What’s the difference? How can cybersecurity teams navigate a balance?
- Focusing on depth over breadth ensures thorough protection for critical SaaS applications, safeguarding the most sensitive data and systems from sophisticated attacks.
- AppOmni’s depth-first approach integrates detailed posture rules, actionable insights, threat detection, and granular data access monitoring, offering robust and adaptable protection for critical SaaS platforms.
The age-old debate of breadth vs depth is once again a challenge for security organizations as they consider adding SaaS security management capabilities to their overall cybersecurity program. Some opt to spread their resources across a broad array of SaaS tools and applications to ensure comprehensive coverage. While others prioritize depth by investing time and effort to securing the most critical SaaS applications.
Breadth may seem appealing as it extends a level of security to all SaaS systems, but it won’t provide maximum protection for the most business-critical SaaS platforms.
This blog explores why focusing on depth, versus breadth, when building a SaaS security program is the most effective option for providing real security to critical data. Focusing only on breadth often leaves the most sensitive data and connected systems still exposed.
What’s the difference between breadth and depth in SaaS security?
In cybersecurity, breadth ensures that all systems, regardless of their criticality, receive some level of protection. It casts a wide net to catch some security threats from as many systems as possible across the organization. By focusing on scope of coverage, this approach provides comprehensive visibility and conducts basic security checks for all apps.
Instead of spreading efforts across disparate systems with lightweight checks and controls, a depth-focused approach prioritizes complex use cases and deeper security checks on the most important and sensitive systems, often categorized by size, scope, type of data stored, and business impact.
Depth-focused SaaS security management solutions go beyond monitoring basic user attributes via common APIs. They invest significant research and development in understanding the complexities of specific, highly sensitive SaaS applications. This dedicated investment, often lacking in breadth-focused approaches, supports individual applications rather than providing generic support for many.
To defend against sophisticated attack mechanisms and threats, depth-focused solutions prioritize dedicated threat research on specific SaaS app attack vectors and the development of related detection rules and insights. They also offer complex, customizable support for various access rights assignment mechanisms and RBAC roles.
Which strategy is best to help you achieve SaaS security?
Prioritize your most critical SaaS apps first
At first glance, covering a range of applications seems like the best move for your organization. But, threat actors typically target systems where they can access the most valuable information, which is often stored not in smaller, less critical apps but in high-value applications. According to the Verizon Data Breach Investigations Report, approximately 70% of breaches involve these crucial systems where financial data or PII is processed and stored.
