UEBA Definition
User and Entity Behavior Analytics (UEBA) is a cybersecurity process that uses machine learning and advanced analytics to monitor and analyze the behaviors of users and entities (like devices or applications) within a network. It identifies abnormal patterns that may indicate insider threats, compromised accounts, or malicious activity by comparing current behavior against established baselines.
UEBA FAQs
What is User Entity Behavior Analytics (UEBA)?
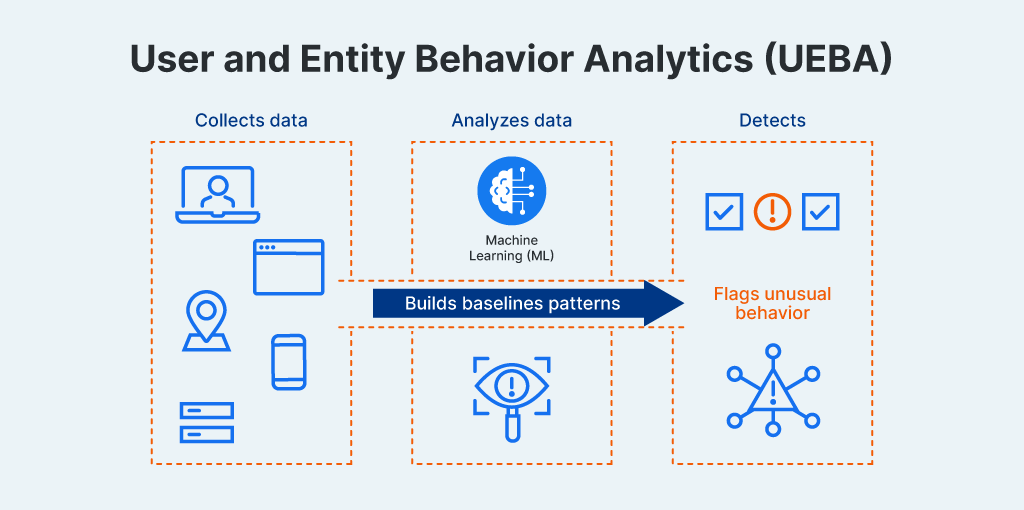
User and Entity Behavior Analytics (UEBA) is a cybersecurity approach that focuses on spotting the weird stuff, like the subtle anomalies that don’t fit normal patterns in how users, devices, and applications typically behave. Instead of just blocking known bad IP addresses or applying static rules, UEBA uses machine learning, statistical modeling, and data analytics to figure out what “normal” behavior looks like. Over time, it builds behavioral profiles and then flags activity that doesn’t line up.
Think of it like a smart security guard who doesn’t just check badges but notices when something feels off: maybe an employee who usually logs in from their office computer at 9 AM suddenly signs in from another country at 3 AM, or a printer service account starts downloading gigabytes of confidential data. On the surface, both logins look “valid,” but the behavior is suspicious. That’s where UEBA comes in, catching insider threats, stolen credentials, and sophisticated attacks that slip past traditional cybersecurity tools.
Why is UEBA Important in Modern Cybersecurity?
Today’s cyberattacks are much trickier than the obvious viruses we used to see. Hackers don’t just try to break down the door anymore; they’re more like burglars who steal your house key and walk right in. Take groups like ShinyHunters/UNC6040 and UNC6395, for instance. UNC6040 used phone scams to trick employees into connecting malicious apps to Salesforce, while UNC6395 stole authentication tokens from business applications to gain access without anyone noticing. These attacks show how cybercriminals now focus on stealing someone’s login credentials, hacking into trusted accounts, or even working with people who already have access to your systems.
Traditional cybersecurity tools like firewalls are great at stopping known bad actors, but they often miss these sneakier approaches. This is where UEBA tools help. They work by watching how people and systems normally behave, then alert you when something seems off. For instance, if a hacker steals login credentials and starts poking around systems they shouldn’t be in, or if an employee suddenly starts accessing files they’ve never looked at before, UEBA will notice and sound the alarm.
What makes UEBA security special is that it doesn’t rely on a fixed list of “bad things to watch for.” Instead, it learns and adapts as it goes, improving its ability to spot unusual behavior over time using AI and machine learning. UEBA helps security teams catch the kind of advanced, hidden attacks that would normally slip by unnoticed.
What Role Does Machine Learning or AI Play in UEBA?
Machine learning (ML) and artificial intelligence (AI) are the engines that make UEBA work. Instead of security teams manually writing rules for every possible threat (which is impossible at today’s scale), UEBA uses ML algorithms to automatically learn what normal behavior looks like across users, devices, and applications. Over time, the system builds baseline patterns like when employees usually log in, how much data they typically move, or which applications they access, and then flags deviations without needing someone to tell it exactly what to look for.
