Key Takeaways
- Attacks on identity providers (IdP) are on the rise. There have been a spate of recent Okta related compromises over the past 12 months, impacting a number of Okta customers.
- The most recent compromise was confirmed by Okta on October 20, 2023.
- No action is required by AppOmni customers for this compromise. The AppOmni Threat Research Team has conducted a thorough investigation across all customer environments and has shared any details directly with customers that showed any events that may warrant further investigation.
- Through AppOmni’s continuous monitoring capability, customers are proactively alerted to any suspicious Identity and Access Management (IAM) activity across their monitored SaaS services.
Measures to Harden Your Identity Security
- Companies should regularly assess their cybersecurity posture and implement proactive measures that include continuous monitoring to protect their end-users, systems, and data.
- IAM platforms like Okta can be vulnerable to attacks, emphasizing the need for additional, layered security measures.
- For more information on hardening strategies, refer to our recent blog post on mitigating configuration risks in IAM systems.
- Learn more about the most recent Okta compromise here.
Summary of Recent Okta Breaches
In recent months, a series of cyberattacks have targeted Okta, a widely used IAM platform. Watch this step-by-step video below to learn how the Okta HAR breach happened.
These breaches have affected several prominent companies, including MGM Resorts, Caesars Entertainment, Cloudflare, 1Password, and BeyondTrust.
MGM Resorts and Caesars Entertainment Breaches
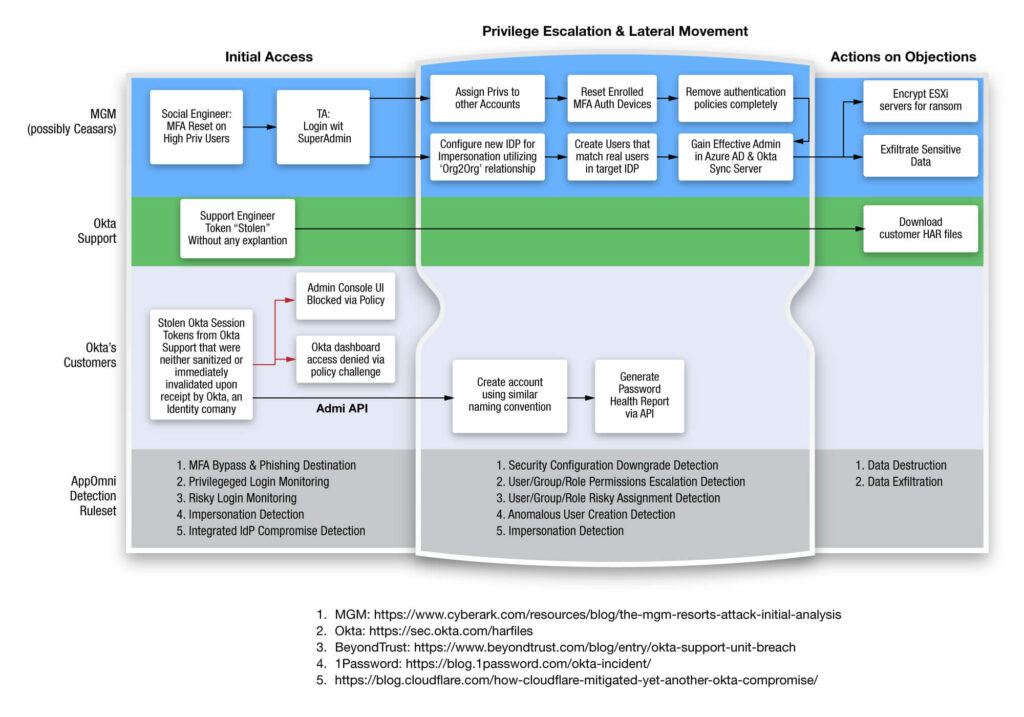
In September 2023, MGM Resorts and Caesars Entertainment, two major casino operators in Las Vegas, fell victim to cyberattacks. Threat actors used social engineering to successfully compromise login credentials at the target organizations, including Okta, and then leveraged Okta for persistence to gain access to additional applications in the compromised organizations. The threat actors, identified as the ALPHV ransomware group and its affiliate Scattered Spider, gained access to sensitive customer data, encrypted production servers, and demanded ransom payments to decrypt their data.
Okta Breach and its Impact on Customers
In an unrelated event starting some time in early October, Okta was compromised in an undisclosed manner, with the attackers gaining access to internal support systems. This allowed attackers access to HAR files which are used by support staff to assist in troubleshooting Okta configurations. If not properly sanitized, HAR files can contain authentication tokens that are capable of being reused to access an insufficiently hardened Okta deployment, and take advantage of limitations of Okta policy enforcement between console and API actions.
BeyondTrust and Other Impacted Customers
BeyondTrust, a cybersecurity company that provides privileged access management solutions, was among the Okta customers affected by Okta’s customer support breach. The company acknowledged that the attackers had gained access to some of its internal systems but maintained that customer data remained secure. Additionally, 1Password was alerted to suspicious activity in their Okta deployment that later was revealed to be a result of the Okta support compromise. Lastly, Cloudflare internal security team was alerted to suspicious activity stemming from their Okta environment that was later confirmed to be related to the Okta support breach.
AppOmni’s Response
In light of the number of new breaches being disclosed impacting customers of Okta, Appomni’s Threat Research Team has reviewed and expanded our current ruleset to provide additional coverage for the techniques disclosed over the last 3 months. No action is required from customers, these rules are enabled by default.
As an additional measure, we reviewed the indicators of compromise (IOCs) shared by Okta, and retroactively scanned all our customers’ Okta events for any hits on these IP Addresses or User Agents. While these events do not always signify confirmed compromise they are a good starting point for further investigation. At this point we have concluded our investigation and if there were any events of interest, they have been shared directly with customers.
Overall Impact and Lessons Learned
Attacks on SaaS will continue to escalate and grow in complexity given that SaaS is fast becoming the critical infrastructure for business. Compounding the security challenges of SaaS, is the lack of industry awareness in monitoring and protecting SaaS applications and the sensitive data it may contain, which only serves to increase threat actor interest in compromising these systems.
The AppOmni Threat Research Team is continuing to focus our research on the attack surface of Okta as well as the larger suite of SaaS IdP’s products. We are relentlessly committed to protecting your monitored assets, and given this, you can expect our collection of SaaS Security Posture Management rules and capabilities to continue to evolve to meet the ever-changing threat landscape.

Detect and Prevent Okta Compromises with SSPM
See step-by-step how this identity-centric breach occurred and how SSPM can detect and prevent sophisticated attack mechanisms.
Related Resources
-

ServiceNow Agentic AI: What It Means for CISOs, SOC Analysts, SaaS Admins, and Developers
Agentic AI expands ServiceNow risk. Read why securing AI agents matters for CISOs, InfoSec, SOC, admins, and IT leaders.
-
Secure Now Or Pay Later: A CISO’s Guide To AI Security
The same SSPM principles that guide SaaS protection also apply directly to AI. So, what steps can CISOs take now?
-

2026 in AI Ops presents opportunity, challenges
In 2026, IT pros should expect to see AI usage grow in importance, said AppOmni Director of AI Melissa Ruzzi, as automation and “self healing” become mainstream.