Third-Party Risks for SaaS
Real-time visibility and insights into risks introduced by connected applications.
CHALLENGE
SaaS applications are all connected and intertwined. These extensions and integrations often request excessive permissions and operate outside of IT’s visibility. Without clear oversight, organizations risk data exposure, privilege abuse, and supply chain compromise.
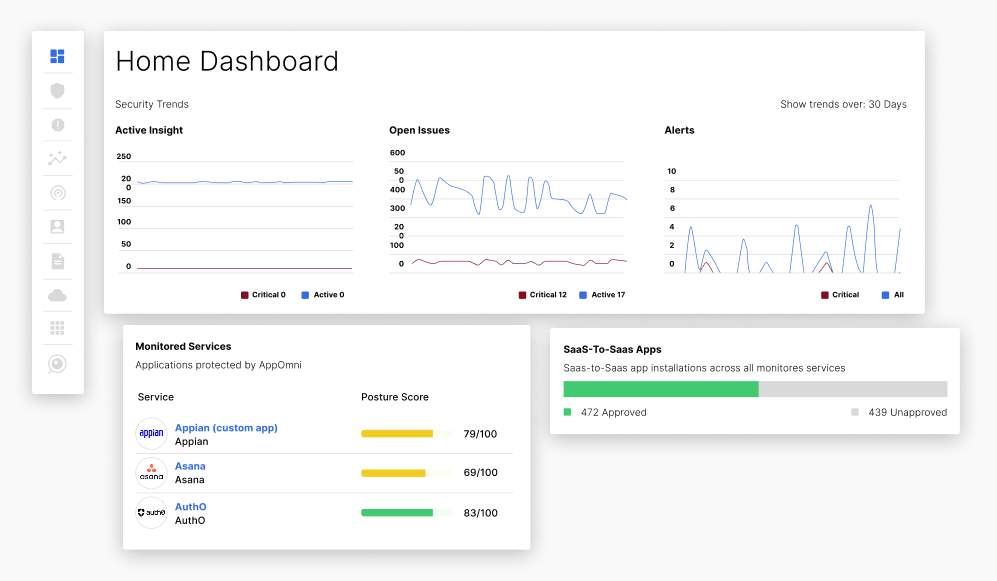
How AppOmni secures third and fourth party app risks
AppOmni provides the telemetry and tools, combined with posture and identity centric analysis to efficiently prioritize and respond to SaaS security threats.
Identifies Unsanctioned Apps
Proactively alert and prioritize unsanctioned non-human identities.
Increased Visibility
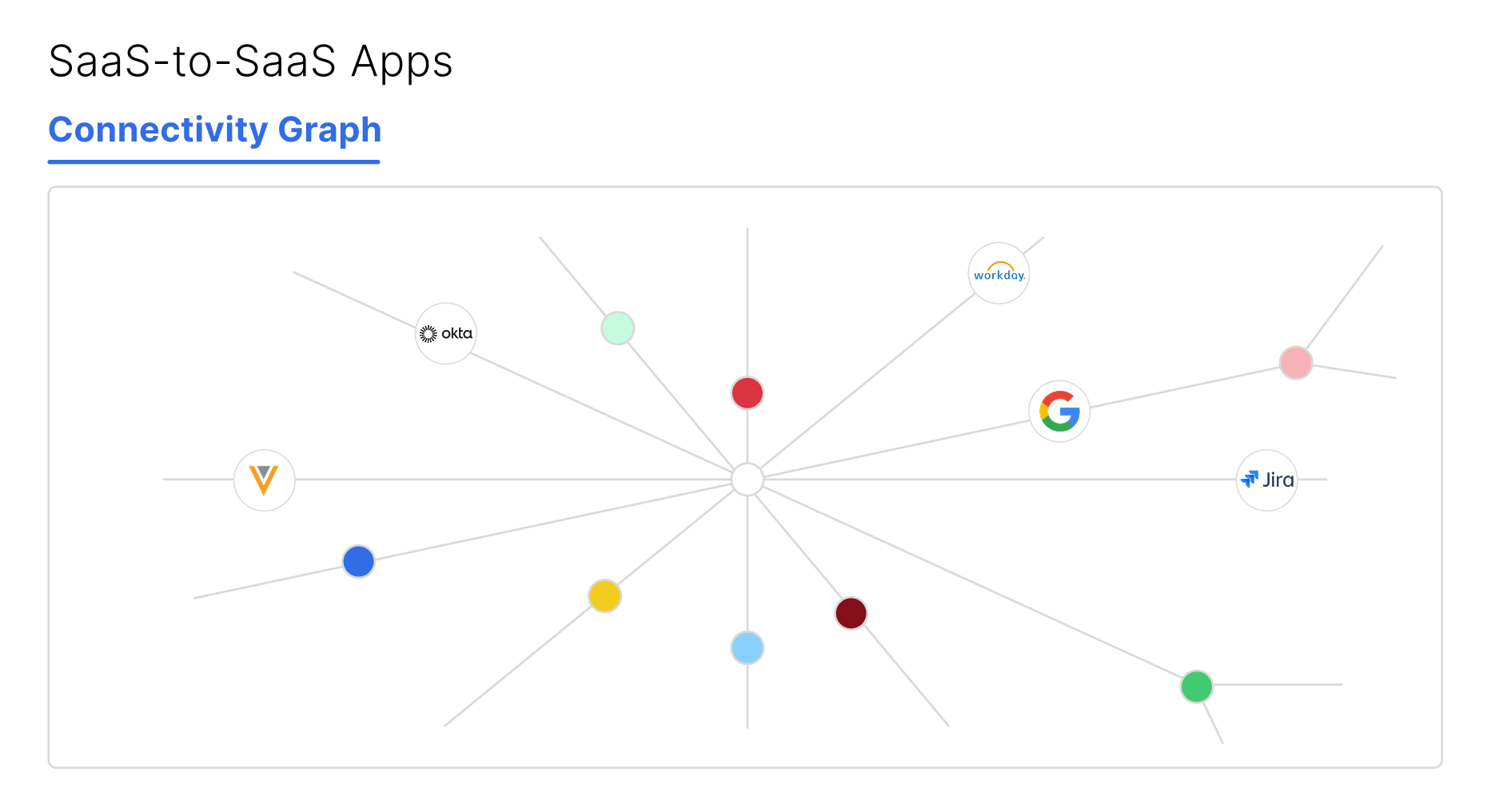
Visualize and monitor SaaS to SaaS integrations, including those authorized by non-human identities.
Discovers Exposure and Impacts
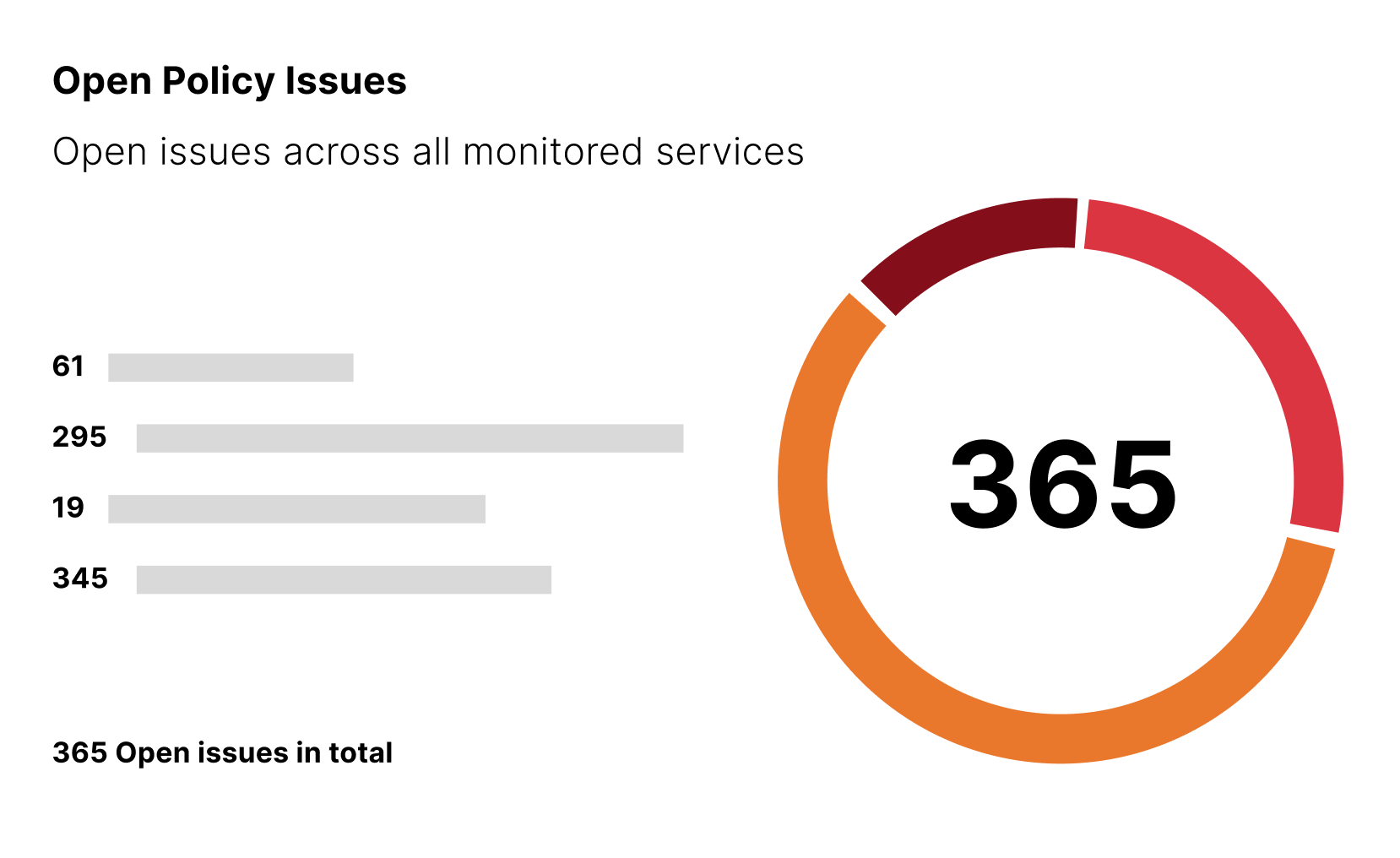
Quickly identify the blast radius of connected apps and misconfigurations.
Key Features
A modern defense strategy for the SaaS supply chain
To defend against recent breaches like UNC6395 and UNC6040, enterprises need a security strategy built for the SaaS-to-SaaS layer.
