Five critical steps to strengthen your organization’s security culture, protect sensitive patient data, and maintain regulatory compliance.
SaaS applications, wearables, and IoT devices paired with telehealth systems provide healthcare providers with greater access to patient data more than ever. But they also require instantaneous, real-time data access that’s highly susceptible to compromise.
The lack of SaaS data security was exacerbated as healthcare organizations rushed to introduce virtual care services during the early days of the pandemic. While cybersecurity safeguards were lifted and underfunded, data protection noncompliance penalties have been reinstated as global public health emergency declarations ended. The financial penalty for regulatory non-compliance depends on the level of negligence and can range between $100 to $50,000 per violation.
With stakes so high and patients expressing deep concern about data privacy, how can security leaders and IT teams protect sensitive patient healthcare information (PHI) and maintain regulatory compliance?
Five Critical Steps to Securing Healthcare SaaS
To strengthen your organization’s posture and ensure protection of valuable PHI, consider enforcing these steps within your organization:
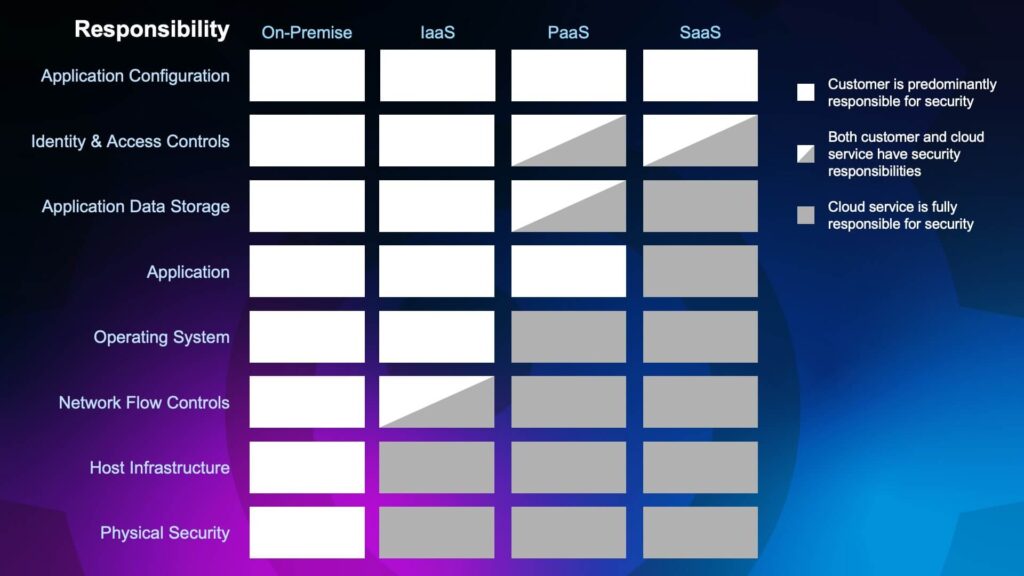
1. Review and understand the shared responsibility model.
While SaaS providers must monitor and respond to security threats related to their application’s underlying infrastructure, healthcare organizations should maintain security controls and appropriate user access settings to protect sensitive data. This includes the CIA triad: confidentiality, integrity, and availability throughout the app lifecycle, including system configuration settings, user permissions, role-based access control (RBAC) models, and SaaS-to-SaaS application integrations.
2. Identify which SaaS apps house your crown jewels.
Conduct an audit to see and understand which SaaS apps store, maintain, and transmit assets that are critical to your organization’s daily operations. Threat actors tend to prey on security misconfigurations, over permissioned users, and/or vulnerable SaaS-to-SaaS connections as means to accessing your crown jewels.
3. Review business partner and SaaS provider agreements.
Take a look at the entire patient experience and map every interaction back to one of the SaaS-to-SaaS connections or SaaS apps you use. This data-matching exercise will not only reveal the precise location of where your sensitive data lives, but also indicate where the largest quantity of data exists across online platforms and SaaS apps.
4. Craft your SaaS governance framework.
Patient care is no longer bound to a centralized corporate network protected by firewalls and cloud-focused security tooling. To help control the sprawl of shadow IT, a centralized model could be necessary for organizations in highly regulated industries. Conversely, would a decentralized model alleviate overburdened IT teams by spreading the responsibility of SaaS stewardship? The key is to strike a balance between a centralized or decentralized model with nuanced SaaS governance.
5. Strengthen your security culture.
Socialize security training throughout your organization, particularly at the user level. Offer ongoing training and simulations to avoid phishing scams and social engineering attacks, spot potential malware behaviors that lead to account takeovers, and help adhere to data privacy and compliance regulations.
How AppOmni Empowers Security Leaders and IT Teams
Establishing SaaS governance and ensuring regulatory compliance is no small feat.
Annual vulnerability assessments and the point-in-time nature of pentests are insufficient in securing your entire SaaS environment. PHI and EHR (electronic health records) must be secured throughout the data lifecycle, from creation to archival.
Only a robust SaaS Security Posture Management (SSPM) solution like AppOmni can provide security leaders and IT teams with:
- Guidance on complex configuration settings and permission levels for internal and external users.
- Continuous monitoring of SaaS policy settings.
- Visibility into everything connected to your healthcare SaaS estate, including the level of data access each app has been granted.
- Prevention of cyber risk exposures stemming from data leaks and publicly exposed data records in SaaS environments.
- Detection of configuration drifts, or divergence from your organization’s baseline, that can lead to security vulnerabilities such as escalation of privilege.
Schedule a demo to see how AppOmni’s advanced security tooling can protect PHI across your entire SaaS ecosystem.
Related Resources
-
Achieving CISA BOD 25-01 Compliance and SCuBA Alignment
Learn how to achieve compliance for CISA’s BOD 25-01 and SCuBA alignment with AppOmni, updated for M365 SCuBA compliance checks.
-

How AppOmni and Cisco Advance Zero Trust SaaS Security
Learn how AppOmni’s SSPM and Cisco’s SSE create a unified Zero Trust security solution, bridging SaaS and cloud service vulnerabilities to protect critical data.
-

What 2024’s SaaS Breaches Mean for 2025 Cybersecurity
In this blog, we take a look at the most impactful SaaS security incidents in 2024 and share insights on what to expect in 2025 for SaaS security.
 Achieving CISA BOD 25-01 Compliance and SCuBA Alignment
Achieving CISA BOD 25-01 Compliance and SCuBA Alignment