User Roles and Least Privilege in SaaS Apps
Learn all about user roles and the principle of least privilege (PoLP) in the context of SaaS application security.
SaaS security is a type of cyber security that is intended to protect SaaS provider-hosted applications. Typically, SaaS security measures include access controls, authentication, and, encryption, and identities, configuration drift, event monitoring, and compliance reporting the platform.
Any SaaS security model should have several key functions:
Each SaaS security framework is different, but most should offer these features.
SaaS security helps users achieve several key goals:
According to IBM, the average global cost of data breaches is $4.24 million; however, that number alone fails to account for other costs. Successful approaches to SaaS security issues and solutions should also minimize potential penalties for non-compliance, productivity losses, recovery and legal costs, reputational damage, and the loss of sales prospects a data breach may cause.
Government and industry best practices call for a shared responsibility model for managing SaaS security threats. In the shared responsibility model, cloud providers, customers, and product vendors each assume responsibility for the security measures that fall under their control.
In the context of SaaS security concerns, the application provider is responsible for all physical infrastructure, as well as the network, OS, and application. The customer is responsible for data security and identity management.
However, SaaS technologies have been adopted too rapidly for security teams to outpace the new risks they present, including:
Out-of-the-box security settings may not comply with organizational standards and customization makes security more challenging.
A report by Oracle and ESG found that 66 percent of all organizations are confused by the shared responsibility model for SaaS security monitoring. That means organizations are not fully securing the SaaS elements they’re responsible for in the shared responsibility model—putting their data at risk.
With many SaaS applications, “installation” is as simple as entering a credit card number to purchase. Nearly instantaneously, a team, office, or entire business can start using a feature-rich productivity application that hosts sensitive data and is accessible from anywhere, on any device in the world.
The flexibility and customizability of SaaS, coupled with economies of scale, make it a game-changer for productivity. However, those same characteristics make SaaS applications challenging to secure. Gone are the days when a security team could simply rely on a network perimeter to keep sensitive data internal.
SaaS cloud security measures are specifically tailored for platforms and applications hosted and delivered through cloud service providers. They secure the underlying cloud infrastructure, the platforms that run SaaS applications, and the data centers or servers that host them.
Cloud SaaS security addresses not only security for the application but also for the broader cloud environment where it operates.
SaaS security refers specifically to measures and practices that secure software applications delivered as a service (SaaS). It includes any security designed to protect software, whether it is hosted on-premises or in the cloud.
A cloud access security broker (CASB) protects data stored or accessed from the cloud and governs cloud usage between users and providers of cloud services. CASBs offer visibility into cloud usage across an organization so administrators can monitor and control which cloud services are accessed, and by whom, how, when, and where.
They can monitor and control the movement of sensitive data and help enforce security policies and controls for cloud applications to protect data loss using encryption, tokenization, or data loss prevention capabilities. CASBs also enforce strong user authentication of the traffic coming from their network and access control mechanisms, and offer threat detection and monitoring for anomalous behavior, protecting against cloud-specific threats like insider threats, malware, or unauthorized access attempts.
SaaS platforms face a number of challenges inherent to cloud services. There are four principal SaaS security challenges:
In the past, organizations stored and managed applications and data on-site, giving IT and security complete visibility and control. Those same departments often selected the applications used by the entire organization. Any changes to the status quo typically required a lengthy governance approval and provisioning process.
Now, ease of deployment and low upfront cost have allowed many users to acquire SaaS applications using local budgets. These cloud applications fall outside the purview of IT or security, creating a “shadow IT” problem. Surveys have shown there can be more than 32 different billing owners for SaaS applications at the average mid-sized company.
The main problem with shadow IT in SaaS security is that executives—not experts well-versed in security—are in charge of ensuring that their applications are configured to function effectively and securely.
But how many non-IT or non-security leaders are equipped to implement appropriate security settings, let alone understand the shared responsibility model?
The group that could help in securing these applications—the CIO, CISO, or enterprise security team—might not even be aware that these applications are in use. And when they are aware, those teams often don’t have the access needed to monitor and manage the applications.
According to Gartner, enterprises today manage an average of over 125 different SaaS applications, each with hundreds of unique controls and settings that can be continually adjusted and tweaked to customize functionality. On top of that, each organization—and each group within an organization—has its own needs and challenges in securing SaaS.
Configuring these applications manually can be overwhelming for even the most experienced security teams. The sheer volume of SaaS applications and lack of consistency in settings makes it impossible for security teams to be experts in every application.
Balancing functionality and security is like dancing on a tightrope. Once a SaaS app is customized to deliver the most value and the desired custom functionality for the team using it, default settings don’t provide optimal security and may conflict with compliance requirements.
SaaS applications also interact with other SaaS apps or internal systems. All of this makes it nearly impossible to detect anomalies and investigate weak SaaS configurations across applications.
