supply chain attacks executed by advanced threat actors like UNC6395.
In early August, UNC6395 (an assessed Chinese threat actor) leveraged compromised OAuth tokens from the Salesloft Drift integration to infiltrate Salesforce environments. By abusing trusted access, the attacker ran targeted SOQL queries across critical Salesforce objects such as Users, Accounts, and Cases, quietly exfiltrating highly sensitive business data: AWS keys, Snowflake tokens, passwords, and more. According to Google, over 700 organizations have been impacted.
The FBI Cybersecurity Advisory (CSA-2025-250912) further warned that attackers like UNC6395 are actively compromising Salesforce instances for data theft and extortion, underscoring the urgency of securing OAuth connections and third-party integrations.
This incident is just the latest example of SaaS supply chain attacks, where trust in one connected app can open the door to broader data exposure, and shows why app owners must stay vigilant.
What happened: UNC6395 & the Salesloft Drift breach
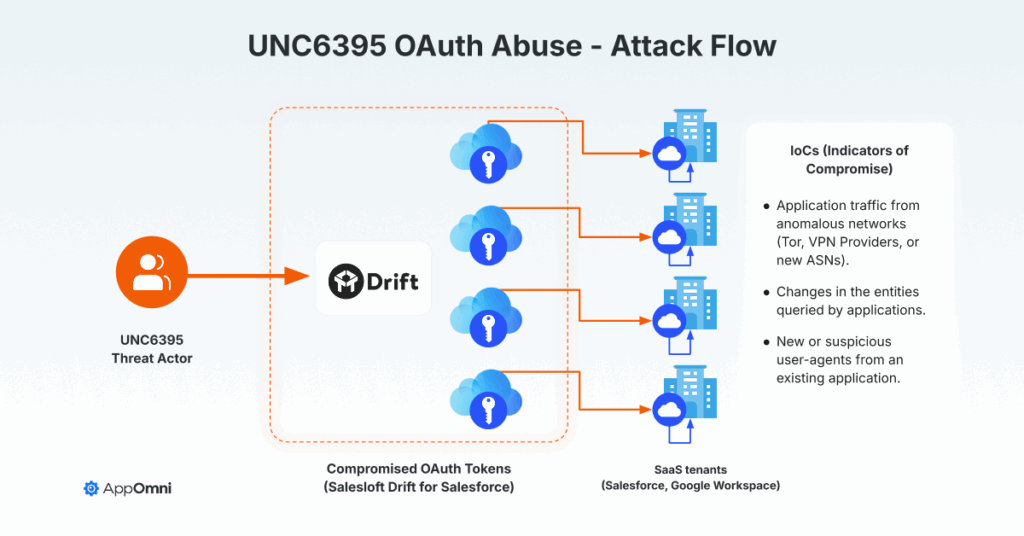
How the attack worked:
- The threat actor ran SOQL queries on Salesforce objects like Users, Accounts, Opportunities, and Cases
- Systematically exfiltrated sensitive credentials and secrets
- Deleted query jobs after execution to hide activity (but audit logs still retained evidence)
Salesloft & Salesforce response actions:
- On August 20, 2025, Salesloft and Salesforce revoked all Drift OAuth tokens.
- Salesforce also removed the Drift application from the AppExchange pending further investigation.
- Impacted organizations were directly notified by Salesforce.
Key observations:
- Attackers ran reconnaissance queries to measure record volumes before selectively pulling detailed user and case data.
- The primary objective appeared to be credential harvesting for downstream attacks.
- Malicious activity was tied to suspicious User-Agent strings, Tor exit node traffic and VPS for data exfiltration.
Why the Salesloft Drift – Salesforce breach worked
The UNC6395 attack succeeded because of common oversights in SaaS environments, turning the Salesloft Drift integration into an entry point for a broader SaaS supply chain attack. The lateral movement is made possible by the abuse of admin OAuth tokens from lesser-known SaaS apps to compromise business-critical applications. Attackers are taking advantage of:
- Persistent OAuth access: Unlike user sessions, OAuth tokens often don’t expire, creating long-term exposure in the event of an OAuth breach.
- Over-permissive access: Many apps request full data access and are approved without review
- Limited monitoring: Most organizations don’t monitor or ingest logs or policies for SaaS applications, making it difficult to detect abuse during a Salesforce breach.
- Unsecured secrets: Credentials stored insecurely in Salesforce fields amplified the impact
How to prevent SaaS supply chain attacks like the Salesloft Drift breach by UNC6395
To effectively prevent SaaS supply chain attacks, focus on these key actions:
- Apply least privilege to service accounts. Know exactly what data these identities can access.
- Scan for exposed secrets. Look for stored AWS keys, tokens, or passwords in your Salesforce schema and data records.
- Utilize IP Restrictions. Build restrictions for applications and integrations, limiting access.
- Manage data access, not just APIs. Limiting scopes isn’t particularly useful for Salesforce integrations. Instead, focus on monitoring and restricting which Salesforce Objects, Fields, and Records your accounts and integrations can access.
- Correlate SaaS logs. Work with security teams to bring together Salesforce, Okta, Google, and Microsoft logs for better threat visibility.
- Use behavioral analytics. Even if access looks normal, UEBA can surface when an app or user starts behaving suspiciously.
How AppOmni protects against SaaS supply chain attacks like the Salesloft Drift Salesforce breach
AppOmni helps organizations prevent, detect, and respond to SaaS breaches, including high-profile incidents like the Salesloft Drift – Salesforce breach attributed to UNC6395. The platform delivers deep visibility into third-party OAuth integrations and enforces monitoring policies and controls to block suspicious activity such as mass exports or anomalous API calls.
By combining Threat Intelligence Enrichment with User and Entity Behavior Analytics (UEBA), AppOmni normalizes SaaS logs to surface anomalies like mass SOQL queries, excessive OAuth token use, or unusual data exports. Each SaaS attack scenario is unique and malicious activity where the attackers cover their tracks well may be hard to detect. AppOmni recommends that customers use a combination of well-structured posture controls together with runtime threat detection capabilities. With the right policies and detection rules, AppOmni’s capabilities can enable early detection of adversarial campaigns, when attackers attempt to evade detection or blend into normal workflows.
With immediate visibility and control over your applications, security teams can stay ahead of attackers. Explore our Salesforce handbook to learn more about recent attack patterns and how to stop them.
Wondering if a connected app like Drift could put your Salesforce data at risk? Request a complimentary risk assessment of your Salesforce Instance.
UNC6395 breach: Frequently asked questions
The UNC6395 attack was a sophisticated cyberattack where a suspected Chinese nation-state threat actor, UNC6395, compromised the Salesloft Drift integration to gain unauthorized access to Salesforce as well as other connected environments. This is considered a SaaS supply-chain attack because it exploited the trusted connection between two software-as-a-service (SaaS) applications.