SaaS (software as a service) applications are now the operating system of modern business. From email and collaboration to finance, HR, and customer data, critical operations now run on platforms like Microsoft 365, Salesforce, Workday, and ServiceNow. This shift creates new opportunities, but also new challenges for security teams. That’s where SaaS Security Posture Management (SSPM) comes into play.
As SaaS usage grows, so does its complexity. Many organizations today operate more than 100 SaaS applications across distributed teams, with varying ownership and inconsistent security practices. Native tools provide siloed views. Existing security solutions (like CASBs or CSPMs) focus on access control or infrastructure, but don’t secure the SaaS apps themselves. And while users may interact with SaaS through a browser or VPN, the real risks often lie within app settings, misconfigurations, and third-party integrations.
SSPM emerged to address these challenges. It’s a foundational capability for securing data, helping organizations gain visibility, enforce policy, and manage risk across the SaaS applications that drive business every day.
What is SaaS Security Posture Management?
SSPM is a category of security tooling focused specifically on the security posture of SaaS applications. At its core, SSPM helps security teams continuously monitor, evaluate, and manage how SaaS applications are configured and used. This includes checking for misconfigurations, tracking user access, evaluating third-party integrations, and detecting potentially risky behaviors.
It’s important to understand that SSPM isn’t just a set of security checks—it’s an operational capability. In the same way cloud security posture management (CSPM) tools brought visibility and control to infrastructure as a service (IaaS) environments, SSPM gives organizations a way to manage SaaS risk proactively, not reactively.
The need for SSPM has become clear as more companies realize that their most sensitive data (customer records, payroll info, product roadmaps, intellectual property) lives in SaaS. And often, that data is more exposed than they think.
What are the benefits of SSPM?
SaaS applications like Salesforce and Microsoft 365 have transformed how organizations create, share, and store information. But this transformation has also made SaaS environments one of the most critical parts of any enterprise’s digital footprint. SSPM provides the tools to protect it.
For security teams, this means moving from reactive app-by-app checks to a unified command center that surfaces the most important issues across the entire SaaS estate. It means spending less time tracking down settings and more time mitigating actual risk.
When implemented well, SSPM becomes a cornerstone of a company’s security plan. It provides not only visibility but also clear guidance on what to fix, why it matters, and how to maintain compliance and operational integrity as SaaS continues to scale.
The five pillars of effective SSPM
An effective SSPM solution delivers on five essential capabilities. These pillars form the foundation of any SaaS security strategy.
Configuration management: Catching misconfigurations before they cause harm
SaaS platforms offer tremendous flexibility. Admins can customize permissions, sharing settings, API access, and more. But that flexibility creates risk. A single misconfiguration (such as a public link sharing policy, a disabled MFA setting, or a permissive guest access role) can result in a major data exposure.
SSPM continuously monitors security-relevant configurations across applications, comparing them against industry best practices or your own internal policies. It alerts when configurations drift from secure baselines or when risky changes are made.
This matters because SaaS configurations are dynamic. They change frequently as admins deploy new features or respond to user requests. Without automated, continuous visibility, it’s nearly impossible to stay ahead of the changes that could create vulnerabilities.
Identity and access governance: Enforcing least privilege in a decentralized world
In SaaS, identity is the new perimeter. Understanding who has access, what level of access they have, and whether that access is appropriate is critical. But in large organizations, user roles are fluid, and different teams often manage different apps with different access models.
SSPM brings central oversight to this complexity. It maps roles and permissions across applications, identifies over-privileged accounts, flags orphaned or inactive users, and helps enforce least-privilege access.
This is essential because excess permissions are one of the most common contributors to data loss and privilege escalation. And in many SaaS platforms, permission inheritance and group nesting make it difficult to understand access relationships without purpose-built tools.
Threat detection and activity monitoring: Moving beyond logs to context
Traditional SIEMs and CASBs struggle with SaaS threat detection because SaaS logs are inconsistent, fragmented, and lack rich context. SSPM changes that by normalizing logs, correlating them with posture and identity data, and layering in behavioral analytics.
