OAuth tokens and third-party integrations have become the backbone of productivity and connectivity as SaaS apps become the operating system of modern business. Yet behind this convenience, OAuth tokens often introduce hidden security risks that can compromise sensitive company data, expose critical systems, and increase the risk of data breaches. For IT leaders, security teams, and business decision-makers, understanding how OAuth works (and the unique vulnerabilities associated with third-party integrations) is essential for protecting your organization’s cloud environment and preventing unauthorized access.
In this article, we explore:
- The hidden security risks of OAuth tokens and third-party SaaS integrations.
- How attackers exploit forgotten or over-permissioned tokens to access sensitive data.
- Practical steps for IT and security teams to secure cloud apps and reduce organizational risk.
What are OAuth tokens?
At its core, OAuth (Open Authorization) is a widely adopted protocol that enables users to grant applications limited access to their accounts on another service without sharing their password.
Instead, OAuth uses access tokens, which are digital credentials issued after the user consents to an app’s requested permissions. These tokens act like a temporary, specific key for an application; while some are cryptographically signed, many are simply unique strings that represent the authorized permissions.
Think of an OAuth token as a valet key. While your password acts like your master key (proving your identity), an OAuth token is like a valet key you give to a third-party application. It grants specific, limited permissions, like reading your calendar but not deleting it, without you ever handing over your master key.
OAuth tokens can provide a third-party app with tightly scoped access to only certain data or actions. These tokens are exchanged behind the scenes in the “OAuth flow,” which often begins when a user clicks “Sign in with Google” or “Connect to Slack.”
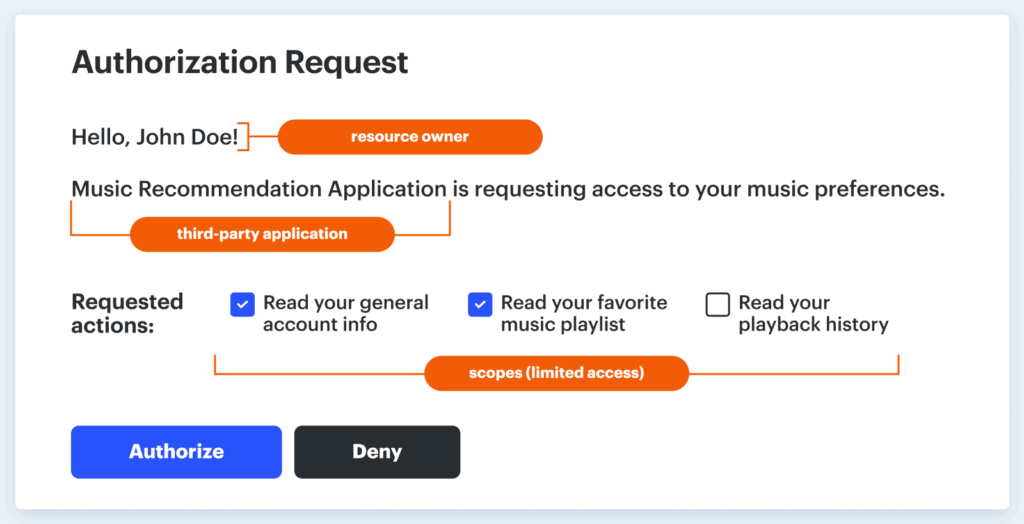
This architecture is what makes integrations and automation between SaaS platforms not only possible but efficient. Businesses can safely link productivity tools, automate workflows, and enable single sign-on (SSO) across a multitude of platforms. However, while OAuth tokens are designed to keep passwords private and minimize exposure, they are themselves powerful secrets that, if mismanaged, can become the weak link in an otherwise secure environment.
➡️ For a deep dive into specific OAuth token vulnerabilities, see this additional blog. For organizational best practices, continue reading below.
Why OAuth is everywhere in modern SaaS environments
The explosion of SaaS apps in the workplace has made OAuth a cornerstone of digital collaboration. Employees regularly authorize new integrations to enhance productivity: Marketing platforms sync with CRM tools, developers link repositories with project management boards, HR systems connect with communication platforms, and so on.
