On November 28 2023, Arctic Wolf Labs reported on a new Cactus ransomware campaign which exploits publicly-exposed installations of Qlik Sense, a cloud analytics and business intelligence platform. While the focus of the attack was on customer-hosted Qlik applications, those instances also integrate with many other SaaS systems as data sources and, if breached, attackers can move laterally from SaaS-to-SaaS.
The security vulnerabilities can be exploited by a remote, unauthenticated threat actor to do the following:
- Execute arbitrary code
- Set up an RDP tunnel for lateral movement
- Add new admins and change admin account passwords in Qlik Sense
- Exfiltrate data
- Deploy Cactus ransomware
Implications of the Qlik breach
With a breach like Qlik, the first question that comes to mind is: “Are we exposed? What is the impact?”
Most security and IT teams can confirm the use of specific apps across an organization. But what they often lack is having “eyes on” or visibility into other systems and apps that Qlik may be connected to, due to four top reasons:
- Applications’ usage and security configuration settings are not rigorously tracked after approval.
- End-users may bypass security to install additional apps (shadow IT), often enabling full Read/Write access and integration with business-critical apps such as Hubspot, Salesforce, and M365.
- Inheritance of refresh tokens or long-lived access tokens.
- Privilege elevation and permission sprawl. Different identities such as employees or contractors can accumulate greater access than they need in order to do their job.
Security teams often have to resort to traditional methods to determine who’s doing what, where. For example, they may send blast communications asking colleagues if they use an app, in hopes of fast replies. Not exactly ideal, scalable, or sustainable. This could also turn into a blame-first cybersecurity culture. Organizations should not expect employees and users to be the frontline defense against rampant phishing, coercive tactics, or credential-based attacks.
How can you detect SaaS data exposure and unsanctioned SaaS-to-SaaS connections?
SaaS Security Posture Management Tools (SSPM) tools provide the visibility and automation to investigate and prevent SaaS-to-SaaS (often referred to as third- and fourth-party) risk. Such a solution enhances any cybersecurity team’s ability to gain insights and protect every enterprise SaaS application and ensure operational continuity.
SSPM tools enable security teams to identify sanctioned or unsanctioned SaaS-to-SaaS connections, allowing CISOs to detect and identify the impact of a SaaS breach. Rather than having little visibility to how attackers managed to compromise your SaaS systems, an SSPM solution can remove the guesswork by answering questions like:
- What applications are connected?
- What level of access do individuals have in the platform?
- What are the configuration settings that may expose sensitive company information?
By incorporating an SSPM solution, you can take the first step to building a robust SaaS security program and understand how SaaS security threats may impact your business. From alerts for possible misconfigurations, SaaS-to-SaaS connections, or determining levels of access, SSPM can help you secure the applications to run your business.
SSPM in Action — How AppOmni Secured Our Environment From Qlik’s Potential Impact
Our own cybersecurity and IT teams leveraged the AppOmni platform to get a cursory glance and deeper look at Qlik’s potential impact to our business. In mere seconds, we were able to determine the scope of the potential threat and which SaaS apps Qlik connected to.
The security team identified Qlik connections to Salesforce and Google Workspace. With an additional pivot, the AppOmni platform also identified the application owners of the applications. This enabled the team to promptly notify the app owners to disconnect from Qlik, limiting any exposure or impact from the attack. No sensitive data, identities, or crucial workflows were exposed from the ransomware attack.
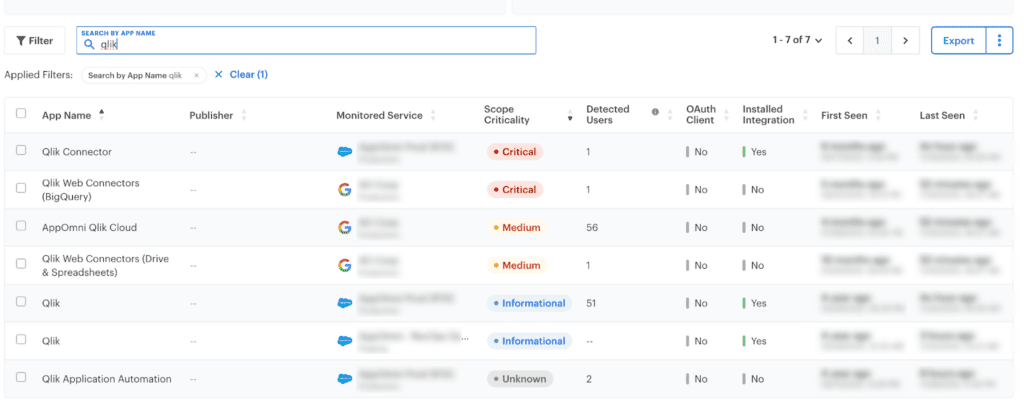
We can do the same to help your cybersecurity team achieve visibility and control over your SaaS estate. Do not hesitate to contact us.
If you’re a current AppOmni customer, check out AOInsight on the topic.

What Is SSPM?
SaaS applications need a virtual command room where security teams can manage their complex SaaS estate securely and holistically. Learn what makes a robust SaaS Security Posture Management (SSPM) solution and its key capabilities.
Related Resources
-

AppOmni at RSAC 2026: Details to Know Before You Go
AppOmni shares RSA Conference 2026 insights to improve SaaS and AI security.
-

Start Smart, Scale Fast: AppOmni’s SaaS Security Packages Explained
AppOmni SaaS security maturity packages simplify risk reduction and compliance for all stages.
-

Securing AI in SaaS: No New Playbook Required
Say yes to AI, no to risks. AppOmni’s AI security solution overview breaks it down with smart discovery workflows and real-time threat detection.