Pentest Definition
A penetration test (pentest) is an authorized, simulated cyberattack performed by security professionals to find and exploit real-world vulnerabilities in systems, applications, networks, or APIs so those weaknesses can be fixed before attackers find them.
Penetration Testing FAQs
What is Penetration Testing (Pentest)?
A penetration test (pentest) is an authorized, simulated cyberattack designed to evaluate a system’s security configuration. It’s conducted within a specific scope and timeframe, with clear rules about what can and cannot be tested.Security professionals use both automated scanning tools and hands-on testing methods to search for security weaknesses. They look for common vulnerabilities like weak authentication, injection flaws (where malicious code can be inserted), misconfigurations, insecure APIs, and broken access controls. Once they find these issues, they try to exploit them, and typically produce a pentest report to show how serious the risk actually is.
Why Do Companies Do Penetration Testing?
Companies perform penetration testing to proactively find and fix cybersecurity weaknesses before attackers can exploit them. Unlike automated vulnerability scans, a pentest goes deeper – it shows whether vulnerabilities can actually be chained or exploited in real-world attack scenarios.
The main goals of a pentest are to:
- Identify exploitable vulnerabilities: across SaaS applications, APIs, infrastructure, and cloud environments.
- Validate security controls: confirming that firewalls, authentication systems, and monitoring tools respond properly to attempted attacks.
- Meet compliance and regulatory requirements: such as SOC 2, ISO 27001, HIPAA, and PCI DSS, which often mandate periodic testing.
- Reduce business risk: by prioritizing critical findings and remediating vulnerabilities before they lead to data loss or service disruption.
In the context of SaaS application security, penetration testing helps organizations ensure that their cloud applications and integrations are properly secured, especially since SaaS platforms often manage sensitive customer data and rely on complex API connections. Testing these environments uncovers real misconfigurations, privilege escalation paths, and data exposure risks that automated tools or internal reviews might miss.
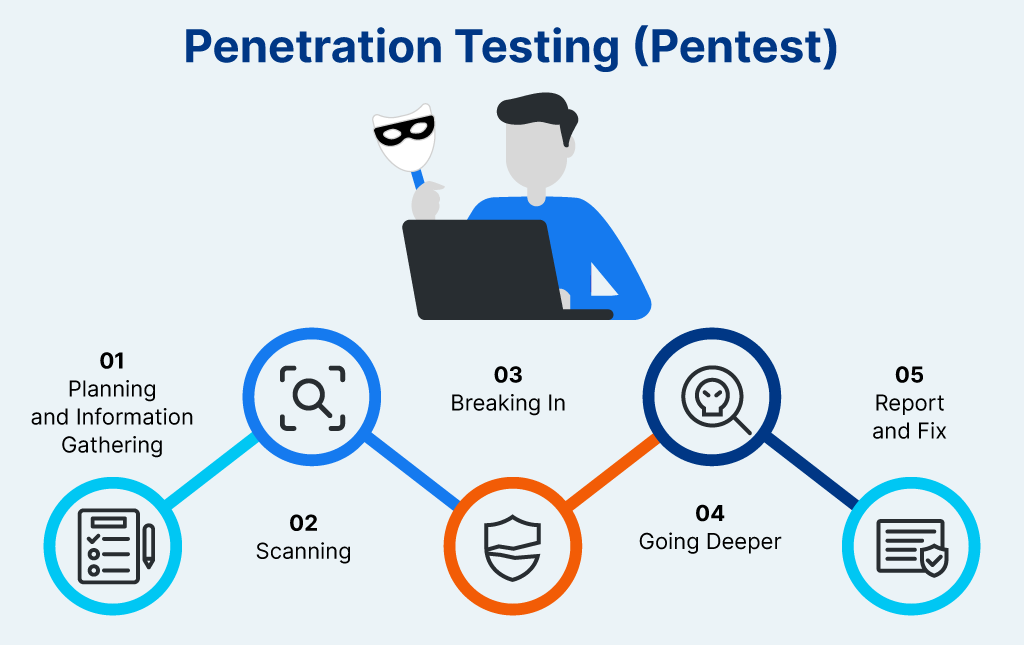
What are the Pentest Phases?
