See step-by-step how the identity-centric breach occurred, potentially exposing Okta customers to account takeovers.
The Okta HAR breach has left Okta customers potentially exposed to takeovers of their Okta environments. Attackers have been attempting to target Okta customers and leverage highly privileged accounts in order to compromise IdP instances and connected applications. This post covers how enterprise SaaS Security Posture Management (SSPM) platforms already have many capabilities today to detect and prevent the tactics that attackers are attempting from being successful.
Summary
On October 20, 2023, Okta reported that its customer support system was breached, which resulted in the theft of HAR files (i.e. HTTP Archive) uploaded by its customers (NOTE: it appears highly likely that the support system itself was a SaaS provider). These HAR files are used for support session browser recordings but can contain sensitive session cookies and tokens. As a result of this data theft, attackers have moved to targeting Okta’s customer base to gain control of their identity instances and associated applications.
BeyondTrust also reported on the same day that it had detected attacks that were leveraging the stolen HAR files on October 2, 2023, and this was confirmed by Okta on October 19, 2023.
Using the token extracted from Okta, the attackers also accessed CloudFlare systems on October 18, 2023 where they compromised two separate Cloudflare employee accounts within Okta.
Most recently, 1Password announced that they have been breached via these tactics, so customers should treat this as an active exploit.
This post details common attack patterns we’re observing and how SaaS Security Posture Management (SSPM) can detect and prevent attackers from leveraging these types of tactics against their Okta instances.
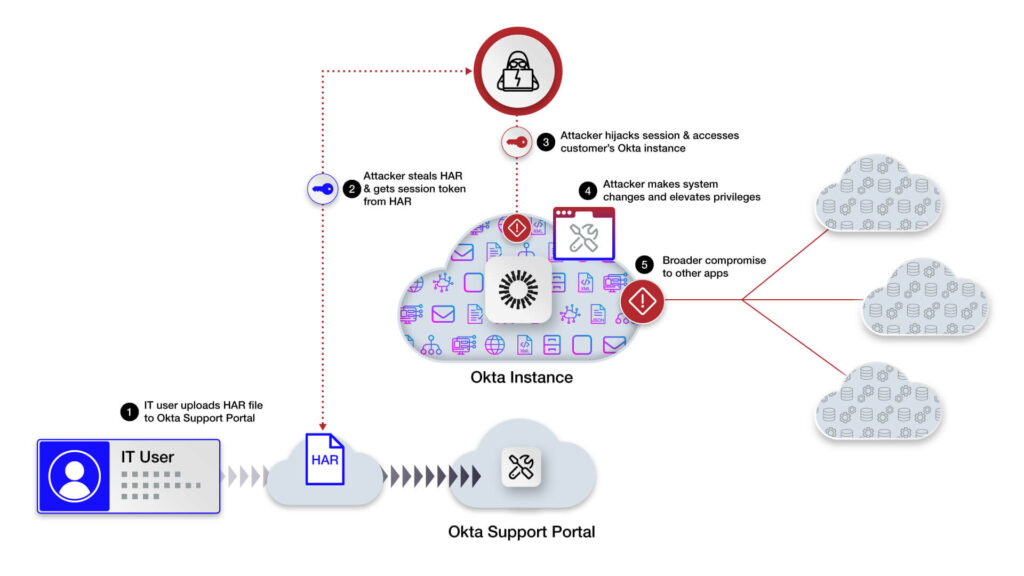
The Okta HAR Breach: Common Attacker Tactics
Attackers are using the stolen HAR files to conduct session hijacks of Okta customers to gain access to the respective customer’s IdP environment. This attack is leveraging session tokens in the HAR files that may not have been sanitized before submission.
It allows the attacker to re-use or hijack an existing support session that is already authenticated into an Okta environment. In addition, most personnel interacting with Okta support have an elevated or administrative permissions profile that allows for creation and modification policies and policy rules within Okta.
A common attack pattern that is being observed may use the following tactics:
- The attacker uses a session from one of the HAR files to get into the customer’s Okta tenant via console or API.
- The attacker enables an account of an inactive user or creates a new user.
- The attacker then modifies MFA settings to add their own controlled tokens.
- Attacker switches accounts to the previously inactive account.
- Attacker then attempts to disable MFA on other IT/Security accounts
- All the traffic was coming from Browsec VPN egress, often used to anonymize the originating source for nefarious purposes.
Watch this step-by-step video to learn how the Okta HAR breach happened.
How SSPM Can Help
An enterprise SSPM platform can help secure Okta environments by proactively securing and continuously monitoring the attack surface and security configurations of an Okta instance. SSPM can also alert on specific threat events or anomalous activity detected from a customer Okta instance.
Given the types of tactics that have been observed and reported, below is a partial listing of the types of alerts and monitoring an SSPM solution could provide to detect and prevent takeovers of an Okta environment. SSPM solutions can also provide complete activity monitoring visibility into SaaS events and anomalous access.
1. Alerts on MFA Policy Modifications: An SSPM can monitor and alert on any modifications or new creations of MFA policies and policy rules. This can help organizations quickly respond to unauthorized changes and potential security breaches.
Example of an SSPM MFA Hardware Key-based Policy Finding:

