Industry
AppOmni for Government
Manage configurations, security posture, and drift across your SaaS environment to reduce risk.

How AppOmni secures SaaS
for Government
Misconfigurations, unauthorized access, and compliance requirements like SCuBA, NIST 800-53, and FISMA demand a proactive approach.
AppOmni delivers visibility, control, and compliance for SaaS applications, enabling government teams to protect sensitive data, meet stringent security frameworks, and streamline compliance reporting—all without disrupting operations.

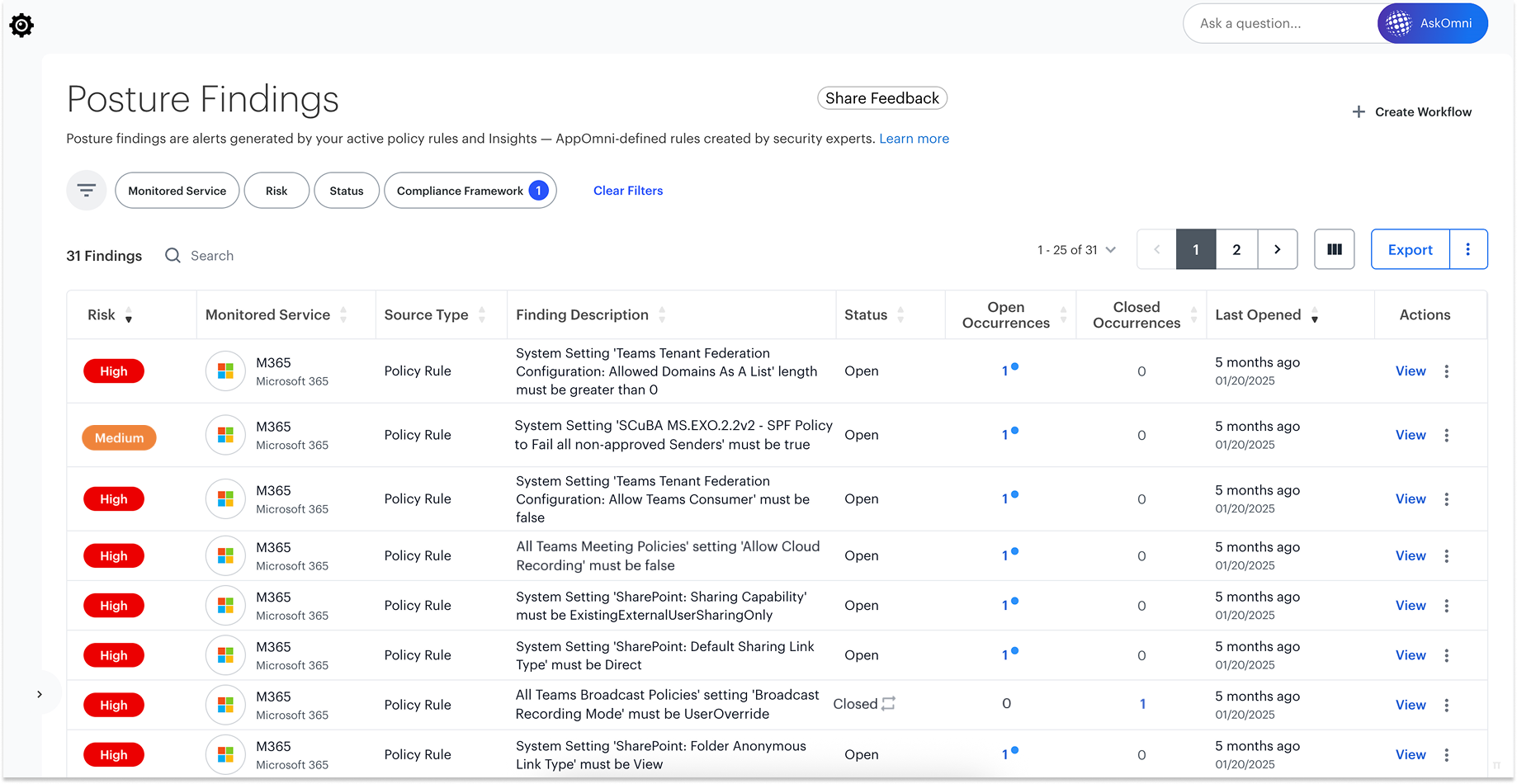
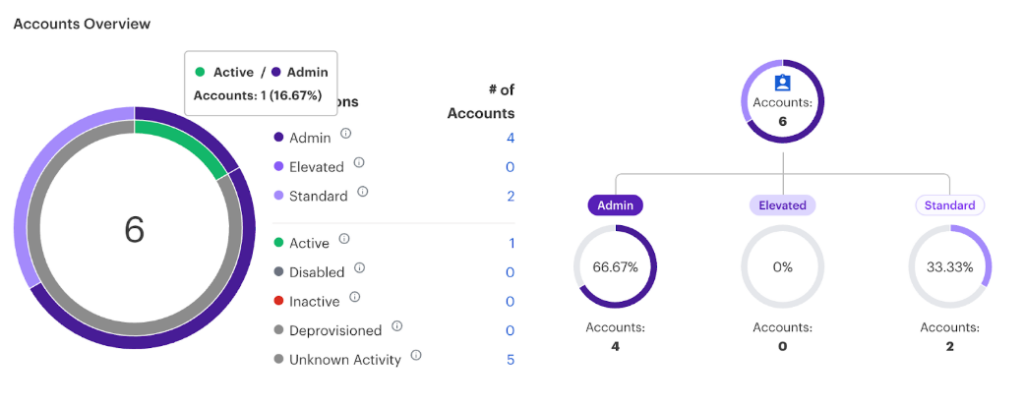
Out-of-the-box Compliance Checks

Detect Configuration Deviations

Automate With Continuous Monitoring

Triage and Remediation Guidance
FedRAMP-Authorized SaaS Security for Federal Agencies
AppOmni’s SaaS Security Platform has been granted FedRAMP® Authority to Operate (ATO), giving federal agencies a trusted path to secure their SaaS environments with confidence. Backed by 325+ controls and built to meet the U.S. government’s highest cybersecurity standards, AppOmni supports agencies in safeguarding sensitive data like CUI, PII, and PHI across platforms like M365, Salesforce, and ServiceNow.
With CISA’s BOD 25-01 now in effect, AppOmni helps federal and civilian agencies, private enterprises, and highly-regulated industries meet SCuBA compliance requirements out of the box—providing instant visibility, secure configurations, and continuous monitoring across core Microsoft apps.

AppOmni on FedRAMP Marketplace
Latest Resources
-
New phishing campaign tricks employees into bypassing Microsoft 365 MFA
Cory Michal, CSO at AppOmni, said attacks often leverage OAuth tokens and service/integration identities because they’re a blind spot for many orgs.
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-
Panera Bread breach: ShinyHunters claims hack of 14 million customers’ data
“This aligns closely with Okta’s recent warnings about vishing-driven SSO compromise targeting Okta, Microsoft, and Google.” — Cory Michal, AppOmni.