This proliferation is not just a convenience; it’s a competitive necessity. OAuth tokens make it possible for organizations to move fast, reduce IT friction, and empower teams to choose their own tools. As a result, most enterprises now manage hundreds or even thousands of active OAuth tokens across their environment at any given time. Each of these tokens represents an implicit trust relationship between your organization, a third-party service, and in many cases, other fourth- or fifth-party applications integrated by those vendors.
What are the benefits of OAuth?
- Enables secure delegated access: OAuth allows applications to access user data on another platform without exposing user passwords.
- Supports granular permissions: Users can grant apps only the specific level of access needed (using “scopes”), reducing unnecessary risk.
- Improves user experience: Simplifies sign-in and app integration by letting users authorize with a few clicks, avoiding multiple logins.
- Facilitates seamless third-party integrations: Makes it easy for organizations to connect SaaS tools and automate workflows across cloud platforms.
- Reduces password fatigue: Users no longer need to remember or manage separate passwords for every application.
- Supports modern security standards: OAuth works with multi-factor authentication and single sign-on, enhancing overall security posture.
- Minimizes credential exposure: Since passwords are never shared with third-party apps, the risk of password theft or leakage is significantly reduced.
As with many benefits come some challenges. The core challenge with OAuth is that every new connection increases the attack surface (the number of ways in which an attacker could try to access sensitive business data). Most organizations struggle to maintain visibility into all the tokens in use, let alone monitor or manage their associated risks.
Third-party integrations: Productivity’s double-edged sword
Third-party integrations are the other piece of this puzzle. They automate processes, facilitate data sharing, and allow best-of-breed tools to work together seamlessly. We all love them, we all need them, yet, with each new integration, organizations cede a bit of control over their security posture.
Many organizations have learned the hard way that it’s not just the apps they choose to trust, but also the developers, partners, and vendors behind those apps, who become stakeholders in their security. Even well-intentioned integrations can become vectors for data leakage, unauthorized access, or compliance violations.
Shadow IT (the unsanctioned adoption of software or services by employees) is often enabled by OAuth, since users can grant permissions to apps without ever going through IT. Over time, these “invisible” integrations accumulate, often with excessive permissions and no oversight.
Moreover, third-party developers may not hold themselves to the same security standards as your own IT department. A compromised or poorly secured third-party service can expose all OAuth tokens granted to it, providing attackers with direct access into your most sensitive business platforms.
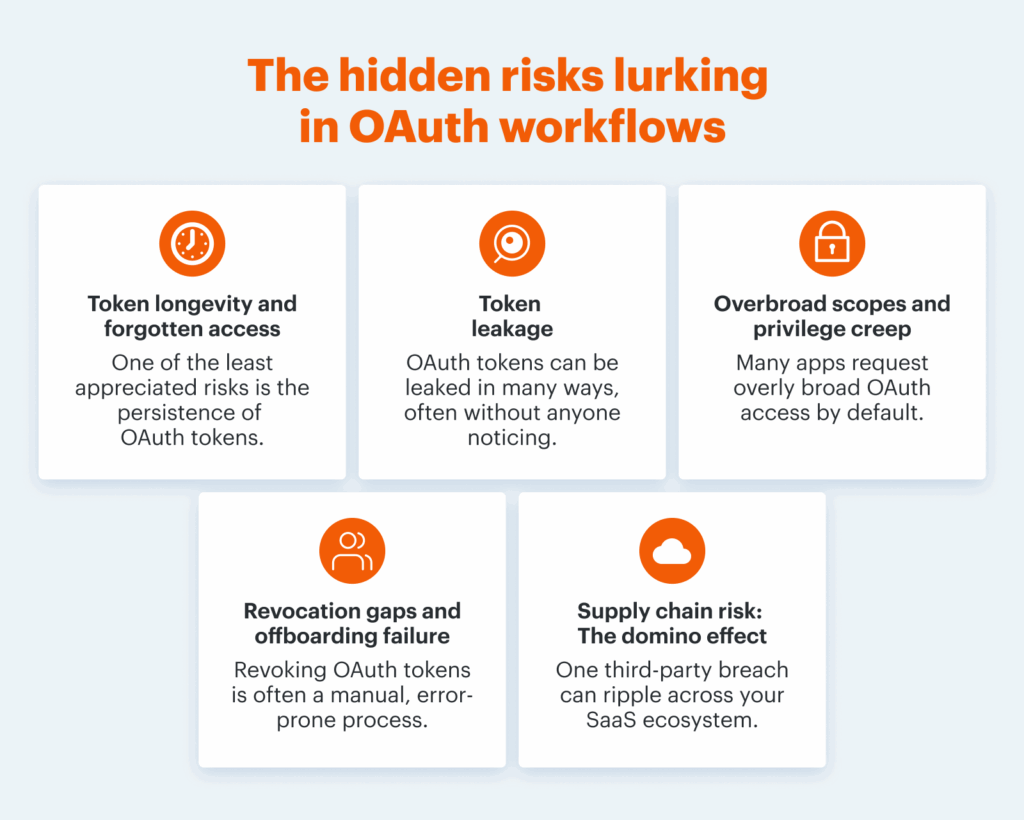
The hidden risks lurking in OAuth workflows
Token longevity and forgotten access