2. Password Setting Changes and Role Modifications: An SSPM can also track any alterations to password settings, role assignments, and administrative group changes within the Okta environment. This level of visibility is crucial to ensure the integrity of access controls.
Example of an SSPM Role Modification Finding:

3. User MFA Updates and Activity Alerts: With an SSPM, you can keep track of user MFA updates and activity. This allows organizations to identify any abnormal behavior or changes in MFA usage, signaling potential threats.
Example of threat detection alert on privilege grants:
Example of threat detection alert on Administrator impersonation:

4. Application Specific Settings Monitoring: Okta’s application-specific settings are critical to the overall security of your identity management system. An SSPM can detect any unauthorized changes, ensuring the confidentiality and availability of these settings.
5. Alerts on OAuth Settings Modifications: Monitoring OAuth settings is vital for preventing unauthorized access and data breaches. An SSPM can promptly alert administrators to any changes in OAuth settings.
6. MFA Status Tracking: A robust SSPM solution will trigger alerts for user accounts without MFA enabled. This ensures that every user follows the organization’s security policy, reducing the risk of unauthorized access.
7. Complex MFA Bypass Detection: SSPM solutions can detect complex MFA bypass techniques and alert administrators to such suspicious activities, providing a proactive defense against sophisticated threats much like this recent breach.
8. Detect Activity from Suspect Proxies/VPNs: SSPM solutions can provide full SaaS activity monitoring including source IP and geolocation information. This can be used to identify suspicious source traffic or known IOCs.
It is important to note that not all SSPM solutions comprehensively monitor SaaS applications such as Okta in-depth – many may take a superficial approach that can leave you exposed to these types of attacks. Other considerations: how well the solution integrates and normalizes activity data for better correlation with your existing set of security solutions.
AppOmni offers real-time alerts on configuration drift or modifications to MFA policy changes, password settings, role modifications, application-specific settings, OAuth changes, and more, enabling organizations to maintain the highest level of security and respond swiftly to any potential threats. The Okta breach serves as a reminder that securing identity and access management systems and other business-critical SaaS apps is a top priority in today’s digital landscape.
Conclusion
In the wake of the Okta breach, it’s evident that organizations must be vigilant and proactive in protecting their identity and access management systems. A SaaS Security Posture Management (SSPM) solution that provides comprehensive monitoring and alerting capabilities, such as AppOmni, is the ideal choice for bolstering security.
AppOmni has the most comprehensive dataset and scope of visibility on SaaS security. Our solution is used by over 20 percent of the Fortune 100 and monitors over 1 billion SaaS events per day.
AppOmni was founded to address this SaaS security risk and is a vital tool in achieving this goal. See why leading global enterprises choose AppOmni as their SaaS security solution of choice. Get a free risk assessment to find out who has access to your SaaS data.

What is SSPM?
SaaS applications need a virtual command room where security teams can manage their complex SaaS estate securely and holistically. Learn what makes a robust SaaS Security Posture Management (SSPM) solution and its key capabilities.
Related Resources
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-

Start Smart, Scale Fast: AppOmni’s SaaS Security Packages Explained
AppOmni SaaS security maturity packages simplify risk reduction and compliance for all stages.
-

Securing AI in SaaS: No New Playbook Required
Say yes to AI, no to risks. AppOmni’s AI security solution overview breaks it down with smart discovery workflows and real-time threat detection.