Effective SSPM platforms provide out-of-the-box detections for common SaaS attack patterns, like mass data downloads, OAuth token abuse, or privilege escalations. They also support custom rule creation, allowing teams to define what risky behavior looks like in their specific environment.
This capability is critical in today’s threat landscape. Attackers target SaaS apps because they’re often poorly monitored. And because users operate within trusted environments, risky actions can look like normal behavior—unless you have the context to know better.
SaaS-to-SaaS and third-party app management: Controlling invisible connections
Many SaaS platforms support third-party integrations via OAuth. These integrations can be powerful, but also dangerous. A marketing user might connect an email automation tool to Salesforce without security team’s knowledge. That tool might request full read/write access to customer data and retain it long after it’s no longer needed.
SSPM shines a light on these often invisible connections. It inventories all connected applications, evaluates the scopes and permissions granted, and flags integrations that represent excessive risk. Some platforms even allow teams to block or quarantine unauthorized apps.
This matters because third-party SaaS-to-SaaS connections bypass traditional network controls and exist outside of your firewall. Without visibility and control, they represent a growing vector for data leakage and supply chain compromise.
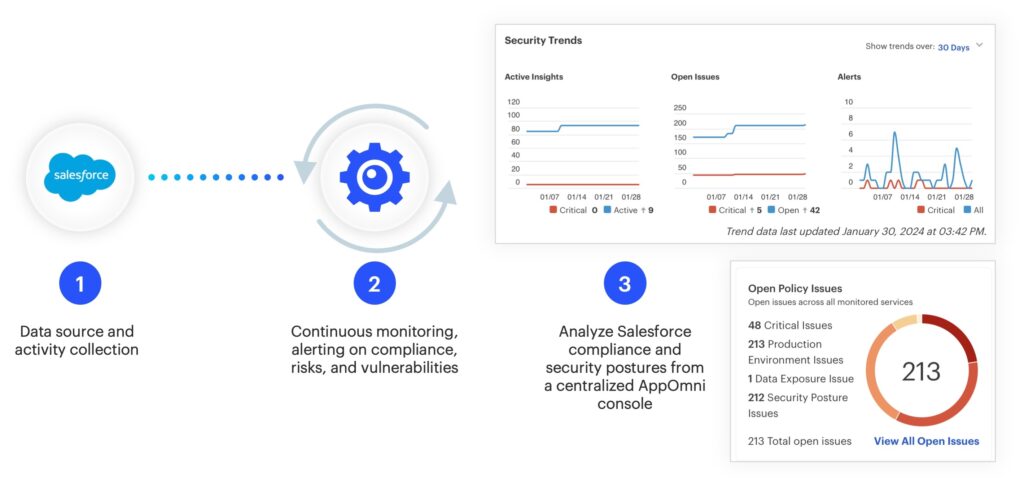
Governance, risk, and compliance: Simplifying the SaaS audit process
Many compliance frameworks now include requirements for SaaS security. Whether it’s s APRA CPS 234, ISO 27001, NIST CSF, NIST 800-53, SOX, and SOC 2, or internal policies, organizations must be able to demonstrate how they protect data across SaaS platforms.
SSPM simplifies this process. It continuously evaluates apps against policy baselines, provides reporting aligned with compliance controls, and generates audit-ready evidence without manual effort.
This isn’t just about ticking boxes. It’s about building a repeatable, scalable SaaS security program. With SSPM, security teams can stop chasing down screenshots and start proactively managing their compliance posture.

How SSPM fits into your broader security stack
SSPM solutions don’t replace any one particular element of your security framework; they instead fill the gap by providing deep, continuous security for SaaS platforms themselves. Think of it as the layer that secures what happens inside your SaaS apps—where your users work, where your data lives, and where attackers increasingly focus.
What is the difference between SSPM vs CASB vs CSPM?
SSPM doesn’t replace CASB or CSPM; it complements them.
- CSPMs (cloud security posture management solutions) focus on infrastructure—things like AWS or GCP—not business apps like Salesforce or Workday.
- CASBs (cloud access security brokers) help enforce access control and monitor traffic. But they can’t see inside SaaS apps to detect misconfigurations or permission risks.