One of the least appreciated risks is the persistence of OAuth tokens. Unlike passwords, which users might change regularly, OAuth tokens can remain valid for months or even years. In some cases, unless explicitly revoked, they may never expire. Consider what happens when an employee leaves the company or when a project ends: unless someone manually reviews and revokes those tokens, the third-party app can retain access to your systems indefinitely.
Token leakage
OAuth tokens can be leaked in many ways, often without anyone noticing. Debug logs, browser caches, clipboard history, or even GitHub repositories can inadvertently expose valid tokens. Attackers actively search for these accidental disclosures, using automated tools to scan public code and logs for secrets like API keys and OAuth tokens.
Once discovered, these tokens can be used to access systems without triggering password resets or multi-factor authentication (MFA) alerts. This is because the token itself is proof that authentication has already occurred. The attacker isn’t logging in as the user; they are using a credential that represents a pre-authorized session, effectively bypassing the front door security controls
Overbroad scopes and privilege creep
While OAuth supports “scopes” (allowing apps to request only the permissions they need), many apps default to requesting the broadest possible access. This creates a situation where a seemingly harmless tool (like a calendar app) might be able to read, write, or delete emails, files, or contacts. Over time, permissions can expand unnoticed, especially as users accept prompts without understanding the implications.
Revocation gaps and offboarding failure
Revoking OAuth tokens is often a manual, error-prone process, largely because most organizations lack a centralized, automated inventory of all authorized integrations. This lack of visibility means that when employees depart or projects end, their associated tokens are frequently forgotten rather than revoked, creating a growing collection of “zombie” tokens (forgotten, still active authorizations that persist long after their intended use). Attackers seek out these dormant tokens, knowing they are less likely to be monitored or deactivated.
Supply chain risk: The domino effect
The interconnectedness of modern SaaS platforms means that a breach in one third-party provider can have ripple effects throughout the ecosystem. If a trusted vendor suffers a security incident, any OAuth tokens it stores (or those of its own integrations) could be compromised. This can lead to secondary breaches in entirely unrelated systems, amplifying the impact and complexity of the attack.
Examples of OAuth and third-party integration attacks
These threats aren’t just hypothetical. They’re real. Here are a few examples of what could happen:
- Silent email takeover: Consider a scenario where an attacker obtains an OAuth token with “read/write” access to a company’s email platform. Unlike traditional account compromises, there may be no login from an unusual location, no password reset, and no MFA challenge. The attacker can quietly monitor, redirect, or even manipulate communications (perhaps adding malicious rules or siphoning sensitive attachments), all while remaining invisible to both the user and IT.
