SaaS Attack Definition
A SaaS attack targets software-as-a-service (SaaS) applications or services provided over the internet. Unlike traditional software installed on individual devices or local servers, SaaS applications are hosted on cloud servers and accessed through web browsers. This centralized nature introduces distinct security challenges and vulnerabilities.
SaaS Attack FAQs
What is a SaaS Attack?
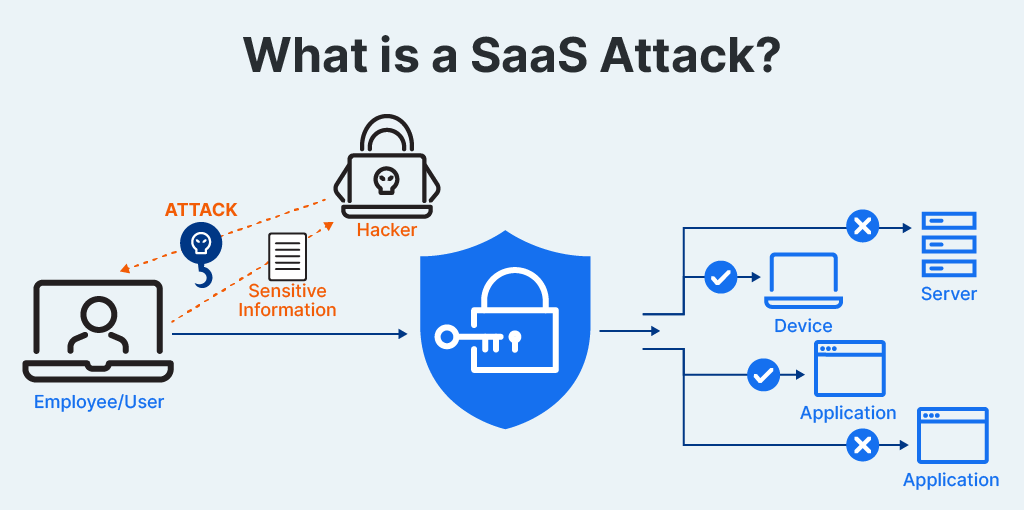
A SaaS attack targets software applications or services that users operate over the internet instead of installing on their computers. These applications, like Salesforce or Microsoft Office 365, store data and run on cloud servers, making them accessible from anywhere with a web browser.
In a SaaS attack, hackers try to steal sensitive information or disrupt services by tricking users into giving up their passwords, exploiting security weaknesses, or gaining unauthorized access. This can lead to data theft, financial loss, and interruptions in service. To protect against these attacks, companies need to use strong security practices and regularly monitor for suspicious activities.
What Are the Most Common Types of SaaS Attacks?
The different types of SaaS attacks include:
Phishing. Deceptive emails or websites trick users into revealing their login credentials by mimicking legitimate SaaS platforms.
Credential Stuffing. Attackers use stolen usernames and passwords from other breaches to gain unauthorized access to SaaS accounts.
Insider Threats. Employees or insiders misuse their access privileges to steal data or disrupt services.
Account Takeover. Attackers gain control of a user’s SaaS account through methods like phishing or credential stuffing to access sensitive data or conduct malicious activities.
Data Exfiltration. Attackers steal data stored within the SaaS application, often by leveraging authorized access or exploiting vulnerabilities.
API Exploitation. Insecure APIs provided by SaaS applications for integration with other services are exploited by attackers to access or manipulate data.
Man-in-the-Middle (MitM) Attacks. Attackers intercept and potentially alter communication between the user and the SaaS application, especially if the connection is not properly encrypted.
Ransomware. Attackers target data within SaaS applications, encrypting it and demanding a ransom for its release.
Misconfiguration. Attackers can exploit misconfigured settings in SaaS applications, such as overly permissive access controls or insecure default configurations to gain unauthorized access or extract data.
Each of these attack types poses specific risks to SaaS environments, necessitating robust security measures to mitigate potential threats.
What are the Risks of SaaS Attacks?
There are a variety of SaaS attack risks including:
Data Breaches. Unauthorized access to sensitive data stored in SaaS applications can lead to data theft, loss, or exposure.
Financial Loss. Attacks such as ransomware or fraudulent transactions can result in significant financial losses for businesses.
Reputation Damage. A successful attack can damage an organization’s reputation, leading to loss of customer trust and potential loss of business.
Service Disruption. Attacks can disrupt the availability of SaaS applications, leading to downtime and affecting business operations.
Compliance Violations. Unauthorized access or data breaches can result in non-compliance with regulatory requirements, leading to fines and legal consequences.
Intellectual Property Theft. Attackers can steal proprietary information and intellectual property, which can be used for competitive advantage or sold to competitors.
Loss of Customer Data. Compromised customer information can lead to identity theft and other forms of fraud, affecting customers directly.
Account Hijacking. Attackers can take over user accounts, leading to unauthorized activities, data manipulation, and further security breaches.
Increased Operational Costs. Addressing and mitigating the effects of a SaaS attack can incur significant costs in terms of incident response, recovery, and implementing additional security measures.
Insider Threats. Employees or other insiders with malicious intent can misuse their access to SaaS applications to steal data or disrupt services, posing significant internal risks.
How to Reduce SaaS Attack Risks
To reduce the risks associated with SaaS attacks, organizations can implement a variety of security measures and best practices:
Multi-Factor Authentication (MFA). Require users to provide an additional shared secret, object or biometric to add an extra layer of security beyond just usernames and passwords.
Strong Password Policies. Enforce the use of strong, unique passwords and encourage regular password changes.
Access Controls. Implement role-based access controls (RBAC) to ensure users have the minimum necessary access to perform their job functions.
Regular Security Training. Educate employees about common threats like phishing and how to recognize and respond to suspicious activities.
Data Encryption. Use encryption for data at rest and in transit to protect sensitive information from unauthorized access.
Security Monitoring and Logging. Continuously monitor SaaS applications for unusual activities and maintain logs to detect and investigate potential security incidents.
Regular Security Assessments. Conduct regular vulnerability assessments and penetration testing to identify and remediate security weaknesses.
Secure APIs. Implement strong security measures for APIs, including authentication, authorization, and encryption, to prevent unauthorized access and data breaches.
Incident Response Plan. Develop and maintain an incident response plan to quickly address and mitigate the impact of security breaches.
Backup and Recovery Plans. Ensure regular backups of critical data and have a recovery plan in place to restore data and services in case of an attack.
Vendor Management. Assess the security practices of your SaaS provider and ensure they comply with industry standards and regulatory requirements.
Compliance with Regulations. Ensure your SaaS usage complies with relevant regulations and standards (e.g., GDPR, HIPAA) to avoid legal and financial penalties.
Behavioral Analytics. Use behavioral analytics to detect unusual user behavior that might indicate a compromised account.
Zero Trust Model. Adopt a Zero Trust security model, where every access request is verified and authenticated regardless of its origin.
Patch Management. Regularly update and patch SaaS applications to fix vulnerabilities and protect against known exploits.
How Does AppOmni Help Prevent SaaS Attacks?
AppOmni provides SaaS Security Posture Management (SSPM) with comprehensive threat detection, offering detailed visibility into cloud and SaaS activities and event streams to identify potential threats. AppOmni provides visibility, exposure prevention, threat detection, and remediation to secure data and help teams maintain compliance. We do this by continuously monitoring your SaaS platforms against security policies, automatically alerting you if suspicious activities—like multiple failed login attempts from various IP addresses in quick succession—are detected.
Discover the advanced insights offered by AppOmni’s threat detection, and learn how the SaaS security platform helps keep your SaaS attack surface threat free.