SaaS Risk Assessment
Conduct your SaaS security risk assessment with a robust SSPM solution.
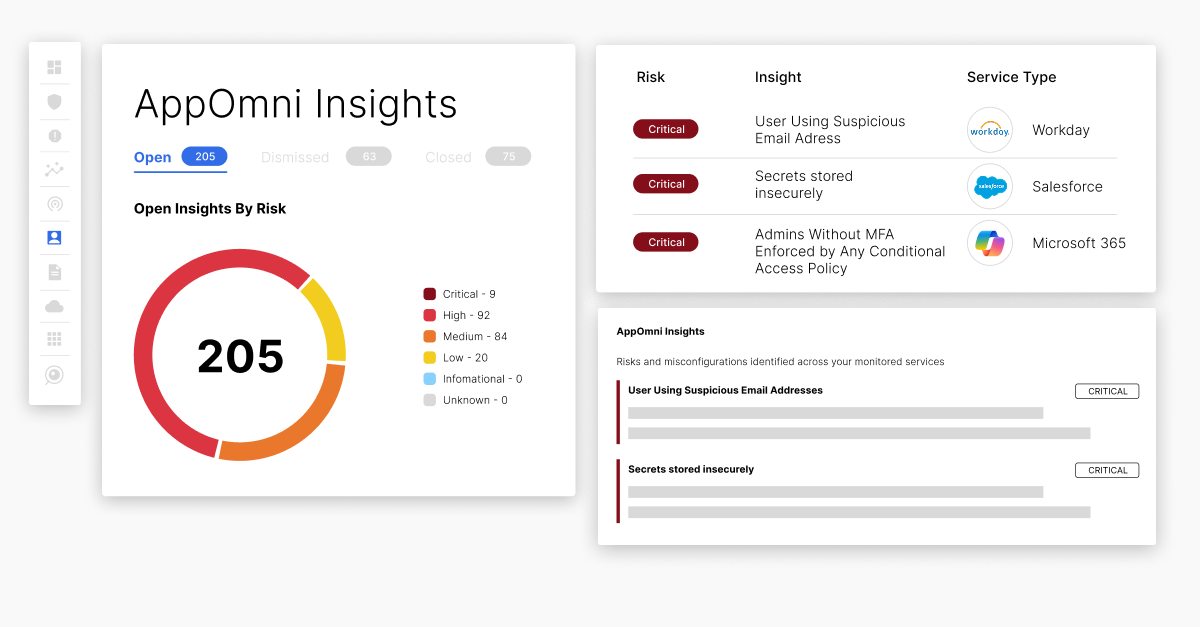
Eliminate SaaS risks hidden in your expanding attack surface
As organizations embrace the benefits of a distributed workforce enabled by SaaS, they need to remove blind spots in their attack surface caused by unmanaged SaaS. AppOmni provides continuous threat exposure management and identifies exposures created by SaaS misconfigurations, improper permissions, and third-party connections so you can proactively remediate issues.

Third-party application connections

Out-of-the-box compliance frameworks

Automation

Triage and remediation guidance
What are the major security risks in a SaaS model?
While SaaS platforms offer scalability and convenience, they also introduce a unique set of security challenges. From shadow IT to insider threats, learn about potential threats and vulnerabilities that arise when organizations use cloud-based apps to store, manage, and transmit sensitive data, workflows, and crown jewels.
How AppOmni helps uncover and remediate SaaS risks from misconfigs to shadow apps
See AppOmni in action
AppOmni’s agentless architecture delivers continuous SaaS and AI security monitoring with timely insights and remediation guidelines to help you prevent data breaches. The platform provides a central control point for all managed SaaS applications in your organization.
Latest Resources
-
AdExchanger Data Privacy Roundup
Costello sees a broader pattern of SaaS vendors racing to bolt AI onto everything. In that rush, security is a lower priority.
-
New phishing campaign tricks employees into bypassing Microsoft 365 MFA
Cory Michal, CSO at AppOmni, said attacks often leverage OAuth tokens and service/integration identities because they’re a blind spot for many orgs.
-
Identity Crisis: Why SaaS Attacks Are Bypassing Your Best Defenses
To help build a solid foundation for AI adoption, IM firms should source high-quality data, use modern data cloud/hybrid infrastructure, and adopt robust data governance principles.