Smaller applications, which tend to handle less business-critical data are generally less appealing targets for significant cyberattacks. Instead of spreading resources thinly across every SaaS app, organizations should focus on security measures that more fully monitor critical systems where the impact of a potential breach could be severe.
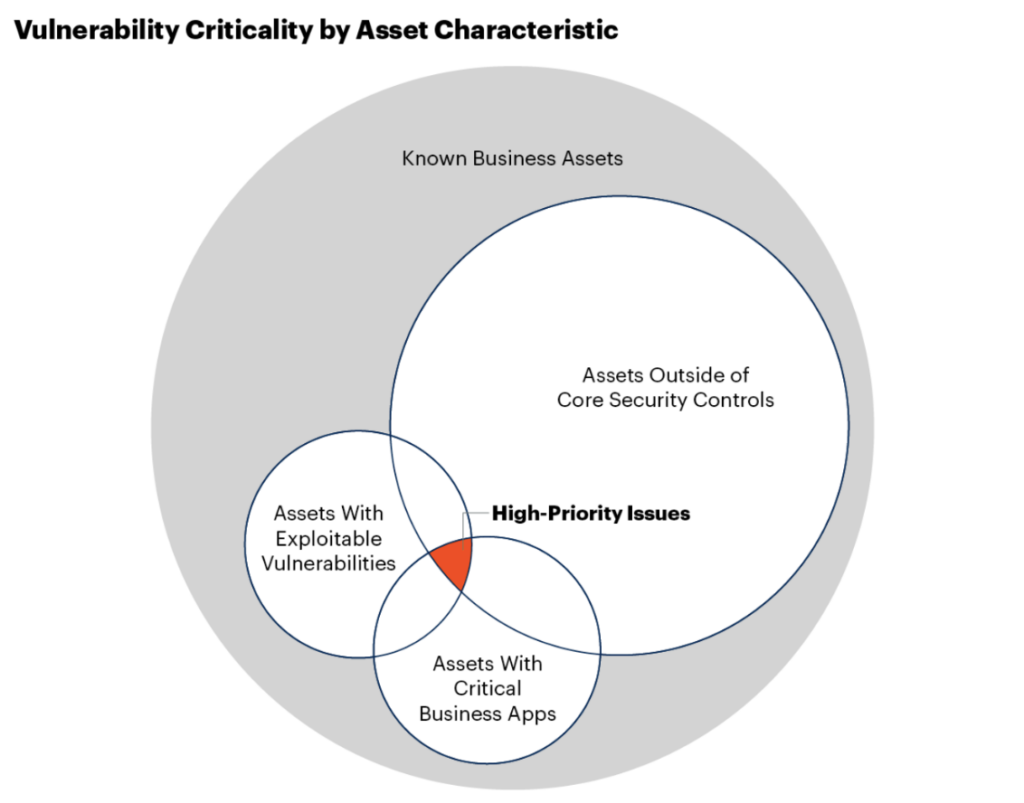
Ensuring data security in apps such as Microsoft 365, Salesforce, and ServiceNow is your best bet. These platforms manage large amounts of sensitive data and are integral to key business processes. They require continuous visibility and monitoring for secure SaaS productivity. Taking a surface-level security approach just won’t cut it.
Start your SaaS security journey with depth
When choosing a SaaS security platform, consider a solution that takes a comprehensive approach to SaaS security. While the number of posture checks is important, prioritize an SSPM solution that integrates identity data, threat detection, and continuous monitoring of SaaS-to-SaaS connections. Though, those looking into SSPMs should also be aware that it’s not all about the number of checks per app. It’s the complete picture, how a platform brings together the information and creates customization to meet your needs. Ensure a depth-first SaaS security strategy by finding a holistic SSPM solution with the following capabilities:
- Posture Rules: These are numerous configurations and policy checks designed to manage and secure various aspects of SaaS applications effectively.
- Insights/Content: Identifies toxic combinations of configurations (vs binary checks) and includes tailored recommendations and actionable guidance based on the latest security research.
- Detection Rules: These rules actively monitor for anomalies and threats, enabling quick identification and mitigation of potential risks.
- Data Access Monitoring: It scrutinizes data exposure and sharing activities within SaaS platforms to prevent unauthorized data exposure and ensure compliance with data protection regulations.
Together, these components ensure a robust defense against a wide spectrum of threats, contributing to a secure and compliant SaaS environment.
Extend breadth to other SaaS apps with The AppOmni Developer Platform
While the AppOmni platform takes a depth-first approach, we understand that your organization may have other high-priority SaaS applications to protect. The AppOmni Developer Platform extends our security insights to other SaaS applications not directly covered out of the box. It allows you to customize and extend security monitoring and management capabilities, ensuring comprehensive protection for every application, no matter its popularity or ubiquity.
AppOmni combines depth and breadth for comprehensive SaaS security
As the market leader in SaaS security, AppOmni prioritizes a comprehensive and strategic deployment of security measures to help you achieve SaaS security.
At AppOmni, depth isn’t just about the quantity of security checks. Rather, it’s about the integration and effectiveness of those security checks in real-world scenarios. The AppOmni platform focuses on the integration of posture rules, actionable insights, threat detection, and granular data access monitoring to enhance your SaaS security posture.