The AI side comes into play when UEBA must make sense of vast amounts of noisy data. It can spot subtle anomalies that humans would miss, reduce false alarms by filtering out harmless oddities, and even prioritize risks so that analysts know what to look at first. In other words, modern UEBA security solutions use ML and AI to adapt as behavior changes, catch brand-new attack techniques, and free up security teams from constantly chasing static rule updates.
How is UEBA Different from Traditional Security Tools, such as SIEM or IDS?
Traditional security tools, such as SIEM (Security Information and Event Management) and IDS (Intrusion Detection Systems), are effective at collecting logs and identifying known threats. However, they primarily focus on detecting attacks that security experts have already encountered.
UEBA works differently. Instead of following a rulebook, it learns what “normal” looks like, then flags unusual behavior. A SIEM might alert you that someone entered the wrong password, but UEBA goes deeper – noticing if that same person suddenly logged in from another country and started downloading sensitive files. This is especially valuable for SaaS Security, where employees access cloud apps like Salesforce or Microsoft 365 from anywhere, and traditional tools often can’t monitor these environments effectively.
The best approach combines both. SIEMs handle log management and compliance, while UEBA adds behavioral intelligence across your on-premises and cloud systems, helping catch insider threats and sneaky attacks that traditional tools would miss.
How Does UEBA Collect and Analyze Behavioral Data?
UEBA platforms gather information by connecting to your existing security tools (SIEMs, identity management systems, endpoint protection, firewalls, and cloud applications). They collect data from various sources, including login records, file access logs, network activity, app usage, and system events, across your infrastructure to create a centralized UEBA analytics hub.
The real work happens during continuous monitoring. UEBA constantly compares live activity against established baselines to identify any unusual activity. When it finds anomalies, it assigns risk scores based on context. For example, multiple suspicious activities happening together, accessing sensitive data, or patterns that match known attack methods. High-risk anomalies get flagged as alerts or automatically sent to your SIEM or security response tools for investigation.
What are Some Common Use Cases for UEBA?
UEBA is used to detect subtle, high-risk behaviors that traditional security tools often miss. Common use cases include:
- Insider threats: Identifying employees or contractors accessing sensitive data outside of their normal scope, or performing actions inconsistent with their typical patterns.
- Compromised accounts: Detecting unusual login activity such as logins from unfamiliar locations or devices, multiple failed login attempts, or atypical access to high-value systems, which may indicate stolen credentials.
- Lateral movement: Spotting attackers who have gained access to a system and are moving across the network, accessing resources or systems they normally wouldn’t touch. UEBA tracks these deviations from established behavioral baselines to catch early signs of breach progression.
- Data exfiltration: Monitoring abnormal file transfers or downloads, such as a service account suddenly copying large volumes of sensitive information, which could indicate a breach or insider malfeasance.
- Privilege abuse: Flagging accounts that suddenly perform administrative or privileged actions outside their normal role, helping prevent misuse or policy violations.
- Anomalous application or device behavior: Detecting unusual patterns in device activity, IoT systems, or SaaS apps (like unexpected API usage), which could indicate compromise or misconfiguration.
How Does UEBA Adapt to Monitoring User Behavior Across SaaS Applications?
User and Entity Behavior Analytics (UEBA) enhances SaaS threat detection by integrating behavioral insights with identity and permission data across cloud applications like Salesforce, Google Workspace, and Microsoft 365. This approach enables security teams to identify high-risk behaviors such as privilege escalation, unauthorized access, and brute-force logins by analyzing user activity in the context of their roles and entitlements
UEBA platforms collect and analyze data from various sources, including authentication logs, file access records, and network traffic. By establishing baselines of normal behavior, UEBA can detect deviations that may indicate compromised accounts or insider threats. For instance, if a user accesses sensitive data from an unusual location or at an atypical time, UEBA can flag this as suspicious activity.
How Does AppOmni Leverage UEBA in SaaS Security?
AppOmni enhances User and Entity Behavior Analytics (UEBA) by integrating deep SaaS visibility with identity-aware threat detection, enabling organizations to proactively identify and mitigate risks within their SaaS environments. Our SaaS security platform continuously monitors user activity, configurations, and permissions across critical applications like Microsoft 365, Salesforce, and Google Workspace, detecting anomalies such as privilege escalations, unauthorized access, and suspicious administrative actions.
AppOmni integrates with existing security tools like SIEM, SOAR, and UEBA systems, making it easy for security teams to monitor SaaS activity alongside their other security operations. This integration means you don’t have to manage SaaS security in isolation.
The result is that organizations can detect and respond to threats as they happen, reducing the chances of data breaches and strengthening their overall SaaS security.