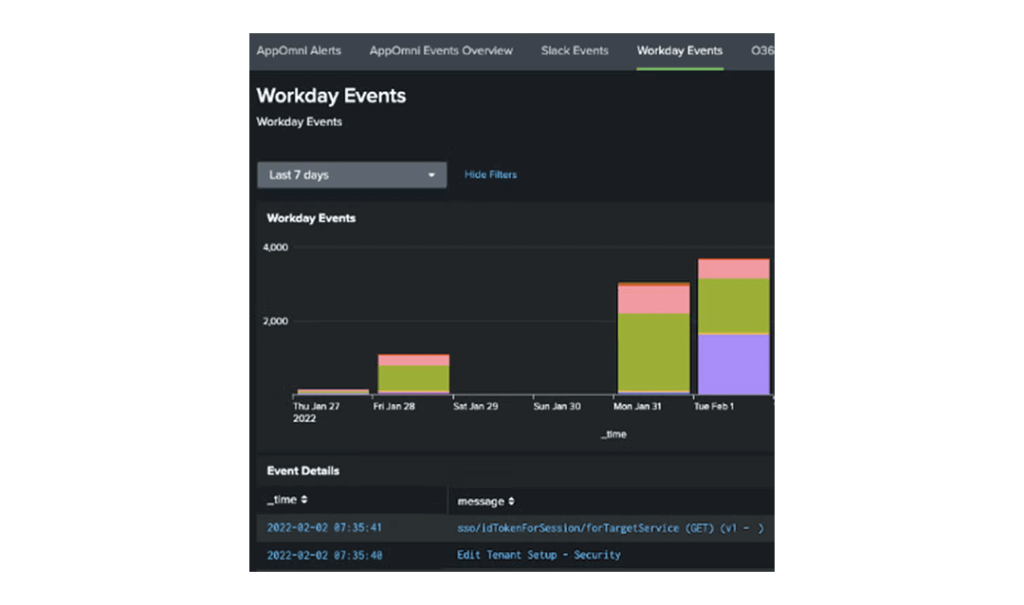
Threat Detection for SaaS Environments
Cut through the noise. See the full picture of your SaaS security threats.
CHALLENGE
Threat detection for SaaS isn’t just about spotting anomalies. It requires deep context across identities, permissions, and activity to detect real risks like privilege escalation, unauthorized access, and brute force logins.
AppOmni delivers precise, actionable threat detection by analyzing identity, permissions, and activity together—giving security teams the insights to spot high-risk behavior and respond faster.
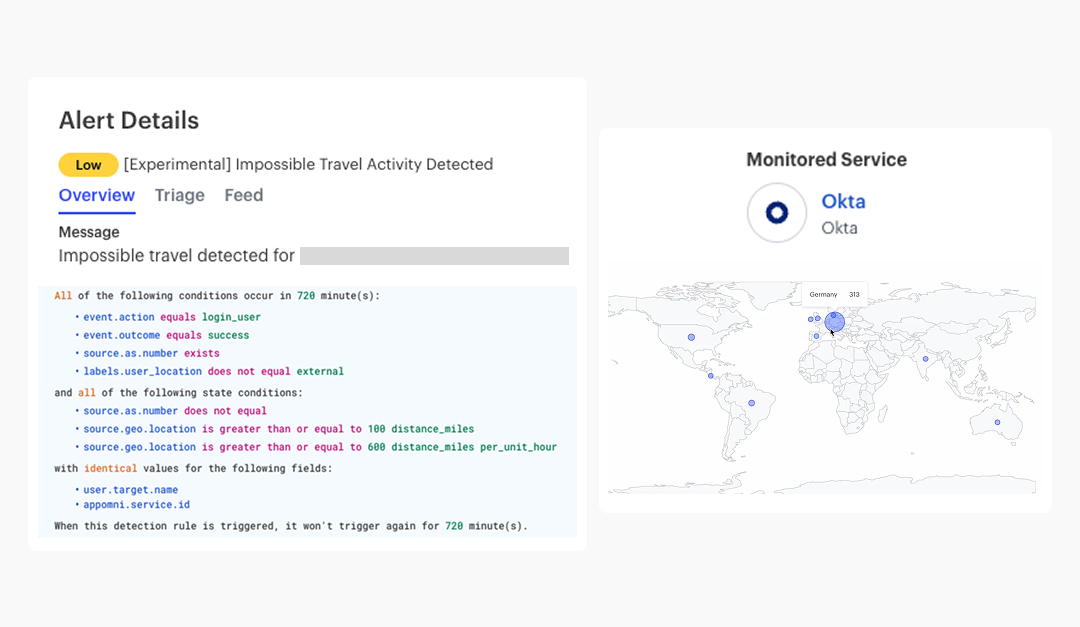
Detect Security Threats, Respond with Confidence
AppOmni provides the telemetry and tools, combined with posture and identity centric analysis to efficiently prioritize and respond to SaaS security threats.
Go Beyond Anomalies and Detect SaaS-Specific Threats
We correlate unusual activity with security settings and permissions to detect high-risk behaviors like account takeovers and privilege abuse.
Reduce False Positives and Identify Critical Threats
Our detection engine filters out noise, surfacing excessive data access, lateral movement, and misused service accounts.
Threat Intelligence Tailored to SaaS
Unlike generic tools, we detect SaaS-specific threats like OAuth token misuse and unauthorized API activity before they escalate.
Detect & Respond Faster with End-to-End Visibility
By monitoring user activity, integrations, and security settings, AppOmni surfaces critical threats like mass downloads, privilege changes, and suspicious admin actions.
Stop Privilege Escalation Fast
Watch how AppOmni detects high-risk permission changes across your SaaS apps, correlates activity to users and non-human identities, and guides a rapid response.
How our Threat Detection secures SaaS
AppOmni can now take threat detection for SaaS to another level with enhanced SaaS-Aware Identity Threat Detection and Response (SaaS ITDR). AppOmni’s SaaS-awareness enhances ITDR capabilities by prioritizing identity in SaaS security. With comprehensive lifecycle visibility into identities within the SaaS environment, including SaaS events and user behavior, we identify SaaS-specific threats arising from suspicious user activities, compromised credentials, and other vulnerabilities.
Read more about AppOmni’s ITDR Solutions
Key Features
SaaS Event Maturity Matrix (EMM) – Know What’s Logged, Avoid Blind Spots
Not all SaaS logs provide useful security insights. The Event Maturity Matrix (EMM) helps security teams understand what security events each SaaS app provides, ensuring you’re detecting threats with the most relevant and reliable data.

Related Content
-
ShinyHunters Claims Woflow Breach: What It Means for SaaS Supply Chain Security
Learn the security risks in SaaS supply chains and about ShinyHunters’ evolving extortion tactics behind the alleged Woflow breach.
-
AdExchanger Data Privacy Roundup
Costello sees a broader pattern of SaaS vendors racing to bolt AI onto everything. In that rush, security is a lower priority.
-
New phishing campaign tricks employees into bypassing Microsoft 365 MFA
Cory Michal, CSO at AppOmni, said attacks often leverage OAuth tokens and service/integration identities because they’re a blind spot for many orgs.
“I needed to get a better understanding of the overall attack surface, our portfolio of applications, and their configurations and data exposure risks.”
Wai Sheng Cheng
Information Security and Risk Manager, Spencer Fane

Spot the signs of a SaaS breach before it spreads
AppOmni Threat Detection gives you real-time insight into suspicious activity across your SaaS apps. Understand what is happening, take quick action, and stop threats before they impact your business.