AppOmni tailors security strategies to the unique needs of each organization, allowing you to operate your SaaS systems securely and confidently. With AppOmni, your business-critical data is secured with a thorough and adaptable depth of protection to guard against both current and emerging threats.
Conclusion
Maintaining a broad security perspective is essential, but depth of security is crucial to securing high-value applications vital to business operations. Threat actors target these high-stakes applications to maximize their impact. Organizations must allocate their resources to these critical applications to safeguard against sophisticated and targeted threats.
AppOmni’s depth-first approach, combined with the flexibility of the AppOmni Developer Platform, helps businesses achieve both breadth and depth in their SaaS security strategies.

SaaS Security Buyer’s Guide
Accelerate your organization’s SaaS security journey with a detailed criteria for choosing the right SaaS Security Posture Management (SSPM) platform.
Additional Resources
-

Zoom Breach at Federal Reserve Shows the Need for SaaS Security
A SaaS security misconfiguration led to a high-profile Zoom bombing, preventing the Federal Governor from delivering his remarks at a virtual event.
-
Zero Trust’s Weak Spot: SaaS Apps Aren’t Playing By The Same Rules
Organizations that rely solely on ZTNA or similar network-focused defenses often mistakenly believe their SaaS applications are protected.
-
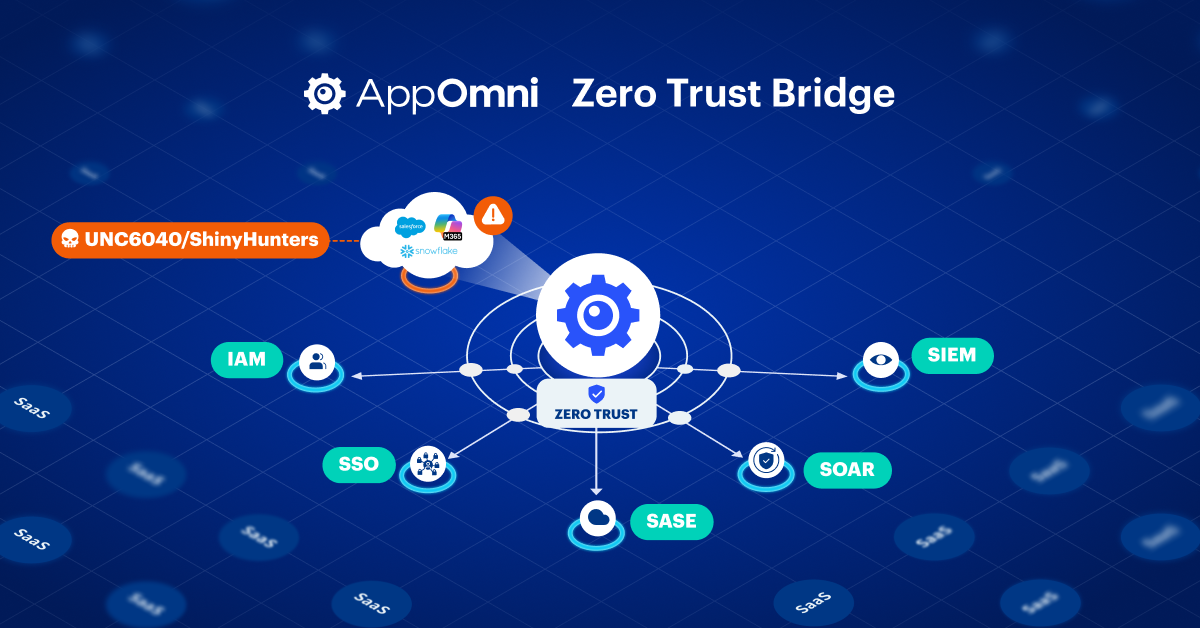
Zero Trust Needs a Bridge: How to Unlock Shared Signals for SaaS Now
Zero Trust Bridge activates shared signals in SaaS, boosting real-time risk detection with AppOmni.