Attack Vector Definition
An attack vector is a means for exploiting a computer system that places it, its network, and the sensitive information it contains at risk of a data breach.
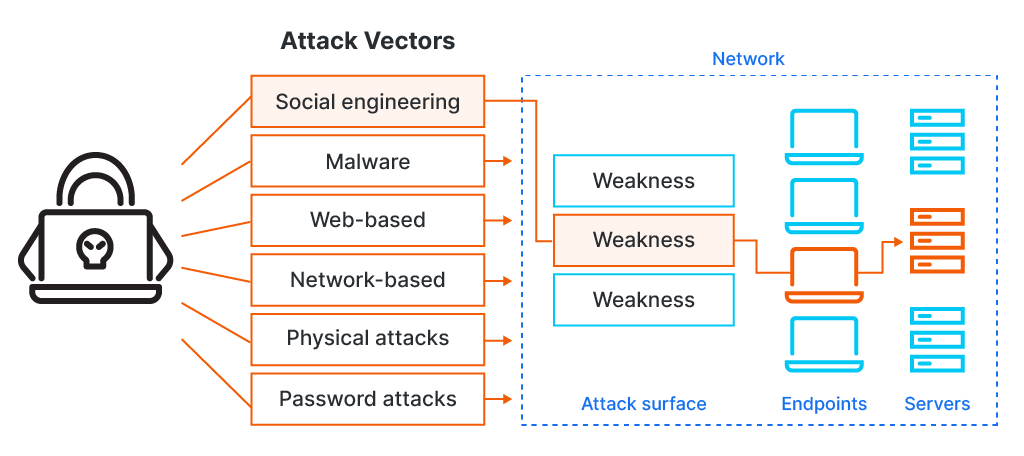
Attack Vector FAQs
What is an Attack Vector?
Attack vectors allow hackers to gain unauthorized access to operating systems (OS). For example, an attacker may exploit unpatched software to compromise a system or deploy malware to infect it.
Other common cloud attack vectors include phishing/social engineering tactics. These latter methods target unsafe human behavior such as leaving factory passwords in place or clicking on links in unknown messages.
What is the Difference Between an Attack Vector vs Vulnerability?
Attack vectors and vulnerabilities are related concepts that refer to distinct threats to a system, its software/hardware, or its organizational processes:
An attack vector is the approach or tools an attacker uses. Phishing emails and malware are examples of attack vectors.
Vulnerabilities are specific coding errors, misconfigurations, weak passwords, or unpatched software that an attacker can exploit.
What is an Attack Surface? How do Attack Vectors vs Attack Surfaces Differ?
The difference between attack surface and attack vectors is like the difference between a forest and its trees:
Attack vectors are the specific tools and methods attackers use to exploit vulnerabilities in a system. Every system has multiple attack vectors, and together as a whole, they create an overall picture.
The attack surface is the aggregate of exploitable points in the network that could be attacked—that overall picture of multiple cyber security attack vectors that could be used to exploit a single system or network. It includes any hardware, software, interfaces, and human factors that could be targeted. Examples include open ports, web applications, network devices, user accounts, and even physical access points.
Reducing both attack vectors and attack surfaces is key to strong cybersecurity. Minimizing attack surfaces involves minimizing the number of opportunities for attack vectors to be successful, while minimizing attack vectors individually obviously protects data problem by problem.
Is There a Difference Between Threat Vectors vs Attack Vectors?
Although they are often used interchangeably in cybersecurity, there is sometimes a subtle, contextual difference between attack vector vs threat vector. Threat vector is a slightly broader term that is sometimes used to encompass not just specific methods used (like a classic attack vector) but also overall routes for attack and broader threat categories and pathways such as insider threats, environmental factors, or systemic vulnerabilities that could lead to security incidents—making threat vectors more like categories or types of attack vectors.
What are Attack Vectors in Cyber Security?
What is an attack vector in cyber security—are there different categories? Are there more common types of cybersecurity attack vectors to expect?
What is the Most Common Attack Vector?
One of the common types of attack vectors in cyber security is phishing, the use of fraudulent messages that seem trustworthy. Phishing messages trick recipients into revealing sensitive data such as usernames and passwords or credit card numbers.
Attack Vector Types and Categories
Cyber attack vectors can be classified based on attacker methodology and tools. Here are some basic attack vector categories:
Social engineering attack vectors exploit human behavior.
- Phishing. These deceptive emails or messages steal information or gain access.
- Pretexting. Fabricated scenarios to steal information.
- Baiting. Enticing victims to click links to take other unsecured actions with offers or rewards.
- Tailgating. Following someone into a restricted area.
Malware is software designed to harm or exploit systems.
- Viruses. These self-replicating programs infect files.
- Worms. These self-replicating programs spread through networks rapidly.