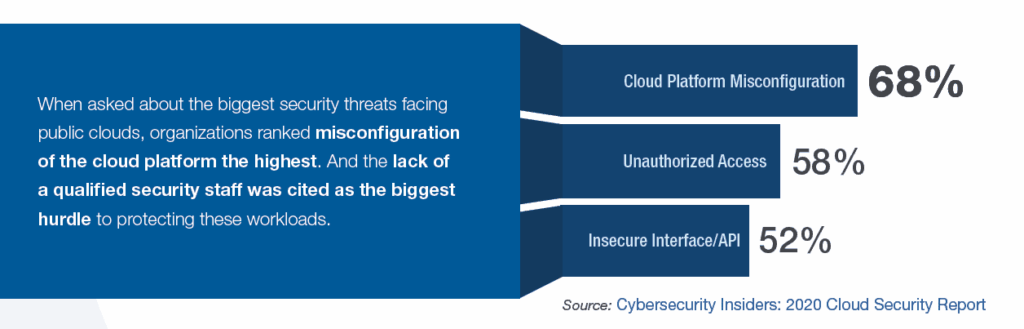
According to the Cybersecurity Insiders’ 2020 Cloud Security Report, organizations ranked misconfiguration of cloud platforms at the top of the list of SaaS security challenges facing public clouds. And the lack of a qualified security staff was cited as the biggest hurdle to protecting these environments. That combination can result in breaches that could have been avoided if appropriate security configurations were in place.
In dynamic business environments, anything and potentially everything can change daily. In today’s world of CI/CD (continuous integration/continuous delivery), SaaS security companies push code into production frequently, sometimes changing major functionality and operability—and often affecting security settings.
Personnel and their business roles change frequently as well, requiring new privileges for users. Security teams and administrators must have access privileges to make changes as the environment evolves.
The easiest way to ensure that the right teams have the permissions needed to support the environment is to allow broad access privileges. But SaaS security best practices call for limiting access privileges to only those who require them and revoking those privileges when they are no longer needed.
This simple concept may be difficult to execute. It can be challenging for managers to remember to downgrade user access when a project is done, for example, or for security teams to remember that increased access remains in place when it’s time to provision a new user.
Over time, manually managed applications experience configuration drift as the consequences of changed settings compound. And that configuration can expose data to internal and external threats.
Third-party integrations into SaaS applications can greatly enhance their functionality and capabilities but also increase the potential of improper exposure.
AppOmni’s data shows that on average, there are more than 42 distinct third-party applications connecting into live SaaS environments within an enterprise. Troublingly, About half are connected directly by end users, not IT or security administrators.
Many of these third-party security solutions can read, write, and delete sensitive data. They can also access user groups, workspaces, or multiple areas in the corporate network, including SaaS applications.
Multiple issues can arise with third-party apps, including uncertainty around knowing which apps are approved, what permissions an app has, and who can install an app. It’s also often unknown what users are doing with the data accessed by apps, since there’s no overarching SaaS security monitoring platform.
Data exposure prevention. Exposed data like shared credentials invites unauthorized access to SaaS applications. Strong SaaS security identifies critical gaps that expose data records publicly and allow data leakage.
Regular updates and patches. Updating software regularly and applying security patches fixes potential bugs and reduces the risk of exploitation by cyber threats.
Authentication and access control. SaaS security controls access across applications and deploy strong authentication.
Governance, risk, and compliance. SaaS security measures provide visibility into noncompliance in SaaS applications and associated policies to reduce risk of noncompliance.
Scalability and flexibility. SaaS security solutions can adapt to the evolving security landscape, allowing for scalable security measures to accommodate growing data volumes and diverse user needs.
Activity monitoring and analytics. SaaS platforms offer monitoring tools and analytics that track and identify potential security threats or unusual activities, enabling proactive measures against potential breaches holistically within your multi application environments.
Identities: Tie multiple identities together holistically to understand internal, external, and other types of sensitive access to development and or production environments.
Several common SaaS application security requirements should apply not only internally to the organization but also to all SaaS providers and vendors:
A robust, holistic SaaS security platform should focus on five key SaaS security strategies:
Refer to the SaaS security assessment checklist above to conduct a thorough SaaS security analysis.
Look for a SSPM tool that offers continuous monitoring and visibility to identify SaaS security risks and manage data access. Define a holistic compliance framework that best follows your business practices across your business critical SaaS apps to establish a robust security posture.
Embed expertise in the product with guidance and advice for the team so they may focus their time and energy on mitigating the highest risk misconfigurations and data exposures first:
Many organizations fail to pursue SaaS security any further than basic configuration management checks that are typically not implemented by security specialists. This leaves business-critical applications and sensitive data at risk.
A successful SaaS security program requires several additional components, including deep and broad security coverage for the entire SaaS ecosystem. Comprehensive security checks offer insight into integrations with the SaaS ecosystem and domains of risk.
Unlimited security checks for these areas are essential:
Verify that any SaaS security program under consideration supports third-party application management for all connecting third party apps. Inventory all installed third-party party apps and control access levels for SaaS-to-SaaS connections.
Track and monitor all SaaS-to-SaaS app access through comprehensive security checks to have a full understanding of your risk exposure. Look for an SSPM solution that is equipped with the following third-party monitoring tools to prevent unauthorized access:
Verify that any SaaS security program in use supports data access management. Quickly identify exposed SaaS data online and other critical instances of data leakage to achieve full control over user data access and actions.
