Previous security breaches at Heroku and GitHub serve as stark reminders that OAuth token theft and inactive, overly permissive SaaS-to-SaaS connections represent significant security risks to any organization.
As more employees turn to SaaS apps to streamline job processes and boost productivity, they rely on OAuth to authenticate and authorize these apps with their enterprise SaaS platforms. This comes as no surprise, as OAuth’s user-friendly framework allows users to access SaaS apps, which also contain data and workflows.
But this OAuth connection and associated OAuth token can also allow unguarded access to SaaS apps for extended periods of time. This is why stealing or compromising OAuth tokens is so sought after by threat actors. While OAuth is a secure framework, the improper implementation and the lack of continuous monitoring of SaaS app access, may leave your organization exposed to unnecessary security risks, which can result in incidents.
What is OAuth and what cyber risk does it pose?
OAuth 2.0 is an open standard authorization protocol or framework that allows users to grant SaaS apps and other websites limited access to their secure resources without having to share their user credentials.
Let’s say an employee uses Asana to optimize project management tasks. With OAuth, they can authorize Asana to access their Microsoft 365 account (and the data connected to it) without ever having to disclose their Microsoft 365 account credentials to Asana. Although OAuth protects a user’s credentials to some extent, it still grants holders of those tokens, including threat actors who manage to compromise a SaaS service provider, to gain access to the connected app — Microsoft 365 in this case.
Instead of users having to relay a password to the SaaS app, OAuth provides it with access tokens that indicate it’s able to read specific data from the enterprise SaaS platform. So, just how does this authentication process work?
How does OAuth 2.0 work?
There are three major components to an OAuth transaction: the resource owner, the SaaS application, and the office productivity suite. In this scenario, Bob is the resource owner, the SaaS app is Asana, and the office productivity suite is Microsoft 365. Here’s an overview of the usual OAuth authentication process:
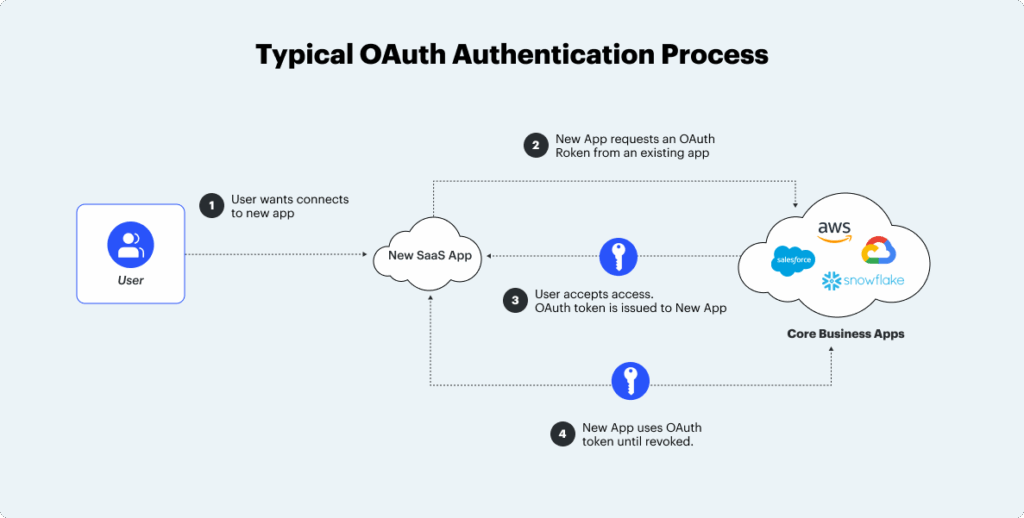
1. The user expresses intent
- After months of toggling between various emails, spreadsheets, and project management tools, Bob decides to use Asana to facilitate his job functions. Bob visits Asana and requests to login with his office productivity suite, Microsoft 365 (which may also store sensitive company data.)
2. The SaaS app asks user for permission
- Asana will redirect Bob to Microsoft 365, requesting for him to enter his user credentials. After Bob logins a prompt will appear asking to grant “read-write” access for Asana to read data in his Microsoft 365 account. Bear in mind that there’s no hierarchy of access rights you can permit a SaaS app to have.
- After Bob logs into Microsoft 365, a secret token will be generated allowing the SaaS platform to authenticate that the token is from Asana. Imagine a secret token as an electronic key required for a SaaS app to enter and establish a connection with your enterprise SaaS platform.
3. The user is redirected to the SaaS app
- Now that Bob has the secret token, Google redirects him back to Asana. He can then use the token to verify his identity and enter the SaaS app.
4. The SaaS app gets a session token and assesses the service provider
- Asana will then exchange its secret token for a session token and can access relevant data to do its functions until the session token is revoked. Now, Asana and Microsoft 365 can maintain an API based cloud-to-cloud communication without Bob having to continually login.
After the initial strong OAuth authentication, SaaS apps can continue to sync and access your data without requiring the same level of authentication. This may create potential blindspots that threat actors can leverage to exploit your enterprise SaaS platform.
3 common ways threat actors hijack OAuth tokens
While OAuth is relatively secure, the implementation of OAuth may expose your organization to threats. Here are some of the most common vulnerabilities that may arise during this process:
1. Open Redirects
Remember the redirects mentioned above that transfer users back to the SaaS app after the secret token is granted? These redirects can be easily exploited by threat actors to create external fake websites that mimic a users’ enterprise SaaS platform. Unsuspecting users may enter their credentials on these fake sites, allowing attackers to steal session tokens and gain access to their SaaS estate, potentially compromising valuable data.
2. Consent Phishing Attacks
Phishing is a widely used attack mechanism and for OAuth token theft the steps are no different. Threat actors will create malicious apps urging victims to say “Yes” to the OAuth permissions consent link, allowing attackers to read and write emails, read contacts, and access other proprietary data. Microsoft reports a surge in this phishing campaign, alerting users about attackers sending bogus apps to users to gain entry into their Microsoft Partner Network (MPN) accounts.
3. Cross-site Scripting (XSS) Exploitation
XSS allows attackers to inject malicious scripts into the code of an otherwise trusted webpage. Usually, these sites feature functionalities like comment boxes or search bars that interact with user input and are vulnerable to compromise. Attackers deceive these browsers into launching malware whenever a user visits the site. If someone enters their credentials, attackers can capitalize on this login to steal access tokens that are gateways into your SaaS ecosystem.
Use SaaS security posture management to mitigate OAuth token theft
OAuth access tokens can unlock valuable company data within your SaaS estate. Organizations need specific SaaS app security tooling that can detect and respond to OAuth token grants that suggest unusual suspicious activity.
If a user connects a SaaS app via an OAuth authentication and the app is granted administrative level privilege that wasn’t approved, there’s a sure-fire chance that something fishy is happening.
A SaaS Security Posture Management (SSPM) solution, like AppOmni continuously monitors your SaaS estate, alerting security and risk admins to take action on potentially compromised tokens.
Addressing these cyber risks are the exact reason why AppOmni was founded. We provide continuous monitoring and threat detection capabilities to prevent security risks from escalating into security incidents.
Identify and address your SaaS attack surface risk — schedule a 1:1 demo today.
Related Resources
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-

Start Smart, Scale Fast: AppOmni’s SaaS Security Packages Explained
AppOmni SaaS security maturity packages simplify risk reduction and compliance for all stages.
-

Securing AI in SaaS: No New Playbook Required
Say yes to AI, no to risks. AppOmni’s AI security solution overview breaks it down with smart discovery workflows and real-time threat detection.