A pentest methodology outlines the structured steps to plan, execute, and report a penetration test. While details vary by framework (such as NIST SP 800-115 or OSSTMM), most pentests follow five key phases:
- Planning and Information Gathering: The team decides what will be tested, sets the rules, and gathers basic information about the target systems using public sources and network scans.
- Scanning: Automated tools are used to find live systems, open ports, and potential weak spots in websites, apps, and APIs.
- Breaking In: Testers try to exploit the vulnerabilities they found – like attempting SQL injection or finding ways to gain unauthorized access – to see what a real attacker could do.
- Going Deeper: Once inside, testers see how far they can go: Can they access more systems? Get higher-level permissions? Reach sensitive data? This shows the full potential damage of an attack.
- Report and Fix: All findings are compiled into a report that explains what was found, how it was exploited, what the risks are, and how to fix each issue. This guides the organization on what to patch and improve.
Types of Pentests
Penetration tests (pentests) come in various types, depending on the systems being tested and the amount of information shared with the tester. These variations help organizations evaluate different layers of their security posture, from networks to cloud and SaaS applications.
- Black Box Test: The tester receives no information about the system. They act like an external hacker with no inside knowledge, using only what they can find publicly or discover themselves. This tests how well your perimeter defenses work against outside attackers.
- White Box Test: The tester gets full access to source code, system architecture, and detailed information. This approach is useful for finding deep security flaws in applications, including logic errors and access control issues that might not be visible from the outside.
- Gray Box Test: The tester has limited information, like basic user credentials or partial system details. This simulates an attacker who has gained some initial access or mimics an insider threat. It helps identify how someone could abuse their existing access to reach sensitive data or systems.
- External Test: This focuses on internet-facing systems like websites, APIs, and login pages. It tests what an outside attacker could exploit through your public-facing infrastructure.
- Internal Test: This assumes the attacker already has network access, simulating a compromised employee account or insider threat. It tests how far someone could move within your systems once they’re already inside.
- Red Team Test: Red team exercises simulate sophisticated attackers using real hacker techniques and tools to test both your technology and your security team’s ability to detect and respond to threats. Unlike standard tests that find many vulnerabilities, red teams focus on achieving specific goals (like accessing sensitive data) while staying undetected.
In modern SaaS application security, organizations often combine multiple pentest types. For example, external black box testing for exposure, followed by gray box SaaS tenant testing for privilege escalation. This hybrid approach helps verify both configuration security and real-world exploitability across cloud environments.
Vulnerability Assessment and Penetration Testing
A vulnerability assessment identifies potential weaknesses in your system, while a penetration test actually tries to exploit them. Think of it this way: a vulnerability assessment tells you where the unlocked doors are, but a pentest checks if someone can actually walk through them and what they could steal once inside.
What is Attestation After a Pentest?
An attestation letter (also called an Executive Summary Report or Pentest Report) is a formal document from an independent third party that confirms a penetration test was performed and summarizes the results.
An attestation letter includes confirmation that the organization’s security was evaluated against industry standards, the scope of testing, a high-level overview of findings (without detailed vulnerabilities), and the methodology used.
Organizations use these letters to meet compliance requirements, build trust with clients and stakeholders, and demonstrate their security commitment. Think of it as a “certificate” that proves your system was tested and summarizes its security posture – suitable for sharing with executives or compliance officers who need verification without exposing the technical details found in the full report.
Enhancing Penetration Testing for SaaS Environments with AppOmni
Traditional penetration tests are essential for identifying exploitable vulnerabilities, but they often miss critical SaaS-specific risks, such as misconfigured permissions, broken tenant isolation, excessive admin roles, and insecure API integrations.
AppOmni complements pentests by continuously monitoring SaaS environments, assessing configurations, and identifying hidden risks that may not appear during point-in-time tests.
By combining pentest results with AppOmni’s SaaS-aware insights, organizations gain a fuller understanding of potential attack surfaces, prioritize remediation, and strengthen their overall SaaS security posture. This helps to ensure that cloud applications like Salesforce, Microsoft 365, and Google Workspace remain protected against both external attacks and insider threats.