Look for an SSPM solution that allows users to offer specific levels of access to each end-user with granular roles and robust environment restrictions while safeguarding sensitive data. Other important functionalities include:
Embrace automated tools that continuously monitor configuration settings in SaaS platforms. Act on misconfigurations, threats and or suspicious activity from alerts and have guided remediation steps on how you can mitigate that risk. Gain the ability to monitor suspicious security related events that may have fallen through the cracks. Create an automated security workflow that provides a structured way to detect, protect against, respond to SaaS security threats and events.
These workflows create and enforce consistent data access policies across all SaaS applications to detect possible areas of exposure, including:
DevSecOps shortens the development cycle while maintaining enterprise-level quality control. It is essential to use an SSPM solution in the secure software development lifecycle.
DevSecOps provides automation, continuous monitoring, and better communication between teams and ensures that security can be integrated in all project phases:
Establish and manage a SaaS assurance or governance plan with security measures that reduces the risk associated with SaaS apps. The plan should include documentation, compliance frameworks, and due diligence for ongoing risk reduction and monitoring, including:
The right system requirements and guided onboarding capabilities can set a SaaS security program up for success. A SaaS security solution should be quick and easy to deploy and allow the security team to add and monitor new applications as the SaaS environment grows.
Other important features include:
The specific strategies and tactics for implementing best practices for SaaS security include:
Some basic SaaS application security standards include:
Here are some of the key SaaS security trends experts observed in 2025:
What do these insights mean for organizations moving forward?
Despite the reassurance SaaS vendors may provide, end-users often overlook their cybersecurity responsibilities to secure their apps and associated data. The shared responsibility model tackles this specific issue.
Automated SaaS security posture management (SSPM) solutions with continuous monitoring capabilities ensure proactive detection of misconfigurations that then lead to data exposure. Together, these trend-based tactics provide a smarter approach to SaaS security.
SaaS Security Posture Management (SSPM) helps with understanding mis-configured environments from a multi application perspective. Through features like user management, configuration management, and event monitoring management, an SSPM platform can securely manage an organization’s SaaS estate by identifying risky configurations — and detecting security risks that may compromise sensitive data.
By continuously monitoring your SaaS applications for risks, a SSPM solution can mitigate potential security issues such as malware and phishing before they turn into significant and costly data breaches.
When choosing an SSPM security platform, a complete SaaS security solution is needed in order to provide comprehensive security to SaaS applications. A comprehensive SaaS security solution like an SSPM means gaining control of a company’s lifeblood – its sensitive data, work, product, and employee communication, just to name a few critical pieces of tech infrastructure.
CASB (cloud access security brokers), a common SaaS security standard, focuses on protecting internal resources from external threats and securing and brokering access to the perimeter of the cloud. However, while CASBs can inspect network traffic moving through proxy/access gateways, they cannot offer visibility into other traffic coming from within the application.
Larger SaaS providers sometimes offer native tooling to help secure their specific applications, yet levels of native security functionality vary from provider to provider, and each application has its own terminology and interface, with an associated learning curve. Additionally, the average mid-sized enterprise owns more than 185 SaaS applications, with no clear sense of whose responsibility it is to ensure security compliance for any given app.
SaaS security posture management is the answer to these challenges, and this is the foundation of the AppOmni approach to SaaS security. The strategy incorporates features of other point solutions, such as compliance and data security software, and builds on the strengths of existing solutions like CASBs—while keeping pace with the rapidly changing SaaS environments and addressing the unique challenges associated with each stakeholder’s responsibilities.
AppOmni’s SaaS Security Platform ensures universal coverage of all SaaS applications in several comprehensive steps:
Identify security trends. AppOmni— automatically updates with new best practices and detections from the experts—allow users to discover how rapidly the team is managing misconfigurations and other risks, closing issues, and tackling critical threat detection alerts.
Analyze open policy Issues coherently with a unified view. AppOmni presents a unified view into open issues across all SaaS applications. This quickly offers insight into where issues are located and their severity, their exposure to the public internet, and how they affect overall security posture.
Monitor controls continuously. With the AppOmni platform, users can consolidate findings and metrics across all monitored SaaS applications to discover permission levels for internal and external users and risk levels for all connected 3rd party applications.
Investigate third-party apps. The AppOmni approach enables users to inventory every add-on, API extension, 3rd party integration, and utility connected to organizational SaaS applications to visualize any risk of data exposure.
Detect and act on threats immediately. Automatically normalize event logs and aggregate SaaS activities to enable better, more rapid decisions. Develop custom rules for threat detection to address unique organizational scenarios.
Route alerts to trusted tools. Use existing workflows to respond to potential threats. Events that may indicate potential threats should route directly into data management tools such as security orchestration, automation, and response (SOAR), security information and event management (SIEM), and user and entity behavior analytics (UEBA) solutions.
Continuously monitor compliance. The AppOmni platform offers a snapshot of adherence and compliance policy across SaaS applications that may be filtered by common frameworks for compliance such as APRA CPS 234, ISO 27001, NIST CSF, NIST 800-53, SOX, SOC 2, and more.
Learn more about the AppOmni approach to SaaS security management here.