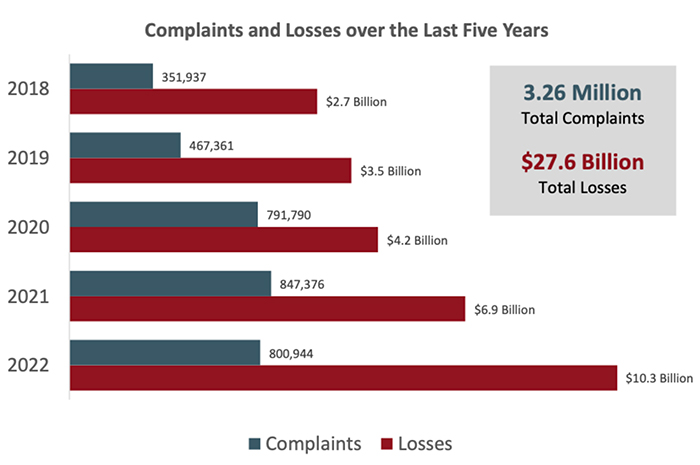
The FBI recently released its 2022 Internet Crime Report, which shows that losses from cybercrime last year reached $10.3 billion, up from $6.9 billion in 2021. This amounts to a staggering 49% increase in damages year-over-year.
What is the main culprit for these crimes, and the financial damage exacted? Social engineering attacks, mainly in the form of phishing, are the most reported cybercrime. And there is little doubt that the mainstream release of AI text tools like ChatGPT will further improve the sophistication and success of phishing attacks, becoming an important augmentor for threat actors.
Read on to see why the relationship between social engineering attacks and insufficient SaaS security is clear. And why robust SaaS security monitoring is fast becoming a critical pillar in the enterprise security stack to thwart attacks and their high cost to business.
Costs of Cybercrime are Skyrocketing
The financial toll of cybercrime is increasing at a significant pace, even as the total number of crimes reported marginally decreased year-over-year. The FBI reports that total costs from cybercrime for the current five-year period (2018-2022) reached $27.6 billion.
Business email compromise, which the FBI defines as “a sophisticated scam targeting both businesses and individuals performing transfers,” alone accounted for adjusted losses of over $2.7 billion in 2022. While consumer-oriented phishing scams receive more media attention, enterprises and SMBs alike are consistent and constant targets of social engineering.
Social Engineering is a Leading Threat to the Enterprise
Phishing is by far the leading cybercrime, with over 300,000 incidents reported in 2022. But it’s important to provide a caveat for the self-reporting of crime statistics, as there is usually a relatively significant margin of under-reporting. Hence the figure of actual cybercrime damages sustained by victims is likely higher.
What makes social engineering in the form of phishing so attractive to threat actors is the low barrier to entry and the high degree of success. Typically, threat actors that rely on social engineering are after three objectives: establishing initial access, stealing data, and/or achieving financial gain (e.g., perpetrating invoice and wire fraud). Often the motives such as data theft and financial gain overlap.
For the enterprise, phishing is usually perpetrated to gain initial access via account takeover (ATO). Once access is achieved, the threat actor is able to move laterally within the organization to access and exfiltrate data at will, often going undetected for months or years at a time.
What makes phishing attacks even more dangerous to the enterprise is poorly secured environments. This can include poor access control, over-privileged users, a lack of network segmentation, and critically no visibility over the SaaS estate.
In forensic analysis of a breach, such as successfully phishing for credentials, the harvesting of authentication codes is frequently determined as the leading attack vector that resulted in the compromise. And often with devastating consequences.
There have been several high-profile incidents where employees at leading SaaS companies were targeted in phishing attacks, such as the compromise of a Microsoft employee in 2022 that resulted in the threat actor accessing Microsoft’s source code.
The Challenge and Risk of Unsecured SaaS
The challenge and risk of not monitoring your SaaS environment with a purpose-built SaaS Security Posture Management (SSPM) solution are that you have no SaaS event observability or telemetry. This can be equated to flying blind from a risk standpoint.
Existing security tools such as Cloud Access Security Brokers (CASBs) or Secure Web Gateways (SWGs) focus on governing cloud security access, but they are unable to detect any suspicious SaaS-to-SaaS activity, including 3rd party application integrations. This presents a major shortcoming in securing the SaaS ecosystem.
For example, say a threat actor has successfully phished the credentials and compromised a SaaS solution provider, like payroll or people management, that you happen to use in your environment. There is no way to detect the threat actor leveraging that initial access to attack your SaaS instance in that service provider’s environment.
Another attack scenario could be the threat actor leveraging a compromised 3rd party app extension used in one of your SaaS tools. This can enable the threat actor to gain access into your SaaS environment.
Without any continuous SaaS monitoring capability, you have no way of knowing that your SaaS environment has been compromised.
Focus on SaaS Security
SaaS adoption is rapidly accelerating and, according to Gartner, has been the leading driver of cloud services growth since 2016. This means that the era of not prioritizing SaaS as a leading threat vector in the enterprise is over.
AppOmni was founded to address this SaaS security risk. As the leader in SaaS security and a top choice for Fortune 500 clients, AppOmni is on a mission to create a safer SaaS world.
See why some of the leading enterprises in the world have chosen AppOmni as their SaaS security solution of choice. Schedule a demo today.
Related Resources
-
How to Investigate Suspicious User Activity Across Multiple SaaS Applications
Discover practical strategies security teams can use to investigate suspicious activity across SaaS apps, reduce alert noise, and respond to real threats faster.
-

Low-Code, High Stakes: Why Security Can’t Be an Afterthought for Customers Using Salesforce Industry Clouds
New research reveals critical security flaws in Salesforce industry clouds. Discover the risks and how to protect your organization now.
-

OAuth Tokens: The Danger Behind the Commvault Breach
Discover what went wrong in the Commvault breach: How AppOmni’s powerful SaaS security platform steps in to stop threats before they strike.
 New research drives security enhancements for Salesforce industry clouds
New research drives security enhancements for Salesforce industry clouds