| Recent Breach TTPs | Capabilities Needed to Prevent | AppOmni |
|---|---|---|
| Initial Access Attackers use social engineering, compromise trusted third-party apps, and abuse OAuth tokens to gain initial access and bypass MFA. | Identify SaaS shadow SaaS and shadow AI Discover third-party connections | ✅ |
| Privilege Escalation & Lateral Movement They exploit SSO misconfigurations and overly permissive accounts to gain administrative rights and pivot to other connected apps. | Prevent Misconfigs by continuously monitoring permissions and configs of apps and users Data exposure, ensure secrets are stored correctly Unauthorized connections via VPN, TOR, or IPs | ✅ |
| Exfiltration Attackers user anomalous behavior such as VPNs, TORs, or IPs from various locations to exfil sensitive data. | Detect Anomalous behavior with User Entity Behavior Analytics (UEBA) such as: High volume API requests Anomalous user logins OAuth activity from VPNs/TORs Normalization of SaaS logs | ✅ |
| Response Stepped up authentication through Shared Signals with IdPs Search normalized logs SIEM/SOAR/ITSM integrations | ✅ |
Remove Risky SaaS Integrations
See how AppOmni discovers third-party connections across your SaaS estate, maps data access and blast radius, and guides you to unwind what you do not trust.
“I needed to get a better understanding of the overall attack surface, our portfolio of applications, and their configurations and data exposure risks.”
Wai Sheng Cheng
Information Security and Risk Manager, Spencer Fane

How New Supply Chain Attacks Challenge SaaS Security: Lessons from UNC6395 and UNC6040 (ShinyHunters)
Attackers like UNC6395 and UNC6040 expose SaaS supply chain risks. Learn how stolen OAuth tokens bypass security—and how to protect your data.
Related Content
-
Identity Crisis: Why SaaS Attacks Are Bypassing Your Best Defenses
To help build a solid foundation for AI adoption, IM firms should source high-quality data, use modern data cloud/hybrid infrastructure, and adopt robust data governance principles.
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-
Artificial Intelligence security vulnerability uncovered
Aaron Costello with AppOmni tells Good Morning Cleveland anchor Mike Brookbank more about the flaw in the ServiceNow platform.
Critical applications secured
Protect data essential to your business