- Trojan horses. This malicious software is disguised to look legitimate.
- Infostealers. Malicious software designed to steal valuable information from victim hosts.
- Ransomware. Encrypting data and demanding ransom for decryption.
Web-based attack vectors exploit vulnerabilities in applications.
- SQL injection. This attack inserts malicious SQL code into queries.
- Cross-site scripting (XSS). This injects malicious scripts into websites.
- Cross-site request forgery (CSRF). This forces users to execute unwanted actions.
Network-based attacks exploit vulnerabilities in the network.
- Man-in-the-middle attacks. These intercept and alter communications.
- Denial of service (DoS). These overload systems to disrupt services.
- Distributed denial of service (DDoS) attacks. These common attack vector examples overload networks with a DoS attack using multiple systems.
Physical attacks gaining unauthorized access to hardware.
- Theft of devices. Stealing laptops, smartphones, or storage devices.
- Tampering. Physically altering or damaging hardware.
Password attacks compromise user passwords.
- Brute force attacks. Attackers try all possible password combinations.
- Dictionary attacks. These attackers use a list of common passwords.
- Credential stuffing. Use of compromised credentials between services and platforms.
An initialization vector attack is a cryptographic assault on the initialization vector used in encryption algorithms. This kind of attack exploits weaknesses in the IV implementation to gain information about the encrypted data or manipulate the encryption process.
- Replay attacks. If the IV is reused or predictable, an attacker can capture and replay the encrypted data to perform unauthorized actions.
- Chosen-plaintext attacks. If an attacker can predict or control the IV, they can craft specific plaintexts to reveal patterns or weaknesses in the encryption.
- Bit-flipping attacks. In some modes of operation, an attacker can alter the ciphertext to cause predictable changes in decrypted plaintext, potentially leading to data manipulation or leakage.
A multi-vector attack employs many vectors simultaneously or sequentially to compromise a target system or network. Multi-vector attacks highlight important differences in attack surface vs attack vector focused security, in that attention to the broader attack surface accounts for more complex approaches like these.
- Advanced persistent threats (APTs). These targeted attacks use spear-phishing, zero-day flaws, and malware to gain long-term access to the network.
- Combined credential stuffing and brute force attacks. Attackers might combine methods to access accounts or systems.
What is Attack Vector Analysis, Mapping, and Security?
Attack vector analysis identifies and assesses the methods attackers could use to compromise a system:
- Identifying vulnerabilities. Reviewing systems, applications, and networks to find security weaknesses.
- Evaluating threats. Understanding relevant attack vectors local to the organization, such as malware, phishing, DDoS attacks, etc.
- Assessing exploitation methods. Determining how these threats can exploit the identified vulnerabilities.
- Prioritizing risks. Ranking potential attack vectors based on their likelihood and organizational impact.
Attack vector mapping involves creating a visual representation of the various ways an attacker might compromise a system:
- Visualizing pathways. Diagram potential routes and attack vector vulnerabilities from a hacker’s perspective.
- Identifying entry points. Mark all unsecured network ports, vulnerable software, or weak passwords.
- Mapping out defense mechanisms. Identify existing security controls and potential gaps.
- Understand flow through the attack vector network. Analyzing how an attack could progress through different stages, from initial access to data exfiltration.
Attack vector security focuses on implementing measures to protect against any identified attack vectors:
- Implement security controls. Deploy firewalls, intrusion detection/prevention systems (IDS/IPS), anti-malware tools, and other security measures.
- Strengthen defenses. Patch vulnerabilities, harden configurations, encrypt data.
- Continuous monitoring and detection. Use SIEM systems and other monitoring tools to look for signs of attacks and unusual activity.
- Incident response. Develop and practice incident response plans to quickly react to detected attacks and minimize damage.
- Security awareness training. Educate employees about best practices for security threats.
Practical tips for attack vector analysis, mapping, and security:
- Conduct regular threat assessments to identify threats and vulnerabilities.
- Create attack maps of possible different attack vectors. Use tools and methodologies such as threat modeling and attack trees.
- Implement multi-layered security. Ensure multiple layers of controls are in place.
- Regularly update and patch software and hardware systems.
- Engage in continuous monitoring. Use advanced tools to detect and respond to threats in real-time.
- Develop and test incident response plans. Prepare for potential breaches and conduct regular drills.
How Does AppOmni Help Reduce the Threat Posed by Attack Vectors?
AppOmni helps users see where threats and risks from attack vectors exist in seconds. Continuous monitoring, threat detection, and configuration management from AppOmni allow organizations to secure their SaaS ecosystems. Both custom and out-of-the-box capabilities combine the strongest preventative measures and active threat detection to secure online environments.
Learn more about how AppOmni’s holistic approach can reduce threats from attack vectors here.