- Mass data exfiltration: In another case, a marketing integration with broad API access is compromised. The OAuth token allows the attacker to download customer lists, financial data, and confidential documents at scale, often via official APIs. Since the activity uses valid tokens, it may bypass traditional security controls and go undetected until significant damage is done.
- Privilege escalation and shadow admins: A malicious OAuth token with administrative scopes can be weaponized to create new privileged accounts, change configuration settings, or grant access to additional integrations. Attackers have been known to use such footholds to escalate their privileges and maintain persistence within an environment.
Real-world examples
- UNC6040 Salesforce vishing campaign: This threat involved “vishing” (voice phishing) to persuade users into authorizing a malicious Salesforce connected app with OAuth, leading to mass CRM data exfiltration. Detection and prevention strategies detailed here.
- UNC6395 stolen OAuth tokens abused for SaaS-to-SaaS compromise:The UNC6395 group exploited stolen OAuth tokens to target and access sensitive data across Salesforce, Google Workspace, and other business-critical SaaS platforms. By hijacking legitimate third-party connections, attackers bypassed MFA and gained persistent access to organizations’ most valuable SaaS data. This incident underscores the urgent need for real-time SaaS-to-SaaS risk visibility, continuous monitoring of connected apps, and strict management of OAuth tokens and permissions. Read our full analysis and prevention recommendations here.
- Commvault supply‑chain breach: AppOmni’s AO Labs dissected the Commvault incident, where attackers leveraged OAuth tokens in a SaaS-to-SaaS supply-chain compromise. The analysis highlights how compromised tokens granted MFA-bypassing access across environments and emphasizes the need for continuous visibility and token management.
- GitHub OAuth consent phishing: Developer accounts compromised via OAuth consent trick; full repo access obtained. This shows how attacker-controlled OAuth apps can be used to escalate privileges and gain lateral movement inside SaaS environments.
How to secure OAuth tokens and manage third-party risk
Build visibility and inventory
Security begins with visibility. Organizations need to maintain a living inventory of all OAuth tokens issued in their environment, including details on which apps they connect to, what scopes they have, and which users or systems authorized them. Many SaaS platforms provide dashboards or APIs for this purpose, but dedicated SaaS security tools can offer centralized monitoring and alerting.
Enforce the principle of least privilege
Regularly review and audit OAuth permissions. Ensure that integrations are granted only the minimum necessary access, and challenge requests for broad or administrative scopes. When possible, use “just-in-time” permissions that expire automatically, reducing the risk of lingering access.
➡️ Learn about AppOmni’s Token Manager to help strengthen your least privilege token management
Automate revocation and off-boarding
Integrate token revocation into your employee offboarding process and review third-party access regularly. Automated tools can help identify unused or risky tokens and ensure they are deactivated quickly, closing gaps before they can be exploited.
Educate and empower users
Many breaches begin with a user unknowingly granting risky access to a malicious or compromised app. Train employees to scrutinize permission requests and recognize the risks of unsanctioned integrations. Establish policies and controls that define which apps are approved and how new integrations are vetted.
Monitor for anomalies
Set up alerts for unusual OAuth activity, such as tokens being used from unexpected locations, at odd hours, or in ways inconsistent with their intended use. Modern security platforms can detect behavioral anomalies and flag high-risk tokens for immediate review.
Conclusion
OAuth tokens and third-party integrations are not just technical conveniences; they are business enablers. But with great power comes great responsibility. The hidden risks associated with OAuth demand a proactive, layered security strategy. By understanding how tokens work, where their vulnerabilities lie, and how attackers seek to exploit them, organizations can unlock the benefits of SaaS collaboration without leaving the door open to invisible threats.
Ready to keep learning? Request a complimentary risk assessment to learn more about how your SaaS supply chain stacks up or download the OAuth Security Checklist.
OAuth Security Checklist
Reduce SaaS risk. Control third-party access. Stop token-based attacks.
Read more: OAuth Security Checklist