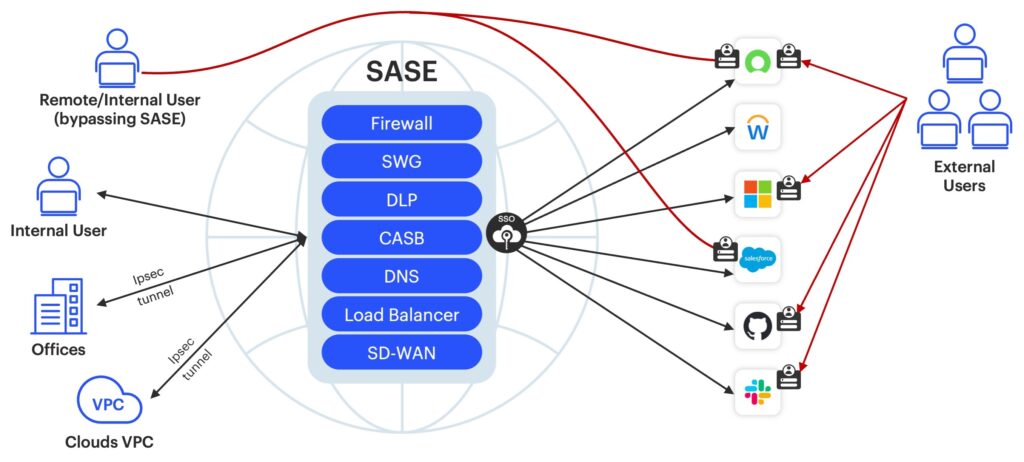
Where does SSPM fit within the larger context of SASE?
A comprehensive secure access service edge (SASE) framework combines networking and security capabilities into a single, cloud-based service model. SASE architecture often integrates multiple security and networking functionalities.
Some SASE functionalities, such as cloud access security brokers (CASBs) may be used with and overlap with SSPM solutions. Other functionalities associated with SASE architecture merely interface with SSPM tools, such as secure web gateways (SWG), and Zero Trust network access solutions (ZTNA).
SSPM vendors specifically address security posture of SaaS applications and ensure they adhere to access controls, compliance measures, security policies, and threat protection aligned within larger security goals of broader SASE architectures.
What is the difference between SSPM in-house solutions?
Larger SaaS providers may offer native security tooling for specific applications. However, levels of security functionality are inconsistent, and each app has its own terminology and interface. Even the average mid-sized enterprise owns over 185 SaaS applications, yet lacks clear roles for ensuring security compliance for these apps.
What is the difference between SSPM vs SIEM?
Like SSPM, security information and event management (SIEM), is a critical component of cybersecurity strategy. Unlike the more narrow SSPM focus on securing SaaS environments, SIEM more broadly collects and analyzes data from sources across the organizational IT infrastructure to identify potential threats and anomalies that signal unauthorized activity or security incidents.
SSPM cybersecurity incorporates features of other solutions, such as compliance and data security software, and builds on the strengths of existing solutions like CASBs—while keeping pace with the rapidly changing SaaS environments and addressing the unique challenges associated with each stakeholder’s responsibilities.
What happens without SSPM
Without SSPM, security teams often operate in the dark. They rely on manual audits, disconnected logs, and best guesses. Misconfigurations go undetected. Over-privileged accounts accumulate. Third-party connections proliferate unchecked. Compliance becomes a fire drill.
Most importantly, risk increases and attackers notice. Data breaches caused by SaaS misconfigurations are growing. And in many cases, the root causes are simple oversights that could have been caught with SSPM in place.
The future of SSPM
SSPM is still evolving. As SaaS usage matures, SSPM will expand to support machine and AI identities along with other developments in the space.
Securing SaaS is no longer optional—it’s mission-critical. And doing it well requires more than native controls and point-in-time checks.
SSPM provides a framework for visibility, control, and continuous improvement. It helps security teams do more than react. It gives them the insights and automation to manage SaaS risk at scale, supporting secure, productive use of the tools that drive modern business.
The AppOmni SaaS Security Checklist

Critical components of a comprehensive SaaS security solution.
Read more: SaaS Security Posture Checklist: 25 Questions to Assess Your SSPM Strategy